Trojan.Win32.HUMBLE.A
Trojan.Win32.Agentb.khme (KASPERSKY)
Windows


Threat Type: Trojan
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
TECHNICAL DETAILS
Arrival Details
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Other Details
This Trojan does the following:
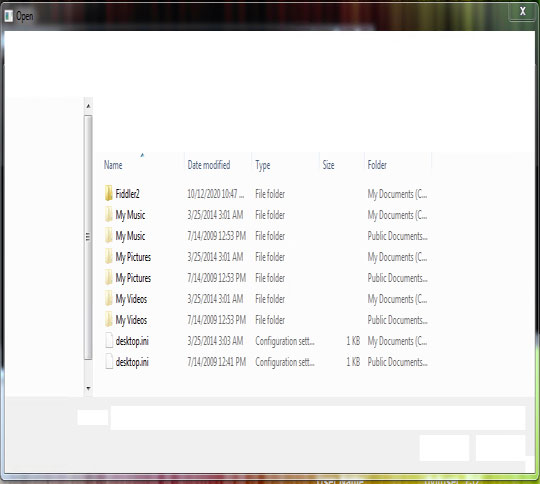
- Displays a dialog box that enables the user to select a file to open or save:
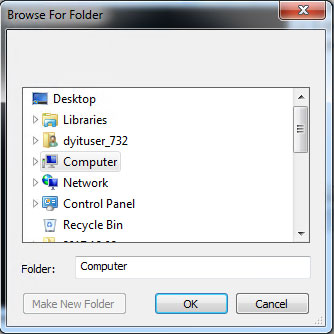
- Displays a dialog box that enables the user to select a folder:
- It displays gathered information on console window
It accepts the following parameters:
- /addextension -> Appends filename extension
- /aesdecode -> Decodes encrypted files using AES algorithm
- /aesencode -> Encrypts files using AES algorithm
- /base64decode -> Decodes encrypted files using Base64
- /browseforfile -> Looks for file/s specified by the user
- /browseforfolder -> Looks for folders specified by the user
- /center -> Sets console window to the center of the screen
- /changeexeicon -> Changes the icon of a file
- /closewindow -> Sends the specified message to a window
- /crc32 -> Gets the crc32 value of a file
- /disablewindow -> Disables a window
- /download -> Downloads a file from specified URL
- /downloadheader -> Downloads header from specified URL and saves it as a file
- /enablewindow -> Enables a window
- /findexecutable -> Retrieves the name of and handle to the executable file associated with a specific document file
- /flashconsole -> Flashes the specified console (Window caption or Taskbar button)
- /flashwindow -> Flashes the specified window (Window caption or Taskbar button)
- /getcursorposx -> Retrieves the position of the mouse cursor, in x coordinates
- /getcursorposy -> Retrieves the position of the mouse cursor, in y coordinates
- /getdesktopheight -> Retrieves the desktop height
- /getdesktopwidth -> Retrieves the desktop width
- /getextension -> Retrieves file extension
- /getfilename -> Retrieves filename
- /getmimetype -> Retrieves MIME type
- /getconsoletitle -> Retrieves console title
- /getsystemlanguage -> Retrieves the system language
- /getspecialfolder -> Retrieves the special folders of the affected machine
- /getcomputername -> Retrieves the computer name of the affected machine
- /getcpuname -> Retrieves the cpu name of the affected machine
- /getuserlanguage -> Retrieves the user language of the affected machine
- /getusername -> Retrieves the user name of the affected machine
- /hideself -> Hides the console window
- /hidewindow -> Hides a window
- /input -> Changes console mode to an input console
- /inputbox -> Activates a new input console window
- /is64bit -> Checks if it is being ran on a 64-bit environment
- /lowercase -> Converts string to lowercase
- /lzma -> Compresses files using the LZMA algorithm
- /makeadmin -> Updates resource of file to admin
- /makeguid -> Creates a GUID, a unique 128-bit integer
- /makeshortcut -> Creates a shortcut to a file
- /maskedinput -> Changes console mode to an input console. User input is masked with asterisk (*)
- /maskedinputbox -> Activates a new input console window. User input is masked with asterisk (*)
- /maximizewindow -> Places (posts) a message in the message queue
- /md5 -> Gets the md5 value of a file
- /messagebox -> Creates a messagebox
- /minimizewindow -> Places (posts) a message in the message queue
- /mouseclick -> Retrieves mouse position and button state
- /movewindow -> Changes window position
- /osversion-> Retrieves OS Version of the affected machine
- /play -> Plays sounds
- /random -> Generates random string
- /rc4 -> Encrypts files using RC4 algorithm
- /readpreferencevalue -> Reads preference value in configuration file
- /removeextension -> Removes the file name extension from a path
- /renameextension -> Replaces the extension of a file name with a new extension
- /resizewindow -> Changes window size and dimension
- /savefiledialog -> Creates a Save dialog box that lets the user specify a file to save
- /screenshot -> Takes a screenshot of the desktop
- /sendkeys -> Retrieves keystrokes and virtual-key code of the keyboard
- /setforegroundwindow -> Brings a window to the foreground
- /setwindowtitle -> Changes the text of the specified window's title bar
- /setconsoletransparency -> Sets the opacity and transparency color key of the console to be completely transparent
- /setwindowtransparency -> Sets the opacity and transparency color key of a window to be completely transparent
- /sha1 -> Gets the sha1 value of a file
- /showself -> Activates the console and displays it in its current size and position
- /showwindow -> Activates a window and displays it in its current size and position
- /setclipboardtext -> Opens, empties, and sets clipboard data of the affected machine
- /setcursor -> Moves the cursor to the specified screen coordinates
- /speak -> Activates the Text-to-Speech voice application based on the OS version of the affected machine
- /sleep -> Infinite sleep
- /tempfile -> Creates a temporary filename
- /uppercase -> Converts string to uppercase
- /unlzma -> Decompresses files using the LZMA algorithm
- /unzip -> Unzip compress files
- /windowontop -> Places the window above all non-topmost windows
- /writepreferencevalue -> Update the preference value in a configuration file
- /zip -> Zip files
SOLUTION
Step 1
Before doing any scans, Windows 7, Windows 8, Windows 8.1, and Windows 10 users must disable System Restore to allow full scanning of their computers.
Step 2
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 3
Scan your computer with your Trend Micro product to delete files detected as Trojan.Win32.HUMBLE.A. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check the following Trend Micro Support pages for more information:
Did this description help? Tell us how we did.

