ANDROIDOS_LOCKER.HBT
Click Fraud
Android OS


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
This is the first mobile ransomware that uses Tor, a legitimate service that allows for concealed server connections. Users with mobile devices affected by this malware may find the files stored in their mobile device rendered useless and held for ransom. This would result in data loss and possibly financial loss as well.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
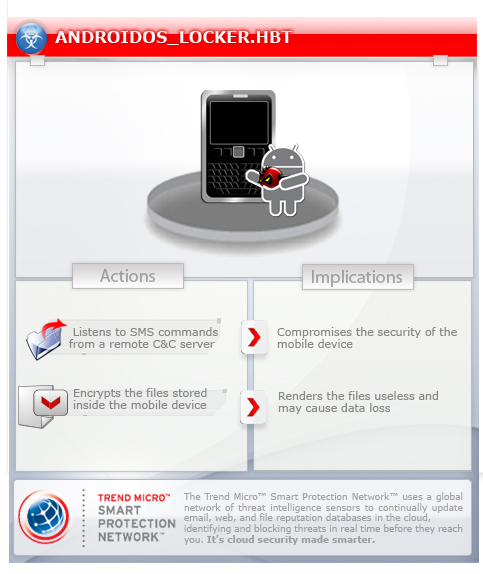
This Trojan may be downloaded from app stores/third party app stores.
TECHNICAL DETAILS
Arrival Details
This Trojan may be downloaded from app stores/third party app stores.
NOTES:
After installed, this malware poses as a fraud application named “Sex xonix.”

Once launched, the app shows a user interface (UI) to trick users into paying the 1,000 ruble ransom. If users don’t pay, the ransom amount, the message informs the user that the data in their phone will be "permanently destroyed" as the phone will be locked forever.
Upon every time system boot, this ransomware will launch automatically.
UI shown by ransomware:

Below is a rough translation of the warning:
For downloading and installing software nelitsenzionnnogo your phone has been blocked in accordance with Article 1252 of the Civil Code of the Russian Federation Defence exclusive rights.
To unlock your phone pay 1000 rubles.
You have 48 hours to pay, otherwise all data on your phone will be permanently destroyed!
- Locate the nearest terminal payments system QIWI
- Approach to the terminal and choose replenishment QIWI VISA WALLET
- Enter the phone number 79660624806 and press next
- Window appears comment – then enter your phone number without 7ki
- Put money into terminal and press pay
- Within 24 hours after payment is received, your phone will be unlocked.
- So you can pay via mobile shops and Messenger Euronetwork
CAUTION: Trying to unlock the phone yourself will lead to complete full lock your phone, and the loss of all the information without further opportunities unlock.
The user is then prompted to pay to the account 79660624806/79151611239/79295382310 by QIWI or 380982049193 by Monexy within 48 hours. This UI will also keep popping out, thus preventing the user from being able to use their device properly.
The files on device (both in internal and external storage) with following format are encrypted:
- .JPEG
- .JPG
- .PNG
- .BMP
- .GIF
- .DOC
- .DOCX
- .TXT
- .AVI
- .MKV
- .3GP
- .MP4
This ransomware communicates with its C&C by Tor with the following address:
- http://{BLOCKED}4wtxee23q6.onion/
SOLUTION
Scan your computer with your Trend Micro product to delete files detected as ANDROIDOS_LOCKER.HBT. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
NOTES:
For users whose devices are infected with this ransomware, the malicious app can be manually removed through the Android Debug Bridge. The adb is part of the Android SDK, which can be freely downloaded from the Android website. The process would proceed as follows:
- Install the Android SDK on a PC, including the adb component.
- Connect the affected device via USB to the PC.
- Run the following command from the command line:
adb uninstall “org.simplelocker”
This procedure will work without problem for devices with Android versions lower than 4.2.2. For 4.2.2 and later users, however, there is a problem: the phone will prompt the user with a dialog to accept a key to allow debugging. However, the ransomware’s own UI will keep interrupting this, making it difficult to use adb to remove the phone.
Did this description help? Tell us how we did.


