Protecting Point of Sales Systems from PoS Malware
 View infographic: Protecting Point of Sales Systems from PoS Malware
View infographic: Protecting Point of Sales Systems from PoS Malware
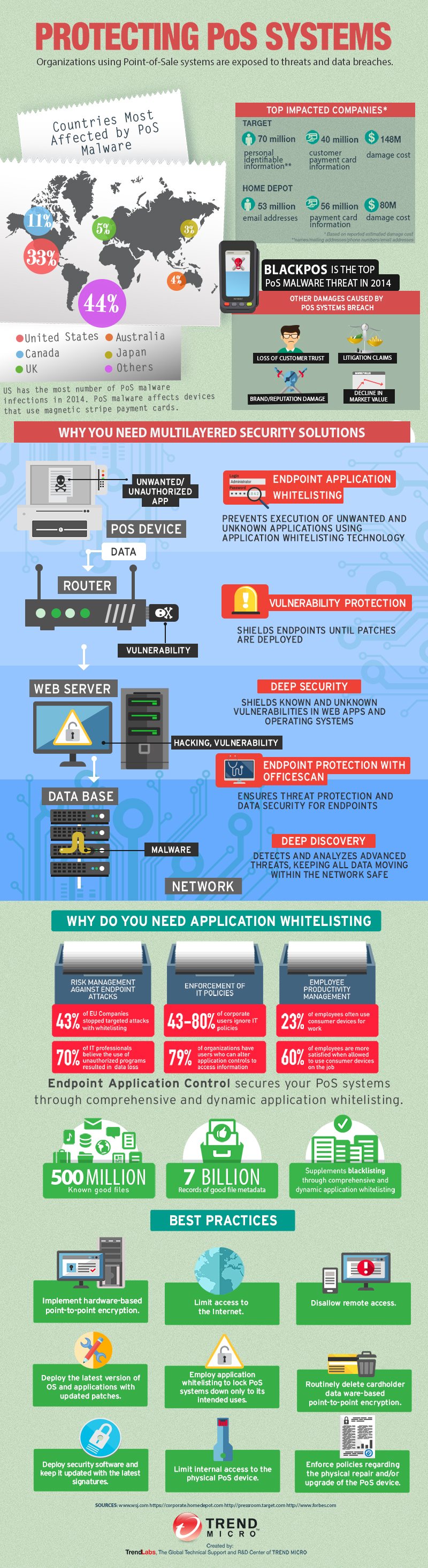
2014 went down in history as year of the “largest retail hacks”. After notable breaches that affected Home Depot and Kmart, PoS attacks have become a common occurrence in the security threat landscape. However, despite the number of past incidents that should have served as a warning for organizations and individuals, companies are still constantly hit by PoS attacks.
PoS Systems and PoS Malware
A PoS system provides operational information such as inventory management, accounting, and sales tracking. It requires a network connection to validate payments by sellers. In the past, criminals relied on physical skimmers to pull data from payment cards. Today, cybercriminals use malware in point of sale systems to steal data primarily from magnetic stripe credit cards. It’s important to know that personal and sensitive data stolen from debit and credit cards can be used by cybercriminals to impersonate unknowing users.
For users, this could result in financial loss, damaged credit standing, and fraudulent purchases. In the event that a customer experiences purchase fraud, they could get their money back if they used a credit card, however, in most cases getting their money back may take time. Companies in turn could suffer litigation claims, loss of customer trust, brand and reputation damage, and eventual decline in market value.
What it takes to protect PoS systems
PoS malware continues to evolve and organizations need to promptly address this trending security problem by deploying integrated data protection for users. Banks should consider issuing chip and PIN cards, which offer better security compared to magnetic stripe cards.
Use a multi-layered security solution that will enable your organization to control user data while giving you enterprise-wide visibility. Employ application whitelisting technology to control which applications run in your network. This complete approach can help prevent PoS-related data breaches and business disruption from gateway and mobile devices. In addition, you can centrally manage threat and data policies across multiple layers of your IT infrastructure, streamline management, and provide more consistent policy enforcement.
View the attached infographic, Protecting PoS Systems, to see how multi-layered security solutions and endpoint application whitelisting can help defend systems from PoS malware.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One