EMOTET
Windows


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
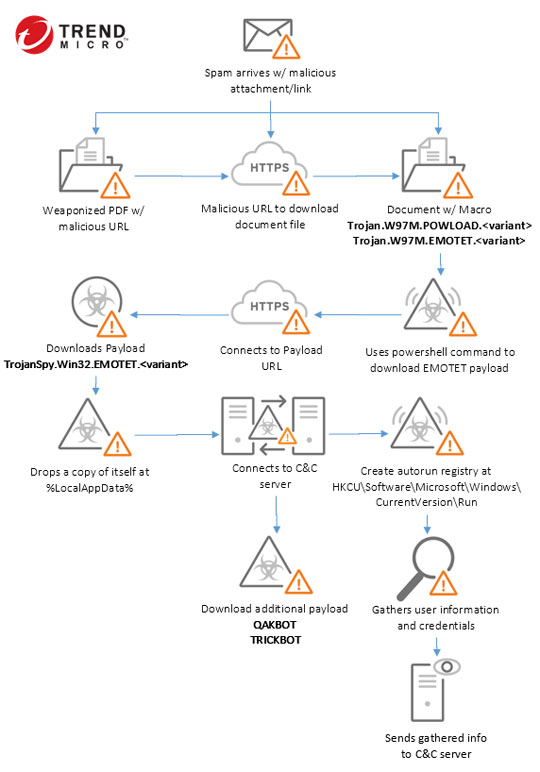
Emotet first appeared in 2014 as a banking malware that attempted to infect computers and steal sensitive information. This malware mostly spreads by spam and phishing emails with infected attachments and embedded malicious URLs. It has worm-like capabilities to spread to other connected computers. It also collects the victim's contact list and sends itself to the email addresses in the contact list.
In some of its spam campaigns, the emails commonly have a financial theme and appear to come as a reply to a previous transaction by using fake payment remittance notices, invoice attachments or payment details . Some variants use PowerShell macros, tricking users to open an attached document to enable macros and trigger a PowerShell command which attempts to download Emotet from compromised sites.
Emotet can target legitimate websites with WordPress themes by using arbitrary file upload vulnerability where the file mime type is not checked by server or code while attacker uploads backdoor script and the uploaded folder on given websites is directly accessible. Recently, EMOTET operates as malware-as-a-service (MaaS), offerring rent access to the Emotet-infected computers to infect them with other malware such as Trickbot and Ryuk.
In its latest spam campaign, some emails were identified to be stolen from existing victims to make it look more legitimate. Some attachments sent were PDF documents with malicious links, in addition to spam that sent out common MS Office macro attachments. A few Emotet samples were found to deliver other notorious malware such as TRICKBOT and QAKBOT.
Its behaviors include:
- Delivers more dangerous payload such as Trickbot, Qakbot, and Ryuk ransomware by renting Emotet-infected machines to other malware groups
- Steals computer data, computer name, system local, operating system (OS) version and running processes
- Steals user credentials, financial and banking information
- Steals usernames and passwords of different mail clients
- Executes backdoor commands from a remote malicious user to connect to malicious websites for sending and receiving information
It is capable of the following:
- Information Theft
- Backdoor commands
EMOTET typically follows the infection chain below: