TrojanSpy.MacOS.XLOADER.A
OSX/XLoader.A!tr (FORTINET)
OSX


Threat Type: Trojan Spy
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
This Trojan Spy arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
TECHNICAL DETAILS
Arrival Details
This Trojan Spy arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Trojan Spy drops the following files:
- /Users/user/Library/LaunchAgents/{random}.plist
It drops and executes the following files:
- ~/.{random1}/{random2}.app/Contents/MacOS/{random2} (copy of itself)
- ~/.{random1}/{random2}.app/Contents/Info.plist
Other Details
This Trojan Spy connects to the following possibly malicious URL:
- www.{BLOCKED}c.com
- www.{BLOCKED}sin.com
- www.{BLOCKED}corral.com
- www.{BLOCKED}awgleads.com
- www.{BLOCKED}byfluff.com
- www.{BLOCKED}s.net
- www.{BLOCKED}cobueno.guru
- www.{BLOCKED}hyourhomes.com
- www.{BLOCKED}leco.com
- www.{BLOCKED}tos.info
- www.{BLOCKED}ricks.com
- www.{BLOCKED}freight.com
- www.{BLOCKED}ellsnv.com
- www.{BLOCKED}shaker.com
- www.{BLOCKED}z6ucg.net
- www.{BLOCKED}ssmywaynow.com
It does the following:
- When the sample is executed, it requires user’s password to access the confidential information stored in Chrome Safe Storage found in keychain.
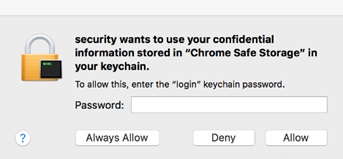
- It will create a hidden directory in the user’s home directory with an app bundle
- ~/.{random1}/{random2}.app/Contents/MacOS
- Uses ptrace implementing PT_DENY_ATTACH flag (0x1f) to avoid being debugged
- Attempts to steal Chrome browser login information by accessing keychain using the command:
- security find-generic-password -wa 'Chrome'
It does not proceed to its malicious routine if it detects that it is being debugged.
SOLUTION
Scan your computer with your Trend Micro product to delete files detected as TrojanSpy.MacOS.XLOADER.A. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check the following Trend Micro Support pages for more information:
Did this description help? Tell us how we did.


