ZLOADER


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
ZLOADER is a banking trojan also known as Terdot and Zbot. This malware is based on leaked code of known ZeuS malware. It uses web injects to steal user credentials and other private information from the victim. It can also steal passwords and cookies stored in the victim’s web browsers.
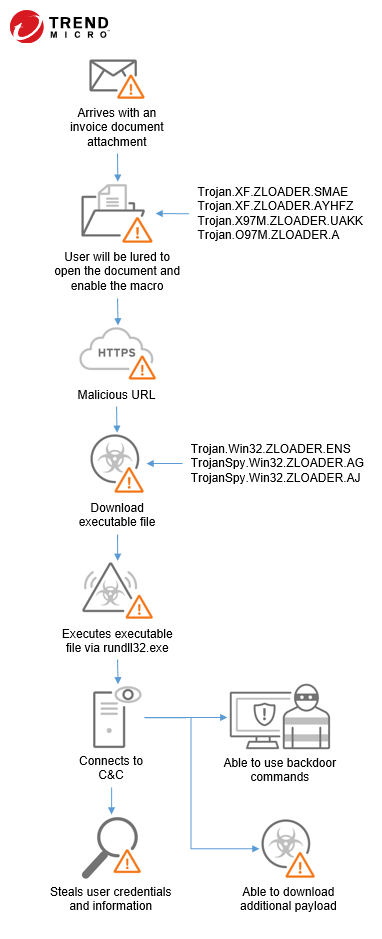
With the stolen information, ZLOADER can use the downloaded Virtual Network Computing (VNC) client to allow attackers to log into victim's system and perform illegal financial transactions from the banking user's legitimate device.
ZLOADER spreads through email campaigns with malicious attachment containing topics such as COVID-19, job offers, resumes, invoices and excel files. The attachment lures the victim to Enable Content. Once user mistakenly clicks on it, the malware is automatically downloaded.
ZLOADER avoids analysis, making its detection and reverse engineering difficult. These mechanisms include junk code, constant obfuscation, Windows API function hashing, encrypted strings, and C&C blacklisting. What is new to this malware is that the enabling of macro has a press button style - view invoice in the sheet itself. In addition, the XLM code of the current ZLOADER has a cleaner and shorter loop for decoding itself.
It is capable of the following:
- Employs anti-analysis mechanisms that includes junk code, constant obfuscation, Windows API function hashing, encrypted strings and C&C blacklisting
- Steals user credentials, financial and banking information
- Steals Outlook client credentials
- Executes backdoor commands from a remote malicious user to connect to malicious websites for sending and receiving information
- Monitors keystrokes in browser and takes screenshots
ZLOADER typically follows the infection chain depicted below: