ANDROIDOS_SMSZOMBIE.A
Information Stealer, Premium Service Abuser
Android OS


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
This Trojan forwards any received SMS to a specific number and sends SMS by keywords. It is controlled remotely via SMS to send SMS or write SMS to Inbox.
It leverages a vulnerability in the China Mobile SMS Payment process to steal banking credentials and money transfer receipt information as well as do unauthorized payments without the user's consent.
This Trojan may be downloaded from app stores/third party app stores.
TECHNICAL DETAILS
Arrival Details
This Trojan may be downloaded from app stores/third party app stores.
NOTES:
This Trojan forwards any received SMS to a specific number and sends SMS by keywords. It is controlled remotely via SMS to send SMS or write SMS to Inbox.
It leverages a vulnerability in the China Mobile SMS Payment process to steal banking credentials and money transfer receipt information as well as do unauthorized payments without the user's consent.
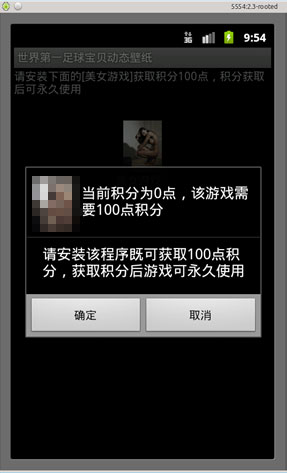
The Trojan pretends to be a live wallpaper. It also promotes a fake game that supposedly gives a reward of 100 points to the user.

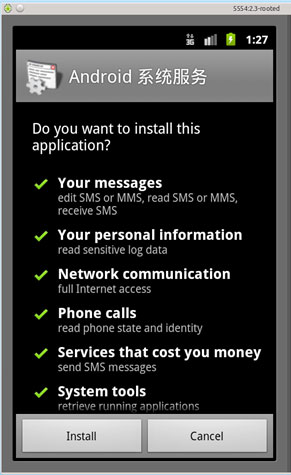
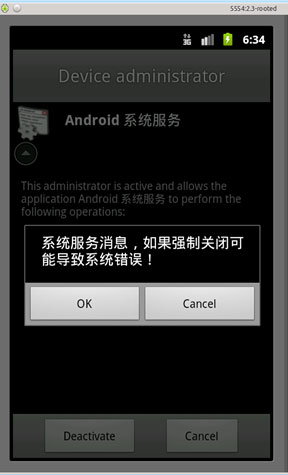
After installation, it then asks the user to activate it as Device Administrator by tricking them that it can save power. If the users click the ‘cancel’ button or click the ‘return’ button, the screen appears again. Once the users activated the Trojan as device administrator, it guides the user to desktop screen.
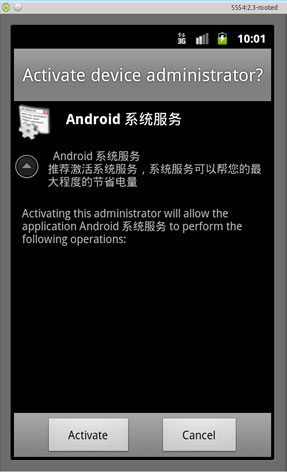
This Trojan is hard to remove on the infected device because once the users go to Manage applications to uninstall it, the malware goes back to the desktop screen. In addition, since the malware is activated as a device administrator, uninstalling the application won’t work.
It also informs users that once they deactivate it, it results to an error in Android OS. If the user chooses to deactivate it, the Trojan displays prompt messages to the users to activate it.
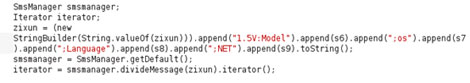
- App version
- Device information (model, OS, language)
It forwards SMS to 13093632006.
It drops SMS possibly to prevent users from receiving any messages.
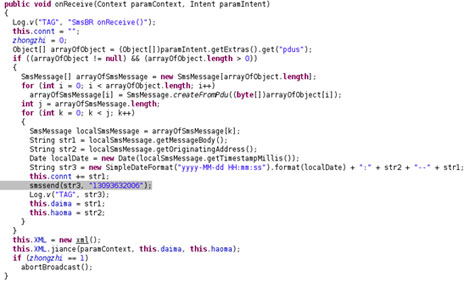
It performs the following routines:
- Send SMS
- Updates configuration
- Writes SMS to Inbox
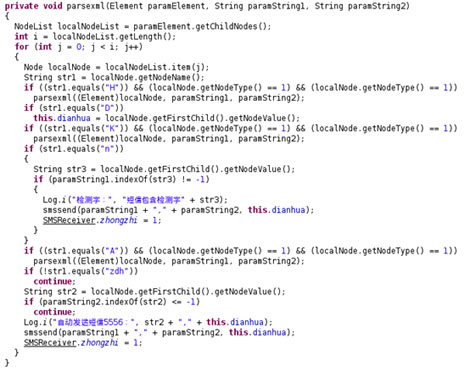

Here’s a list of SMS instructions in XML format:
| TAG | Description |
| S | change the currently configuration |
| J | write the currently to phone.xml |
| M | send SMS with value specified by tags con and rep |
| con | set SMS content |
| rep | set SMS number |
| E | write a SMS to inbox with value specified by xgh and xgnr |
| xgh | set sms number |
| xgnr | set sms content |
For example, if the attacker wants to send a SMS from the infected device to China Mobile, the cybercriminals can send the following content to the device:
11 10086
Configurations are in XML format and the default control number is “13093632006.” The default content keywords are 转,卡号,姓名,行,元汇款,hello and default number keyword is 10.
| TAG | Description |
| D | control number |
| n | keyword in SMS content, if it contains the keyword, this Trojan drops the message |
| zdh | keyword in number, if an SMS is from this number, the message will be dropped and not received by the user. |
SOLUTION
Step 1
Scan your computer with your Trend Micro product to delete files detected as ANDROIDOS_SMSZOMBIE.A. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Step 2
Remove unwanted apps on your Android mobile device
Did this description help? Tell us how we did.


