NEGASTEAL
Windows


Threat Type: Trojan Spy
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
NEGASTEAL, also known as AGENT TESLA, is an information stealer written in Microsoft’s .NET language. It has keylogging and remote access Trojan (RAT) capabilities. It was discovered in 2014 and has been used in various malicious campaigns ever since. It has been known to send stolen information either through web panel, file transfer protocol (FTP) or simple mail transfer protocol (SMTP). A previous version of the malware was compiled in AutoIT to obfuscate malware binary and evade security detection, and another version is capable of spreading the malware through the use of removable drives.
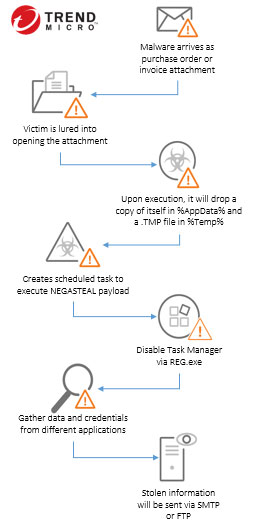
It was observed to be delivered via spam campaign that uses social engineering lures. Some of these campaigns use Covid-19, while others contain product inquiry or purchase order inquiry sent to marketing officers of different companies. The malicious spam has .iso, .ace or .gz attachments, which are archived files that contain the malware. This trojan spyware sends the data it gathers from its victims to the email address of the malware author via Simple Mail Transfer Protocol (SMTP).
A variant observed in 2020, aside from able to steal machine information, data in browsers, email client or FTP credentials and user credentials, has a new module for getting the WiFi profile or credential. The stolen information will be sent via email or FTP. With this new feature, cybercriminals have the ability to spread or create an entry vector through the victim's network.
It gathers the following data and sends it to its servers:
- Computer information (OS version, computer name, OS version platform, IP address, user name, physical memory size)
- Hardware information (processor name, video card name, video card memory)
- Browser's user names and passwords
- File Transfer Protocol (FTP) clients or file manager software stored account information
- Email credentials of popular mail clients
It is capable of the following:
- Information Theft
- Backdoor commands
NEGASTEAL typically follows the infection chain below: