Identity theft is currently a gold mine for cybercriminals—one that reached an all-time high in 2016, with up to $16 billion worth of losses caused by fraud and identity theft. Most people are already aware that theft can happen due to high visibility cases that occurred during the past couple of years, like the attack on Yahoo during latter half of 2016. While identity theft should be concerning in itself, the real, tangible damage usually comes after, when an attacker uses the stolen information for malicious purposes.

This can have devastating consequences for a user, especially when the attacker starts targeting important aspects of their lives such as insurance, bank and credit card information. Many users are actually unaware that they have been compromised, and get surprised when faced with the consequences of identity fraud.
But where exactly does this stolen information end up? Do they get sold in underground markets? Perhaps bundled with other stolen information and sold to legitimate companies? Used for payment fraud? Before we delve into where stolen information and data goes, let us first look at how this information can be stolen.
How is the information stolen?
While the prevalence of high-profile incidents might lead the general public to think that hacking is the primary cause of compromised information, data that we gathered from our paper titled Follow the Data: Dissecting Data Breaches and Debunking the Myths reveals that from 2005 to 2015, device loss or theft was actually the primary cause of stolen information. However, in terms of prevalence, hacking and malware was not far behind. Unintended disclosures and insider leaks also ranked high up in terms of causes.
What happens to the stolen information?
Typically, the type of stolen information dictates where it all ends up. Here are some specific examples of what happens to stolen data.
Underground
Markets
Personally identifiable information (PII) is defined as data that can be used to identify, locate, or contact a specific individual. Examples of personally identifiable information include names, birth dates, addresses, social security numbers, phone numbers and all other data that is used to distinguish or identify an individual.
PII, which is the most likely type of data stolen, is highly versatile in terms of how cybercriminals can use the information. Attackers can often go for malicious attacks that impact the victim directly, by applying for loans or credit cards under the user’s name, filing fraudulent income tax returns, and applying for loans under the victim’s name. On the other hand, victims can also be impacted indirectly when their PII is sold to marketing firms or companies that specialize in spam campaigns.
Financial information is data that is used in an individual’s financial activities. This includes banking information, billing accounts, insurance information and other data that can be used to access accounts or process financial transactions.
When this information is stolen, it could greatly impact a user’s finances. A cybercriminal can use financial information for simple malicious activities such as paying bills, performing fraudulent online transactions, and transferring money out of victims’ bank accounts. More dedicated cybercriminals and groups may even resort to creating counterfeit credit cards for their own use.
Healthcare information pertains to data that is used for an individual’s medical services. This includes hospital records, medical insurance and other related information.
Healthcare is similar to PII in that they also contain a large number of a user’s identifying information. While it can similarly reveal an individual’s personal information, healthcare information can be potentially used to buy prescription drugs that can’t be bought over the counter. This can lead to abuse, especially when it comes to drug-related scenarios for prescription medicines.
Education information refers to an individual’s data based on his educational records. This includes transcripts and school records.
While education information does not yield immediate results in the same kind of way that financial information can provide, it exposes users to potential blackmail or extortion. An attacker can use education information to scare or trick users into giving in to their demands. Similarly, cybercriminals can also use this information to perform phishing attacks by pretending to be students or officials of an academic institution.
Payment card information pertains to data found in an individual’s payment cards, which include credit and debit card data as well as other related information.
This data is similar to financial information in that it can affect the user’s finances. However, payment card information might even be more dangerous as they can be used to make immediate purchases and transactions online based on the information found in the card. Both financial and payment card information are often correlated with each other.
Digital or online credentials refer to data that is used to very that the user is really who he or she is claiming to be. This includes email usernames and passwords as well as online shopping log-in credentials.
Theft of user credentials might even be more dangerous than PII, as it essentially exposes the victim’s online accounts to potential malicious use. Email is often used to verify credentials and store information from other accounts, and a compromised email account can lead to further instances of fraud and identity theft. Emails and social media accounts can also be used to perpetrate spam and phishing attacks, while other cybercriminals may use stolen accounts to pull off espionage attacks or steal intellectual property from organizations the user is a part of.
Based on our research, we also have evidence that these types of information are interrelated. If one type of data, such as healthcare is stolen, there is also a large chance that other types might also have been compromised.
As an example, a cybercriminal manages to get hold of a user’s email credentials. Unfortunately for the victim, this email also contains billing invoices for credit cards, giving the cybercriminal access to bank information where he can apply for possible loans in the user’s name. This email also contains the user’s Facebook account, which also uses the same password as his email. In a single attack, the cybercriminal already gains access to a wide array of information—enough to perform multiple types of identity fraud.
How much is personal information worth?
In a study conducted in 2015, Trend Micro asked more than a thousand individuals around the world to place a monetary value on their data. Respondents notably put the most value on their passwords:
| Type of data | Estimate monetary value |
| Passwords | $75.80 |
| Health information and medical records | $59.80 |
| Social Security numbers | $55.70 |
| Payment details | $36.60 |
| Purchase history | $20.60 |
| Physical location information | $16.10 |
| Home address | $12.90 |
| Photos and videos | $12.20 |
| Marital status | $8.30 |
| Name and gender | $2.90 |
PII does have tangible monetary value in the underground markets, where the price of stolen information depends on how useful they are to fraudsters. Here are some prices for stolen data we found during our research into the cybercriminal underground markets for the paper mentioned earlier (prices are as of 2015, in USD):
- PII is commonly sold on a per-line basis at $1 per line.
- Full credit reports of people with very high FICO23 scores are available for purchase at $25 per report.
- Full scans of documents like passports, drivers’ licenses, utility bills, and others are available for purchase from $10 to $35 per scanned document.
- Login credentials for banks around the world are sold between $200 and $500 per account in deep web marketplaces.
- Accounts for various mobile phone operators in the US are available for up to $14 per account.
- Mature PayPal and eBay accounts (accounts with years of transaction history), are sold for up to $300 each. Mature accounts are less likely to be flagged for suspicious transactions.
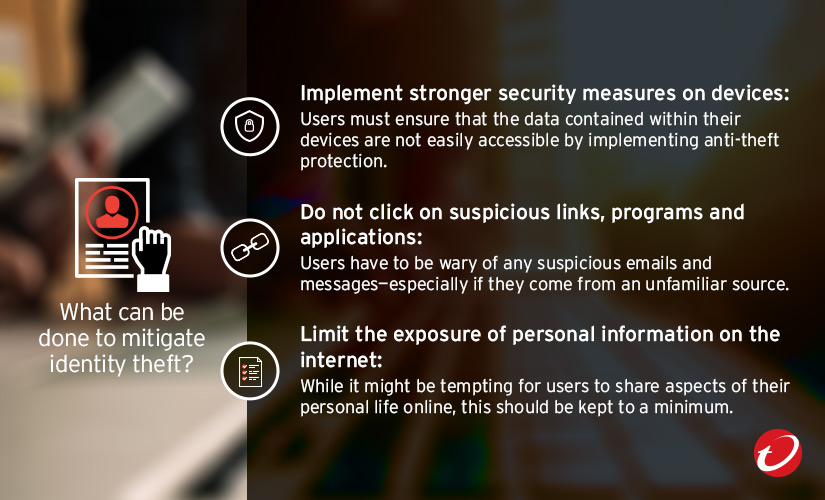
What can be done to mitigate identity theft?
Due to the widespread nature of identity theft, users and organizations must be careful with all personal information—whether it belongs to an individual or to members of the organization. Here are some ways to mitigate or even stop any attempts at potential identity theft.
Trend Micro Solutions:
In addition to the best practices mentioned above, users can look into solutions such as Trend Micro™ Security and Trend Micro Internet Security, which offer effective protection against identity theft. In addition, enterprises can monitor all ports and network protocols to detect advanced threats and protect from targeted attacks via Trend Micro™ Deep Discovery™ Inspector.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One