SYMBOS_ZBOT.B
Information Stealer
Symbian OS


Threat Type: Spyware
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
Trend Micro has flagged this spyware as noteworthy due to the increased potential for damage, propagation, or both, that it possesses. Specifically, it is a mobile device Zeus malware that steals user credentials from SMS messages.
To get a one-glance comprehensive view of the behavior of this Spyware, refer to the Threat Diagram shown below.
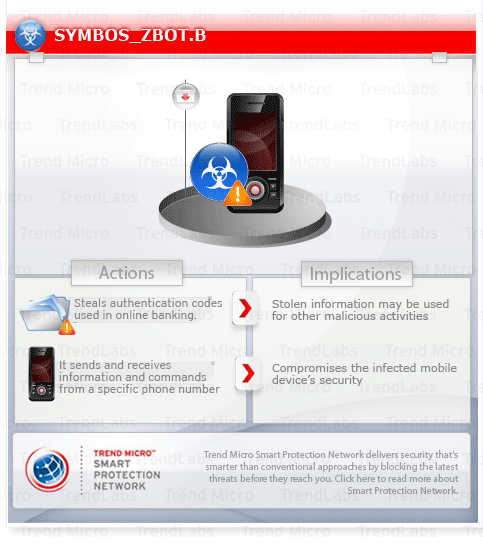
It monitors SMS messages of an infected Symbian phone then forwards the message if the sender is listed in its monitored list. Its primary objective is to steal authentication codes used in online banking.
It sends and receive information/commands from a certain number.
This spyware may be unknowingly downloaded by a user while visiting malicious websites.
TECHNICAL DETAILS
Arrival Details
This spyware may be unknowingly downloaded by a user while visiting malicious websites.
Installation
This spyware drops the following files:
- C:\system\apps\u.dat
- C:\system\apps\u.sisx
- C:\private\20039E30\firststart.dat
- C:\private\20039E30\settings2.dat
- {install path}\CertificateUpdate.exe
- C:\private\20039E30\NumbersDB.db
It drops the following copies of itself into the affected system:
- C:\sys\bin\SmsControl.exe
It creates the following folders:
- C:\private\20039E30
Other Details
This spyware does the following:
- Monitors SMS messages of an infected Symbian phone then forwards these message if the sender is listed in its monitored list. Its primary objective is to steal authentication codes used in online banking.
- Sends and receives information/commands from the following phone number:
- {BLOCKED}481813
- Interprets the following messages as its backdoor commands:
- ON/OFF - sets the malware state
- SET ADMIN - sets a number as the command and control (C&C)
- REM SENDER ALL - removes all senders from monitored list
- ADD SENDER ALL - adds all contacts to the monitored list
- BLOCK ON - blocks incoming calls is ON
- BLOCK OFF - blocks incoming call is OFF
- UNINSTALL - renames C:\system\apps\u.dat to C:\system\apps\u.sisx and installs the said .SISX package
- ADD SENDER - adds a number to the monitored list
- REM SENDER - removes a number from the monitored list
- SET SENDER - replaces all numbers in the monitored list with a new number
- Notifies the remote user of the malware's current status by sending any of the following messages:
- App installed ok
- state is On
- state is Off
- monitoring all
- blocking is on
- blocking is off
The file C:\private\20039E30\settings2.dat contains settings for the malware including the state, blocking, monitoring, and phone number of the remote attacker
The file C:\private\20039E30\NumbersDB.db contains information about monitored contacts, phone numbers, and history:- tbl_contact:
index
name
descr
pb_contact_id - tbl_phone_number:
contact_id
phone_number - tbl_history:
event_id
pn_id
date
description
contact_info
contact_id
SOLUTION
Step 1
For Windows XP and Windows Server 2003 users, before doing any scans, please make sure you disable System Restore to allow full scanning of your computer.
Step 2
Scan your computer with your Trend Micro product to delete files detected as SYMBOS_ZBOT.B. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
NOTES:
If you recently connected your smartphone to your Windows PC, please do the aforementioned cleanup step.
Did this description help? Tell us how we did.


