WORM_STUXNET.A
Windows 2000, XP, Server 2003, Vista 32-bit


Threat Type: Worm
Destructiveness: Yes
Encrypted: No
In the wild: Yes
OVERVIEW
Trend Micro has flagged this threat as noteworthy due to the increased potential for damage, propagation, or both, that it possesses.
To get a one-glance comprehensive view of the behavior of this Worm, refer to the Threat Diagram shown below.
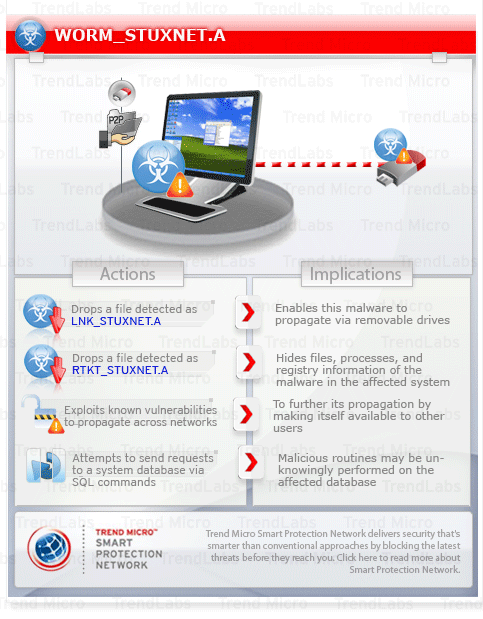
This worm arrives via removable drives.
It exploits software vulnerabilities to propagate to other computers across a network.
It hides files, processes, and/or registry entries.
TECHNICAL DETAILS
Arrival Details
This worm arrives via removable drives.
Installation
This worm drops the following component file(s):
- %System%\drivers\mrxcls.sys - detected as RTKT_STUXNET.A
- %System%\drivers\mrxnet.sys - detected as RTKT_STUXNET.A
- %System%\wbem\mof\sysnullevnt.mof
- %Windows%\inf\oem6C.PNF
- %Windows%\inf\oem7A.PNF - encrypted DLL on .stub section
- %Windows%\inf\mdmcpq3.PNF - encrypted data where URL of server is stored
- %Windows%\inf\mdmeric3.PNF
- C:\\WINDOWS\Help\winmic.fts
(Note: %System% is the Windows system folder, which is usually C:\Windows\System on Windows 98 and ME, C:\WINNT\System32 on Windows NT and 2000, or C:\Windows\System32 on Windows XP and Server 2003.. %Windows% is the Windows folder, which is usually C:\Windows or C:\WINNT.)
Propagation
This worm drops the following copy(ies) of itself in all removable drives:
- {drive letter}:\\Copy of Shortcut to.lnk
- {drive letter}:\\~WTR4132.tmp
- {drive letter}:\\~WTR4141.tmp
It exploits the following software vulnerabilities to propagate to other computers across a network:
- Microsoft Security Bulletin MS10-061
This worm exploits this vulnerability in the Windows Shell by calling the StartDocPrinter procedure in order to impersonate the Printer Spooler service to create the file WINSTA.EXE on the Windows system folder of a target machine. It also sends a second file named sysnullevnt.mof and saves it as %System%\wbem\mof. It is automatically registered to the Windows Management Instrumentation then it executes WINSTA.EXE. The said .MOF file also registers an event that deletes its duplicate in the %System%\wbem\mof\good and WINSTA.EXE once the said executable is terminated.
- Microsoft Security Bulletin MS08-067
By sending specially crafted RPC requests, this worm can send and execute a copy of itself into a vulnerable system.
(Note: %System% is the Windows system folder, which is usually C:\Windows\System on Windows 98 and ME, C:\WINNT\System32 on Windows NT and 2000, or C:\Windows\System32 on Windows XP and Server 2003.)
Backdoor Routine
This worm connects to the following URL(s) to send and receive commands from a remote malicious user:
- www.{BLOCKED}ierfutbol.com
- www.{BLOCKED}futbol.com
Rootkit Capabilities
This worm hides files, processes, and/or registry entries.
Stolen Information
This worm sends the gathered information via HTTP POST to the following URL:
- http://www.{BLOCKED}ierfutbol.com/index.php?data={data}
(Note: {data} is an encrypted hex value that contains the IP address of the machine, computer name, and domain.)
Other Details
This worm connects to the following URL(s) to check for an Internet connection:
- www.windowsupdate.com
- www.msn.com
It does the following:
- Hooks the following NTDLL.DLL APIs:
- ZwMapViewOfSection
- ZwCreateSection
- ZwOpenFile
- ZwClose
- ZwQueryAttributesFile
- ZwQuerySection
- Searches for the legitimate Siemens SCADA file, S7OTBXDX.DLL on processes and on the Windows system folder. If found, the said .DLL is renamed to S7OTBXSX.DLL. It then drops a modified .DLL to replace the original S7OTBXDX.DLL file. This modified .DLL has the same exports as file it replaces but with code modifications. It also creates the file C:\WINDOWS\Help\winmic.fts if the said routine is successful.
- Enumerates and finds processes with the following file names:
- avp.exe
- mcshield.exe
- avguard.exe
- bdagent.exe
- Umxcfg.exe
- fsdwd.exe
- rtvscan.exe
- ccSvcHst.exe
- ekrn.exe
- tmproxy.exe
- Once found, it validates if these are 32-bit file with a certain file version. If conditions are met, this worm runs any of these files and injects itself to them. If none of these processes were found, it then inject itself in LSASS.EXE. It can also find the location of a target files by searching the registry for the following values and get the stored data:
- For avp.exe:
Keys:HKEY_LOCAL_MACHINE\SOFTWARE\KasperskyLab\protected\AVP9\environment
HKEY_LOCAL_MACHINE\SOFTWARE\KasperskyLab\protected\AVP8\environment
HKEY_LOCAL_MACHINE\SOFTWARE\KasperskyLab\protected\AVP7\environment
HKEY_LOCAL_MACHINE\SOFTWARE\kasperskylab\avp7\environment
HKEY_LOCAL_MACHINE\SOFTWARE\kasperskylab\avp6\environment
Value:- ProductRoot
- For Mcshield.exe:
Key:HKEY_LOCAL_MACHINE\SOFTWARE\McAfee\VSCore
Value:
- szInstallDir32
- For tmproxy.exe
Key:HKEY_LOCAL_MACHINE\SOFTWARE\TrendMicro\NSC\TmProxy
Value:- InstallPath
- For avp.exe:
- Creates a mutex generated from its Process ID (PID) and applying the formula, {(PID xor 0x5858AA3) - (PID xor 0x0AE48481) - (PID xor 0x5858721) - (PID xor 0x49481)}, with a format string of {%08x-%08x-%08x-%08x}. For example, a PID of 0x244 produces the mutex string {058588e7-0ae486c5-05858565-000496c5}.
- Implements the Microsoft Remote Procedure Call and installs both server and client components on an infected machine. The server uses dynamic port mapping when listening to a client using the UUID 000204e1-0000-0000-c000-000000000046. The server component contains the following functions:
- Create a process that could be command shell or a file
- Create a file
- Delete a file
- Get malware version
- Read a file
- Receive module and inject it
- Send the malware file
The server uses dynamic port mapping when listening to a client. Using these functions, two affected systems can communicate with each other and update a copy of this worm if one of them is not updated.
- Exploits the Siemens SIMATIC WinCC Default Password Security Bypass Vulnerability to gain access to the back-end SQL database of a WinCC SQL server.
- Searches for the legitimate Siemens Simatic file, S7OTBXDX.DLL, in the list of running processes and in the Windows system folder. If found, it renames the said file to S7OTBXSX.DLL. It then drops a modified .DLL file to replace S7OTBXDX.DLL. This new .DLL is a modified version is used by the worm to intercept functions. It also creates the file C:\Windows\Help\winmic.fts if the said routine is successful.
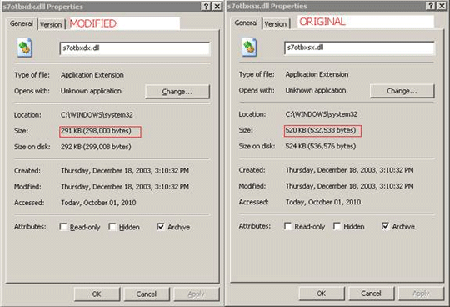
Note that the number of export functions of the modified S7OTBXDX.DLL has 109, while the original .DLL only has 80.
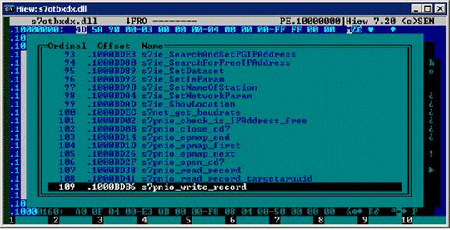
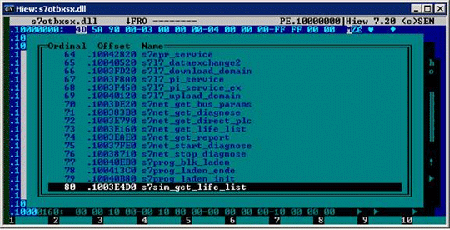
The following are the 16 export functions being intercepted by the NEWS7OTBXDX.DLL.
- s7db_open
- s7blk_write
- s7blk_findfirst
- s7blk_findnext
- s7blk_read
- s7_event
- s7ag_test
- s7ag_read_szl
- s7blk_delete
- s7ag_link_in
- s7db_close
- s7ag_bub_cycl_read_create
- s7ag_bub_read_var
- s7ag_bub_write_var
- s7ag_bub_read_var_seg
- s7ag_bub_write_var_seg
These functions are used to access, read, write, and delete code blocks on the PLC. By intercepting these functions, this worm can modify the data sent to and from the Programmable Logic Controller (PLC).
Using SQL commands, it is capable of doing the following:
- Alter configuration settings of the SQL server
- Delete the SQL file %All Users Profile%\sql%05x.dbi
- Search for \GraCS\cc_tlg7.sav by querying into the SQL database. It then extracts and saves the file as \GraCS\cc_tlg7.savx, which may contain sensitive information about the database
- Views saved projects and project information in the database.
- Creates the following files in the folder of the Simatic Projects:
- XUTILS\listen\xr000000.mdx - encrypted copy of this worm
- XUTILS\links\s7p00001.dbf
- XUTILS\listen\s7000001.mdx
It also creates the file S7HKIMDB.DLL which serves as the decryptor of XUTILS\listen\xr000000.mdx in all folders found under \hOmSave7 in the Simatic Projects folder.
- Views the database of projects and information related to these projects from the WinCC server.
- Alters configuration settings and can access or delete the file %All Users Profile%\sql%05x.dbi.
SOLUTION
Step 1
For Windows XP and Windows Server 2003 users, before doing any scans, please make sure you disable System Restore to allow full scanning of your computer.
Step 3
Identify and delete files detected as WORM_STUXNET.A using the Recovery Console
Step 4
Delete this registry key
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\
- MRxCls
- MRxCls
- In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\
- MRxNet
- MRxNet
Step 5
Search and delete these files
- %Windows%\inf\oem6C.PNF
- %Windows%\inf\oem7A.PNF
- %Windows%\inf\mdmcpq3.PNF
- %Windows%\inf\mdmeric3.PNF
- C:\WINDOWS\Help\winmic.fts
- %Simatic Project folder%\XUTILS\listen\xr000000.mdx
- %Simatic Project folder%\XUTILS\links\s7p00001.dbf
- %Simatic Project folder%\XUTILS\listen\s7000001.mdx
- %Simatic Project folder%\hOmSave7\s7hkimdb.dll
Step 6
Restart in normal mode and scan your computer with your Trend Micro product for files detected as WORM_STUXNET.A. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Step 7
Download and apply this security patch Refrain from using these products until the appropriate patches have been installed. Trend Micro advises users to download critical patches upon release by vendors.
- Microsoft Security Bulletin MS10-046
- Microsoft Security Bulletin MS10-061
- Microsoft Security Bulletin MS08-067
Note: To identify STUXNET-infected systems within a network, administrators can use Trend Micro's special STUXNET Scanner Tool. For more details, download and extract the package and refer to the tool's incorporated text file.
Did this description help? Tell us how we did.


