ANDROIDOS_ROOTSMART.A
Information Stealer, Premium Service Abuser, Malicious Downloader, Rooting Tool
Android OS


Threat Type: Trojan
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
The number of infected phones by this malware increases rapidly. Hence, the cybercriminal responsible is able to generate a large amount of revenue given that the current infection rates are sustained.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
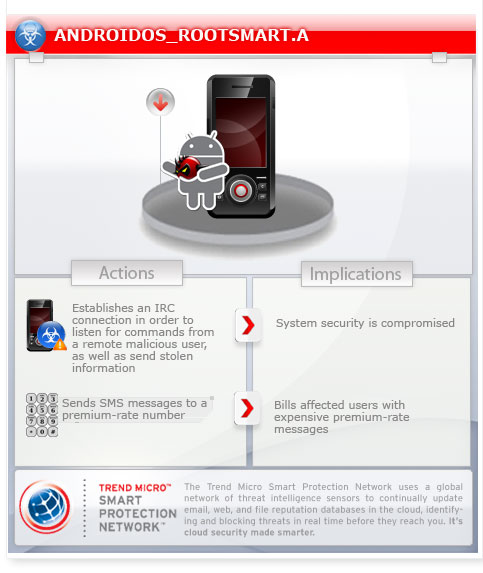
This Trojan may perform certain routines when installed on the affected device.
It collects certain device information and sends it to a remote server.
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It connects to a website to send and receive information.
TECHNICAL DETAILS
Arrival Details
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Backdoor Routine
This Trojan connects to the following websites to send and receive information:
- go.{BLOCKED}ui.com
NOTES:
This Trojan may perform the following routines when installed on the affected device:
- Access pay-per-view video
- Boot the device
- Call premium-rate numbers
- Check phone current state
- Download APK and other files
- Get information on running tasks
- Get local information
- Install application
- Prevents screen from turning off or dimming
- Read/Write the SYNC settings
- Search/pair/connect to bluetooth devices
- Send SMS to premium service numbers
- Shutdown the device
- Start its own application
- Steal information from the device
- Vibrates the device
- Write/Modify APN settings
It collects the following device information and sends it to a remote server:
- CID
- IMEI
- IMSI
- Install Type
- LAC
- MNC
- Package ID
- Package Level
- Package Name
- Phone Model Number
- Phone Version
- Release version
- SMS Center
SOLUTION
Step 1
Trend Micro Mobile Security Solution
Trend Micro Mobile Security Personal Edition protects Android smartphones and tablets from malicious and Trojanized applications. The App Scanner is free and detects malicious and Trojanized apps as they are downloaded, while SmartSurfing blocks malicious websites using your device's Android browser.
Download and install the Trend Micro Mobile Security App via Google Play.
Step 2
Remove unwanted apps on your Android mobile device
Did this description help? Tell us how we did.


