Addressing Threats Like Ryuk via Trend Micro XDR
 View Infographic: Addressing Threats Like Ryuk via Trend Micro XDR
View Infographic: Addressing Threats Like Ryuk via Trend Micro XDR
In today’s security landscape, threats that affect multiple layers of an organization’s infrastructure are common. In response to the challenge of detecting and responding to these kinds of attacks, businesses often use siloed security tools that are designed to focus on individual parts rather than the whole system.
Some companies have resorted to using security information and event management (SIEM) tools to help them aggregate the various threats they face on a daily basis. While effective, SIEM solutions are often expensive to own and operate. In addition, they often require security operation centers (SOCs) to sift through large amounts of data for correlation and analysis. Meanwhile, other security solutions might have powerful detection and response capabilities, but lack the telemetry required for seeing the bigger picture.
To understand what kind of threats SOCs are dealing with, and what kind of security solution is needed to address these threats, here’s a real-life example.
Introducing Ryuk: A modern-day threat
Ryuk has been one of the most noteworthy ransomware families in recent memory. It is perhaps the best representation of the new paradigm in ransomware attacks where malicious actors go for quality over sheer quantity.
On the surface, Ryuk does not seem too different from the ransomware families of the past; it still encrypts important files, documents, and other important data. However, one notable difference between Ryuk and other ransomware families is that unlike other ransomware malicious actors who go for indiscriminate victims using a “shotgun” method, the cybercriminals behind Ryuk go after specific targets while asking for much higher payouts. Because the malicious actors behind Ryuk often go after extremely sensitive information in industries such as finance and the military, the victim organizations often feel that they have no other recourse than to pay the substantial ransom amount.
In 2019, the Trend Micro™ Managed XDR and Incident Response teams investigated an incident concerning a Trend Micro customer that was infected with the Ryuk ransomware. This infection involved multiple layers of compromise, including multiple endpoints and the company’s network.
In this case, Ryuk’s routine involved the use of emails as an infection vector to get to the endpoint. From there, it spread to the rest of the network.
The infection started with a malicious spam mail that was sent to an employee of the organization. This email contained a malicious attachment — a downloader for TrickBot — which can spread within the network via two methods: either through the infamous EternalBlue exploit (which was also used in the WannaCry attacks of 2017) or through harvested credentials.
In the case of the Trend Micro customer, once TrickBot was downloaded into the system, it exploited vulnerable routers and used them as a command-and-control (C&C) server for sending and receiving instructions. Additionally, TrickBot deployed Ryuk as its payload.
TrickBots modules also show that it has information theft capabilities, so any organization that has been a victim of this attack can have their files encrypted and their information stolen — resulting in damage far beyond what regular ransomware families can do.
Fortunately, the Trend Micro Managed XDR was able to identify the compromised machines and the chain of attack by gathering data from various sources to create a clearer picture of what the organization was dealing with.
Trend Micro XDR: Designed for advanced threats
Trend Micro XDR is designed to combat threats like Ryuk using machine learning and analytics to correlate various events across multiple layers.
It comes either as a solutions platform or as a managed service via Trend Micro Managed XDR, which takes advantage of the whole wealth of knowledge and experience of Trend Micro’s security experts to provide 24/7 alert monitoring and prioritization, as well as investigation and threat hunting.
It addresses the significant challenges organizations face when implementing threat detection and response strategies, such as:
- Expensive and often incompatible security tools needed for data aggregation and analysis. A traditional SOC setup uses multiple pieces of software with different methods of storing and indexing data — that focus on different parts of the system. The siloed nature of these tools results in security analysts’ having to manually correlate data, making it an additional burden on their workflow.
- Endpoint detection and response (EDR) solutions that lack the full range of telemetry to accurately assess the full scope of an attack.
- The length of time spent on high-priority issues. This means that strengthening and improving security processes and system infrastructure take a back seat.
Through the use of machine learning, expert security analytics, and detection rules for correlation and prioritization of alerts, Trend Micro XDR can help an organization’s SOC lessen the time needed for triaging and research, thereby providing faster detection and response capabilities. It uses telemetry gathered from each vector to allow security analysts to gain complete insight into ongoing attacks, while also helping enhance the XDR analytics engine for a quicker and more effective response strategy for future attacks.
Trend Micro XDR uses a multifaceted approach that works on multiple layers of the system:
Emails
Trend Micro™ Cloud App Security protects the email layer through the use of machine learning for web reputation and URL dynamic analysis. It can detect suspicious content not only in the message body but also in the attachment. It can also provide sandbox malware analysis and document exploit detection.
Endpoints
Trend Micro Apex One™, features a number of automated threat detection capabilities that protect endpoints against threats such as ransomware and fileless malware. In addition, it can identify the endpoints affected by an attack via customizable on-demand investigation and monitoring capabilities.
Network
The Trend Micro™ Deep Discovery™ Email Inspector solution can monitor an organization’s network — including all physical, virtual, north-south, and east-west traffic. It provides complete visibility into all aspects of advanced threats like Ryuk through the use of specialized detection engines and custom sandbox analysis.
Cloud
The Trend Micro Cloud One™ – Workload Security solution protects cloud workloads, servers, and containers from threats in critical applications, operating systems, and platforms like Docker and Kubernetes through the use of techniques such as virtual patching and machine learning.
Our infographic illustrates how Trend Micro XDR protects each layer of an organization, using the Ryuk incident as a real-world example.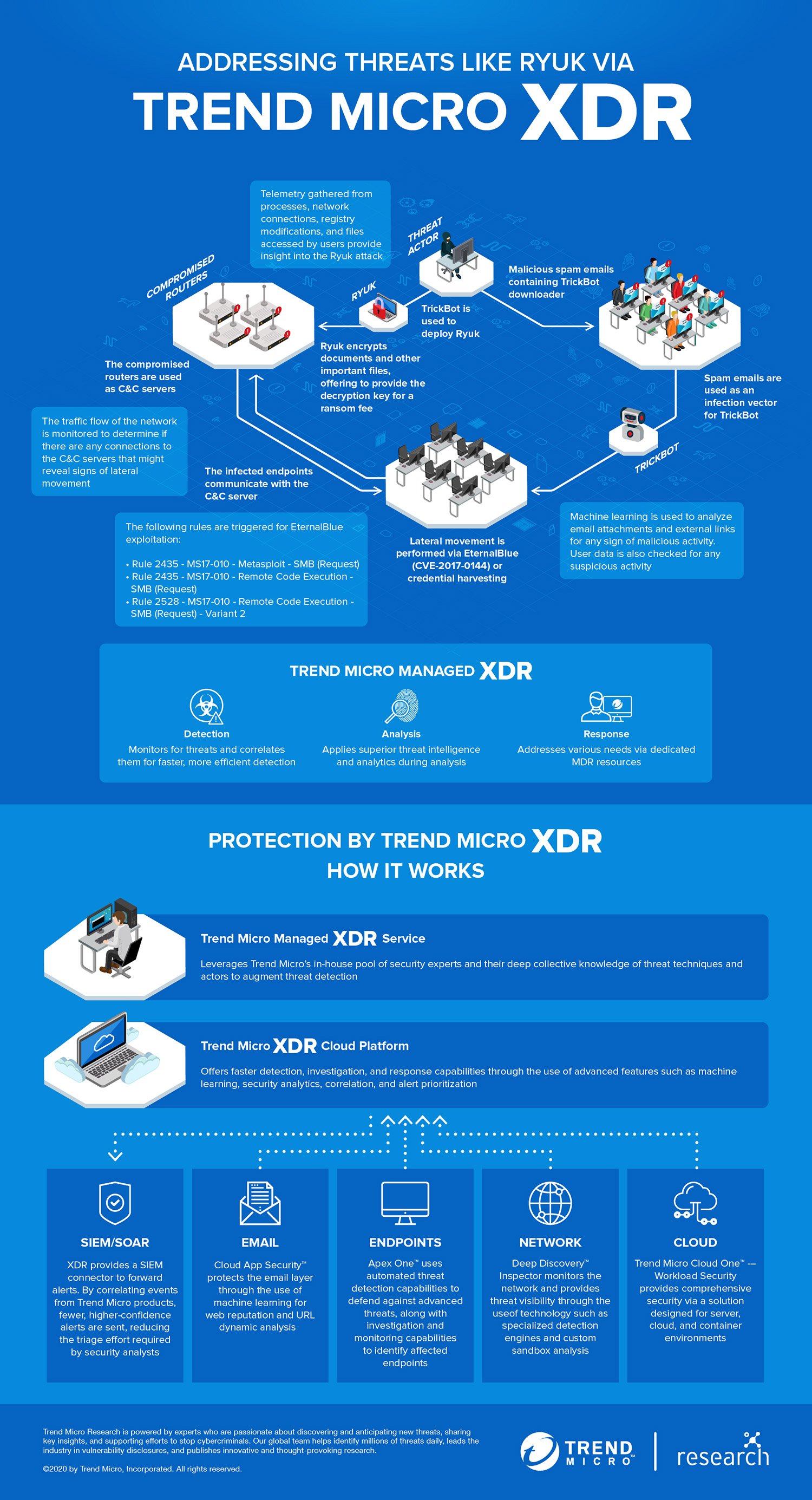
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One