WORM_LAMIN.AC
W32.IRCBot, Worm:Win32/Lamin.A
Windows 2000, Windows XP, Windows Server 2003


Threat Type: Worm
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
Trend Micro has received multiple infections similar to this threat from multiple, independent sources, including customer reports and internal sources. These indicate that this threat poses a high risk to users due to the increased possibility of infection.
To get a one-glance comprehensive view of the behavior of this Worm, refer to the Threat Diagram shown below.
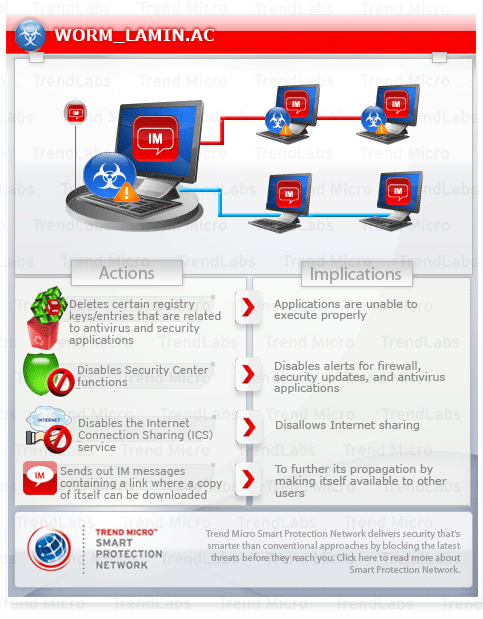
This worm opens Microsoft Word in order to hide its malicious routines from the user. It creates registry entries to prevent execution of specific applications, as well as the various functions of the Windows Security Center. It also modifies registry entries to lower the security settings of the system, as well as delete other entries to disable Safe Mode.
For its backdoor routine, this worm is capable of joining a predetermined Internet Relay chat (IRC) channel where it can receive commands from a malicious user.
This worm adds registry entries to enable its automatic execution at every system startup.
It modifies certain registry entries to disable Security Center functions. Doing this allows this malware to execute its routines without being detected.
This worm modifies certain registry entries to disable Security Center functions. Doing this allows this malware to execute its routines without being detected.
TECHNICAL DETAILS
Arrival Details
This worm may be downloaded from the following remote sites:
- http://bukuger{BLOCKED}.hared.com
Installation
This worm drops the following component file(s):
- %Program Files%\Microsoft Office\OFFICE11\control.ini - IRC configuration file
- %Program Files%\Microsoft Office\OFFICE11\Drvics32.dll - network configuration file
- %Program Files%\Microsoft Office\OFFICE11\hjwgsd.dll - contains the list of IM messages that it will send
- %Program Files%\Microsoft Office\OFFICE11\jwiegh.dll - contains the list of MIRC nicknames it will use
- %Program Files%\Microsoft Office\OFFICE11\PUB60SP.mrc - IRC script component
- %Program Files%\Microsoft Office\OFFICE11\remote.ini - encrypted file
- %Program Files%\Microsoft Office\OFFICE11\ruimsbbe.dll - encrypted file
- %Program Files%\Microsoft Office\OFFICE11\yofc.dll - encrypted file
- %Program Files%\Microsoft Office\OFFICE11\smss.exe - encrypted file
(Note: %Program Files% is the default Program Files folder, usually C:\Program Files in Windows 2000, Server 2003, and XP (32-bit), Vista (32-bit), and 7 (32-bit), or C:\Program Files (x86) in Windows XP (64-bit), Vista (64-bit), and 7 (64-bit).)
It drops the following copies of itself into the affected system:
- %Program Files%\Microsoft Office\OFFICE11\services.exe
- %Program Files%\Microsoft Office\OFFICE11\WINWORD.EXE
- %User Startup%\Adobe Gamma Loader.com
Autostart Technique
This worm adds the following registry entries to enable its automatic execution at every system startup:
HKEY_CURRENT_USER\Software\Microsoft\
Windows NT\CurrentVersion\Winlogon
Shell = %Program Files%\Microsoft Office\OFFICE11\WINWORD.EXE
Other System Modifications
This worm adds the following registry entries as part of its installation routine:
HKEY_CLASSES_ROOT\exefile
NeverShowExt =
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center
AntiVirusDisableNotify = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center
AntiVirusOverride = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center
FirewallDisableNotify = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center
FirewallOverride = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center
FirstRunDisabled = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center
UpdatesDisableNotify = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center
UacDisableNotify = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center\Svc
AntiVirusDisableNotify = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center\Svc
AntiVirusOverride = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center\Svc
FirewallDisableNotify = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center\Svc
FirewallOverride = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center\Svc
FirstRunDisabled = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center\Svc
UpdatesDisableNotify = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center\Svc
UacDisableNotify = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Tracing\FWCFG
EnableFileTracing = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Tracing\FWCFG
EnableConsoleTracing = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Tracing\FWCFG
FileTracingMask = ffff0000
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Tracing\FWCFG
ConsoleTracingMask = ffff0000
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Tracing\FWCFG
MaxFileSize = 00100000
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Tracing\FWCFG
FileDirectory = %windir%\tracing
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\policies\
system
EnableLUA = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\WinDefend
Start = 4
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\WinDefend
Type = 4
It modifies the following registry entries to disable Security Center functions:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\SharedAccess
Type = 4
(Note: The default value data of the said registry entry is 20.)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\SharedAccess
Start = 4
(Note: The default value data of the said registry entry is 2.)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\wscsvc
Type = 4
(Note: The default value data of the said registry entry is 20.)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\wscsvc
Start = 4
(Note: The default value data of the said registry entry is 2.)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\wuauserv
Type = 4
(Note: The default value data of the said registry entry is 20.)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\wuauserv
Start = 4
(Note: The default value data of the said registry entry is 2.)
It modifies the following registry entries to hide files with Hidden attributes:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Explorer\
Advanced
SuperHidden = 0
(Note: The default value data of the said registry entry is 1.)
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Explorer\
Advanced
ShowSuperHidden = 0
(Note: The default value data of the said registry entry is 1.)
It deletes the following registry keys:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Control\SafeBoot
Propagation
This worm sends copies of itself to target recipients using the following instant-messaging (IM) applications:
- GoogleTalk
- Digsby
Other Details
This worm does the following:
- Opens Microsoft Word in order to hide its malicious routines from the user.
- Creates the following registry entries, to prevent execution of specific applications:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\{Application name}
Debugger = "cmd.exe /c del"
- Acha.exe
- AmyMastura.exe
- BabyRina.exe
- cscript.exe
- csrsz.exe
- lsasc.exe
- registry.exe
- SMSSS.exe
- wscript.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\{Application name}
- Disables the following services:
- Windows Firewall/Internet Connection Sharing (ICS)
- Automatic Updates
- Security CenterSystem Firewall
- Pings the following sites using the following commands:
- ping www.tourism.gov.my -t -l 3000
- ping www.miti.gov.my -t -l 3000
- ping www.putera.com -t -l 3000
- The sent spam messages are predetermined, which is listed in HJWGSD.DLLl, and contains the link http://bukuger{BLOCKED}.hared.com. Copies of the malware maybe downloaded from this site, which is currently inaccessible.
- For its backdoor routine, it is capable of joining a predetermined IRC channels where it can receive commands from a malicious user.
- Adds the said registry entries (seen in Other System Modifications) to lower security settings of the system.
- Deletes the said registry keys to disable Safe Boot.
- Modifies registry entries to lower security settings in the system.
SOLUTION
Step 1
Before doing any scans, Windows XP, Windows Vista, and Windows 7 users must disable System Restore to allow full scanning of their computers.
Step 2
Identify and terminate files detected as WORM_LAMIN.AC
- Windows Task Manager may not display all running processes. In this case, please use a third-party process viewer, preferably Process Explorer, to terminate the malware/grayware/spyware file. You may download the said tool here.
- If the detected file is displayed in either Windows Task Manager or Process Explorer but you cannot delete it, restart your computer in safe mode. To do this, refer to this link for the complete steps.
- If the detected file is not displayed in either Windows Task Manager or Process Explorer, continue doing the next steps.
Step 3
Enable Registry Editor
Step 4
Delete this registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
- Shell = %Program Files%\Microsoft Office\OFFICE11\WINWORD.EXE
- Shell = %Program Files%\Microsoft Office\OFFICE11\WINWORD.EXE
- In HKEY_CLASSES_ROOT\exefile
- NeverShowExt =
- NeverShowExt =
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system
- EnableLUA = 0
- EnableLUA = 0
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\{Application name}
- Debugger = cmd.exe /c del
- Debugger = cmd.exe /c del
Step 5
Delete this registry key
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\
- Svc
- Svc
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\
- FWCFG
- FWCFG
- In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\
- WinDefend
- WinDefend
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
- Security Center
- Security Center
Step 6
Restore this modified registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
- From: SuperHidden = 0
To: SuperHidden = 1
- From: SuperHidden = 0
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
- From: ShowSuperHidden = 0
To: ShowSuperHidden = 1
- From: ShowSuperHidden = 0
- In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess
- From: Type = 4
To: Type = 20
- From: Type = 4
- In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess
- From: Start = 4
To: Start = 2
- From: Start = 4
- In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\wscsvc
- From: Type = 4
To: Type = 20
- From: Type = 4
- In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\wscsvc
- From: Start = 4
To: Start = 2
- From: Start = 4
- In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\wuauserv
- From: Type = 4
To: Type = 20
- From: Type = 4
- In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\wuauserv
- From: Start = 4
To: Start = 2
- From: Start = 4
Step 7
Search and delete this file
- %Program Files%\Microsoft Office\OFFICE11\control.ini
- %Program Files%\Microsoft Office\OFFICE11\Drvics32.dll
- %Program Files%\Microsoft Office\OFFICE11\hjwgsd.dll
- %Program Files%\Microsoft Office\OFFICE11\jwiegh.dll
- %Program Files%\Microsoft Office\OFFICE11\PUB60SP.mrc
- %Program Files%\Microsoft Office\OFFICE11\remote.ini
- %Program Files%\Microsoft Office\OFFICE11\ruimsbbe.dll
- %Program Files%\Microsoft Office\OFFICE11\yofc.dll
- %Program Files%\Microsoft Office\OFFICE11\smss.exe
Step 8
Scan your computer with your Trend Micro product to delete files detected as WORM_LAMIN.AC. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.



