PUA_SYSTEMCARE.GB
Hoax.Win32.Agent.zsq (Kaspersky), Riskware/Agent (Fortinet)
Windows


Threat Type: Potentially Unwanted Application
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This Potentially Unwanted Application arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites. It may be manually installed by a user.
TECHNICAL DETAILS
Arrival Details
This Potentially Unwanted Application arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It may be manually installed by a user.
Installation
This Potentially Unwanted Application adds the following folders:
- %Program Files%\Power -System- Care for {System Name}
- %Program Files%\Power -System- Care for {System Name}\x64
- %Program Files%\Power -System- Care for {System Name}\x86
- %All Users Profile%\Power -System- Care for {System Name}
- %All Users Profile%\Microsoft\Windows\Start Menu\Programs\Power -System- Care for {System Name}
- %Application Data%\Power -System- Care For {System Name}
- %User Temp%\is-{random}.tmp\_isetup
- %User Temp%\is-{random}.tmp
(Note: %Program Files% is the default Program Files folder, usually C:\Program Files in Windows 2000, Server 2003, and XP (32-bit), Vista (32-bit), 7 (32-bit), and 8 (32-bit), or C:\Program Files (x86) in Windows XP (64-bit), Vista (64-bit), 7 (64-bit), and 8 (64-bit).. %All Users Profile% is the common user's profile folder, which is usually C:\Documents and Settings\All Users on Windows 2000, XP, and Server 2003, or C:\ProgramData on Windows Vista, 7, and 8. . %Application Data% is the current user's Application Data folder, which is usually C:\Documents and Settings\{user name}\Application Data on Windows 2000, XP, and Server 2003, or C:\Users\{user name}\AppData\Roaming on Windows Vista, 7, and 8.. %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000, XP, and Server 2003, or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, and 8.)
It drops the following files:
- %User Temp%\is-{random}.tmp\{original file name}.tmp
- %User Temp%\is-{random}.tmp\_isetup\_shfoldr.dll
- %User Temp%\is-{random}.tmp\_isetup\_iscrypt.dll
- %User Temp%\is-{random}.tmp\setup_en.bmp
- %Program Files%\Power -System- Care for {System Name}\iytr.exe
- %Program Files%\Power -System- Care for {System Name}\NAudio.dll
- %Program Files%\Power -System- Care for {System Name}\Newtonsoft.Json.dll
- %Program Files%\Power -System- Care for {System Name}\System.Data.SQLite.DLL
- %Program Files%\Power -System- Care for {System Name}\x64\SQLite.Interop.dll
- %Program Files%\Power -System- Care for {System Name}\x86\SQLite.Interop.dll
- %Program Files%\Power -System- Care for {System Name}\HtmlRenderer.dll
- %Program Files%\Power -System- Care for {System Name}\PaddleCheckoutSDK.dll
- %Program Files%\Power -System- Care for {System Name}\gmtrs.dll
- %Program Files%\Power -System- Care for {System Name}\HtmlRenderer.WinForms.dll
- %Program Files%\Power -System- Care for {System Name}\Interop.IWshRuntimeLibrary.dll
- %Program Files%\Power -System- Care for {System Name}\Interop.SHDocVw.dll
- %Program Files%\Power -System- Care for {System Name}\Microsoft.Win32.TaskScheduler.dll
- %Program Files%\Power -System- Care for {System Name}\TAFactory.IconPack.dll
- %Program Files%\Power -System- Care for {System Name}\unins000.dat
- %Program Files%\Power -System- Care for {System Name}\unins000.exe
- %Program Files%\Power -System- Care for {System Name}\iytr.exe.config
- %Program Files%\Power -System- Care for {System Name}\application.ico
- %All Users Profile%\Power -System- Care for {System Name}\mdb.db
- %All Users Profile%\Power -System- Care for {System Name}\pcspstartrepair_en.mp3
- %Program Files%\Power -System- Care for {System Name}\langs.db
- %Program Files%\Power -System- Care for {System Name}\english_iss.ini
- %Program Files%\Power -System- Care for {System Name}\finish_iss.ini
- %Program Files%\Power -System- Care for {System Name}\French_iss.ini
- %Program Files%\Power -System- Care for {System Name}\german_iss.ini
- %Program Files%\Power -System- Care for {System Name}\italian_iss.ini
- %Program Files%\Power -System- Care for {System Name}\japanese_iss.ini
- %Program Files%\Power -System- Care for {System Name}\norwegian_iss.ini
- %Program Files%\Power -System- Care for {System Name}\portuguese_iss.ini
- %Program Files%\Power -System- Care for {System Name}\russian_iss.ini
- %Program Files%\Power -System- Care for {System Name}\spanish_iss.ini
- %Program Files%\Power -System- Care for {System Name}\swedish_iss.ini
- %Program Files%\Power -System- Care for {System Name}\danish_iss.ini
- %Program Files%\Power -System- Care for {System Name}\Dutch_iss.ini
- %All Users Profile%\Microsoft\Windows\Start Menu\Programs\Power -System- Care for {System Name}\Power -System- Care.lnk
- %All Users Profile%\Microsoft\Windows\Start Menu\Programs\Power -System- Care for {System Name}\Buy Power -System- Care.lnk
- %All Users Profile%\Microsoft\Windows\Start Menu\Programs\Power -System- Care for {System Name}\Uninstall Power -System- Care.lnk
- %System Root%\Users\Public\Desktop\Power -System- Care.lnk
- %Program Files%\Power -System- Care for {System Name}\unins000.msg
- %Application Data%\Power -System- Care For {System Name}\Errorlog.txt
- %Application Data%\Power -System- Care For {System Name}\exlist.bin
- %Application Data%\Power -System- Care For {System Name}\notifier.xml
- %Application Data%\Power -System- Care For {System Name}\res.xml
- %System%\Tasks\Power -System- Care_Logon
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000, XP, and Server 2003, or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, and 8.. %Program Files% is the default Program Files folder, usually C:\Program Files in Windows 2000, Server 2003, and XP (32-bit), Vista (32-bit), 7 (32-bit), and 8 (32-bit), or C:\Program Files (x86) in Windows XP (64-bit), Vista (64-bit), 7 (64-bit), and 8 (64-bit).. %All Users Profile% is the common user's profile folder, which is usually C:\Documents and Settings\All Users on Windows 2000, XP, and Server 2003, or C:\ProgramData on Windows Vista, 7, and 8. . %System Root% is the Windows root folder, where it usually is C:\ on all Windows operating system versions.. %Application Data% is the current user's Application Data folder, which is usually C:\Documents and Settings\{user name}\Application Data on Windows 2000, XP, and Server 2003, or C:\Users\{user name}\AppData\Roaming on Windows Vista, 7, and 8.. %System% is the Windows system folder, where it usually is C:\Windows\System32 on all Windows operating system versions.)
Autostart Technique
The scheduled task executes the malware every:
- user logon
Other System Modifications
This Potentially Unwanted Application adds the following registry keys:
HKEY_LOCAL_MACHINE\Software\Power -System- Care For {System Name}
HKEY_CURRENT_USER\Software\Power -System- Care for {System Name}
HKEY_CURRENT_USER\Software\Power -System- Care for {System Name}\
2.0.0.0
HKEY_LOCAL_MACHINE\Software\scd-pr
HKEY_LOCAL_MACHINE\Software\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
HKEY_LOCAL_MACHINE\Software\UG93ZXIgLVN5c3RlbS0gQ2FyZQ==
HKEY_LOCAL_MACHINE\Software\UG93ZXIgLVN5c3RlbS0gQ2FyZQ==\
ACT
HKEY_LOCAL_MACHINE\Software\ZHJpdmVyZGV0YWlscy5jb20=
HKEY_LOCAL_MACHINE\Software\ZHJpdmVyZGV0YWlscy5jb20=\
RHJpdmVyIFVwZGF0ZXI=
HKEY_LOCAL_MACHINE\Software\ZHJpdmVyZGV0YWlscy5jb20=\
RHJpdmVyIFVwZGF0ZXI=\ACT
It adds the following registry entries as part of its installation routine:
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO = "(855)-332-0124"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
ISTELNO = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
apst = "0"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
isshowng = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
issilent = "0"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
affired = "0"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
showwfo = "0"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
ovoffdis = "0"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
playsound = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
wfoset = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
country = ""
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
ipaddrurl = "http://www.alfactiv.com/getip/"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
prereg = "0"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
showtn = "0"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
cbkpoff = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
cta = "0"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
showunins = "0"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
delaytime = "0"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
isiunidu = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
isavst = "0"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
isprmjsn = "0"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
runcam = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
runsrc = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
runpixel = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
stdismax = "4294967295"
HKEY_CURRENT_USER\Software\Power -System- Care For {System Name}
utm_medium = ""
HKEY_CURRENT_USER\Software\Power -System- Care For {System Name}
affiliateid = ""
HKEY_LOCAL_MACHINE\SOFTWARE\scd-pr
utm_source = "msmsite"
HKEY_LOCAL_MACHINE\SOFTWARE\scd-pr
utm_campaign = "msmsite"
HKEY_LOCAL_MACHINE\SOFTWARE\scd-pr
utm_medium = ""
HKEY_LOCAL_MACHINE\SOFTWARE\scd-pr
affiliateid = ""
HKEY_LOCAL_MACHINE\SOFTWARE\scd-pr
pxl = "msmsite"
HKEY_LOCAL_MACHINE\SOFTWARE\scd-pr
x-at = ""
HKEY_LOCAL_MACHINE\SOFTWARE\scd-pr
x-context = ""
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_us = "(855)-332-0124"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_uk = "0800-031-5066"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_gb = "0800-031-5066"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_au = "(61)280-733403"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_fr = "05 82 84 04 06"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_de = "0800 1822 974"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_at = "+43 (0)720 902 309"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_ch = "+41 (0)44 508 70 37"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_lu = "0800 1822 974"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_no = "+47 21 95 01 97"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_dk = "+45 78 73 09 26"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_nl = "+31-08-58882839"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_be = "+32-28085306"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_se = "+46-08124-10298"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_ja = ""
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_br = "+55 21 2391 4319"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_it = "+39 069 4802886"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_es = "+34 951 203 537"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_ar = "+54 11 5236 0324"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_fi = "+358 (0)9 4270 4911"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
TELNO_pt = "+351 70 750 2094"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
pdtm = "30"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
PurchaseURL = "https://store.mypccareutils.com/psc/price?"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
RenewURL = "https://store.mypccareutils.com/psc/renewal?"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
WebURL = "https://www.mypccareutils.com/"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
EmailURL = ""
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
afterInstallUrl = "http://ins1.alfactiv.com/install/psc/?"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
supporturl = "http://www.mypccareutils.com/help/"
HKEY_CURRENT_USER\Software\Power -System- Care For {System Name}\
2.0.0.0
Installstring = "%Program Files%\Power -System- Care for {System Name}"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
Installstring = "%Program Files%\Power -System- Care for {System Name}"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
Inno Setup: Setup Version = "5.5.8 (u)"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
Inno Setup: App Path = "%Program Files%\Power -System- Care for {System Name}"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
InstallLocation = "%Program Files%\Power -System- Care for {System Name}\"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
Inno Setup: Icon Group = "Power -System- Care for {System Name}"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
Inno Setup: User = "{User Name}"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
Inno Setup: Language = "en"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
DisplayName = "Power -System- Care"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
DisplayIcon = "%Program Files%\Power -System- Care for {System Name}\iytr.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
UninstallString = ""%Program Files%\Power -System- Care for {System Name}\unins000.exe""
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
QuietUninstallString = ""%Program Files%\Power -System- Care for {System Name}\unins000.exe" /SILENT"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
DisplayVersion = "2.0.0.0"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
NoModify = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
NoRepair = "1"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
InstallDate = "20180924"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
MajorVersion = "2"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
MinorVersion = "0"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
{42BED48C-0BC1-46E5-BA9E-36D27915DDCF}_is1
EstimatedSize = "12861"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
paramurl = "http://trkr.alfactiv.com/ipfiles/"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
plurl = "http://pp.alfactiv.com/ProductPrice.svc/"
HKEY_LOCAL_MACHINE\SOFTWARE\Power -System- Care For {System Name}
buybowinapp = "http://store.mypccareutils.com/psc/plan? "
Download Routine
This Potentially Unwanted Application saves the files it downloads using the following names:
- %System%\view.txt
- %Application Data%\Power -System- Care For {System Name}\pplan.xml
- %Application Data%\Power -System- Care For {System Name}\update.xml
(Note: %System% is the Windows system folder, where it usually is C:\Windows\System32 on all Windows operating system versions.. %Application Data% is the current user's Application Data folder, which is usually C:\Documents and Settings\{user name}\Application Data on Windows 2000, XP, and Server 2003, or C:\Users\{user name}\AppData\Roaming on Windows Vista, 7, and 8.)
Other Details
This Potentially Unwanted Application connects to the following URL(s) to get the affected system's IP address:
- http://www.alfactiv.com/getip/
- http://trkr.alfactiv.com/ipfiles/{public ip address of affected machine}.txt
It does the following:
- It connects to the following URL(s) for tracking offers or updating its configuration:
- http://trk.{BLOCKED}track.com/trackerwcfsrv/tracker.svc/trackOffersView/?q=pxl%3DPCS2064_PCS2020_PCS1056%26utm_source%3Dpcspudubnd%26utm_medium%3Dpcspudubnd%26utm_campaign%3Dpcspudubnd%26x-count%3D1%26
- http://update.{BLOCKED}reutils.com/psc/psc_upgrades/pplan.xml
- http://pp.{BLOCKED}iv.com/ProductPrice.svc/PaddlePlanPrice/{Country Code}/75
- http://update.{BLOCKED}reutils.com/psc/psc_upgrades/update.xml
- It connects to the following URL(s) to report new installation:
- http://ins1.{BLOCKED}iv.com/install/psc/?utm_source=cccleanersite&utm_campaign=cccleanersite&utm_medium=&utm_pubid=&pxl=cccleanersite&x-context=&x-at=&x-uid={UID}&sysname=&syslogo=&x-dm=aHR0cHM6Ly93d3cubXlwY2NhcmV1dGlscy5jb20v&x-ccode={Country Code}&x-ip={public ip address of affected machine}&x-fetch=0
- This PUA displays the following scanning window:
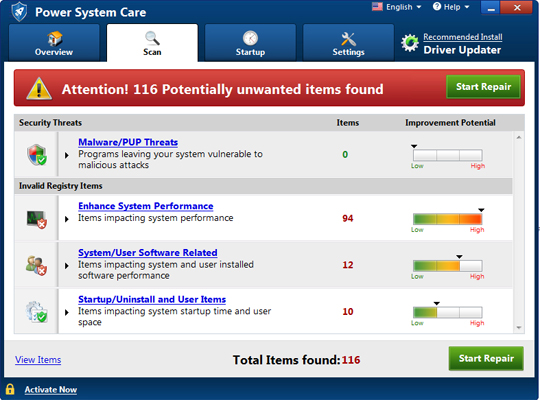
- Clicking "Start Repair" will redirect the user to the following website:
- https://store.{BLOCKED}reutils.com/psc/price?utm_source=cccleanersite&utm_campaign=cccleanersite&utm_medium=&utm_pubid=&pxl=cccleanersite&x-context=&x-at=&x-uid={uid}&sysname=&syslogo=&x-dm=aHR0cHM6Ly93d3cubXlwY2NhcmV1dGlscy5jb20v&x-ccode={country code}&x-ip={public IP addresss}&x-fetch=0&totalcount={value}®count={value}&seccount={value}&os={OS of affected machine}&ram={amount of memory installed in affected machine}&model={system model of affected machine}&proc={processor of affected machine}
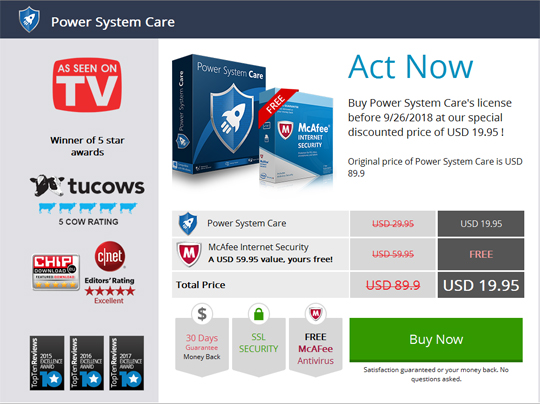
This requires the user to buy the full version to use the product
- Closing the program displays the following window to persuade the user into buying the full product:
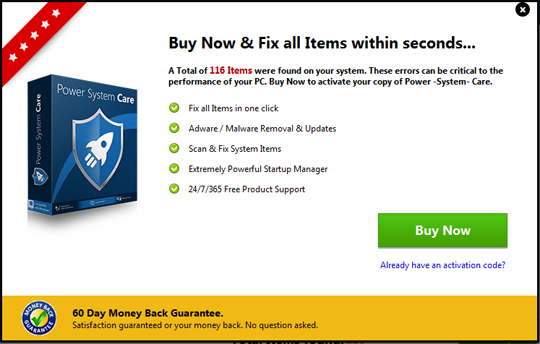
- It retrieves the affected machine's country code by accessing the following URL:
- http://cc.{BLOCKED}iv.com/productprice.svc/getcountrycode
It adds the following scheduled tasks:
- Power -System- Care_Logon
SOLUTION
Step 1
Before doing any scans, Windows XP, Windows Vista, and Windows 7 users must disable System Restore to allow full scanning of their computers.
Step 2
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 3
Identify and terminate files detected as PUA_SYSTEMCARE.GB
- Windows Task Manager may not display all running processes. In this case, please use a third-party process viewer, preferably Process Explorer, to terminate the malware/grayware/spyware file. You may download the said tool here.
- If the detected file is displayed in either Windows Task Manager or Process Explorer but you cannot delete it, restart your computer in safe mode. To do this, refer to this link for the complete steps.
- If the detected file is not displayed in either Windows Task Manager or Process Explorer, continue doing the next steps.
Step 4
Remove PUA_SYSTEMCARE.GB by using its own Uninstall option
Step 5
Scan your computer with your Trend Micro product to delete files detected as PUA_SYSTEMCARE.GB. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check the following Trend Micro Support pages for more information:
Did this description help? Tell us how we did.

