ANDROIDOS_SPYGOLD.A
Spying Tool
Android OS


Threat Type: Backdoor
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
This backdoor is a Trojanized copy of a legitimate gaming application for Android OS smartphones. It steals sensitive information of the affected phone's SMS and calls functions, compromising the security of the device and of the user.
To get a one-glance comprehensive view of the behavior of this Backdoor, refer to the Threat Diagram shown below.
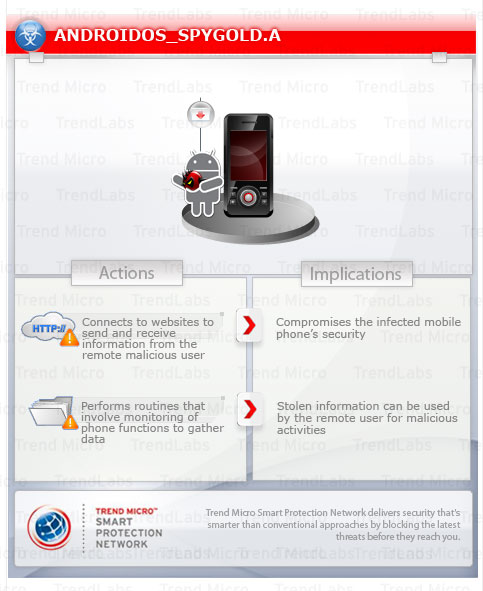
This backdoor is a Trojanized copy of a legitimate gaming application for Android. It inserts its own receiver and service into the affected phone to execute its malicious routines.
It monitors the affected phone's SMS and phone calls and sends stolen information to a remote URL.
It connects to a malicious URL in order to receive commands from a remote malicious user.
This backdoor may be manually installed by a user.
It connects to a website to send and receive information.
It steals certain information from the system and/or the user.
TECHNICAL DETAILS
Arrival Details
This backdoor may be manually installed by a user.
Backdoor Routine
This backdoor connects to the following websites to send and receive information:
- http://{BLOCKED}r.gicp.net
Information Theft
This backdoor steals the following information:
- Device ID
- Sim Serial Number
- Subscriber ID
NOTES:
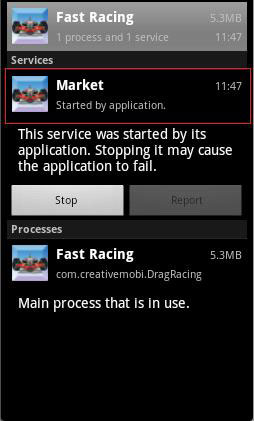
This backdoor is a Trojanized copy of a racing game. The malware inserts its own receiver and service to execute its malicious routines.
When the phone boots or the BOOT_COMPLETED action is triggered, it will start its service named Market. The service is named such so that users are deceived into thinking that it is a legitimate service.
It monitors the incoming text messages. Once a message is received, it will record the message body and the sender's phone number to a text file named ZJSMS.TXT.
It also monitors your incoming and outgoing calls. Same with the received text messages, it records the details of a call to a text file and saves it as ZJPHONECALL.TXT. It can phone home and send the phone's information such as Device ID, Subscriber ID, and Sim Serial Number using this link:
- http://{BLOCKED}r.{BLOCKED}p.net/zj/RegistUid.aspx?
- http://{BLOCKED}r.{BLOCKED}p.net/zj/upload/UploadFiles.aspx
- http://{BLOCKED}r.{BLOCKED}p.net/zj/allotWorkTask.aspx
- Send SMS
- Initiate a call
- Install/Uninstall apps
- Upload files
It is also capable of updating the site it uses.
SOLUTION
Step 1
Trend Micro Mobile Security Solution
Trend Micro Mobile Security Personal Edition protects Android smartphones and tablets from malicious and Trojanized applications. The App Scanner is free and detects malicious and Trojanized apps as they are downloaded, while SmartSurfing blocks malicious websites using your device's Android browser.
Download and install the Trend Micro Mobile Security App via Google Play.
Step 2
Remove unwanted apps on your Android mobile device
Did this description help? Tell us how we did.


