OSX_QHOST.A
Trojan.BAT.Qhost.nh (Kaspersky)
Mac OS


Threat Type: Trojan
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This Trojan poses as a fake Flash Player installer package. Upon execution, it prompts the installation of a Flash Player application. It adds certain strings strings to "private/etc/hosts". This behavior is used to redirect the user to their server.
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
TECHNICAL DETAILS
Arrival Details
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Trojan drops the following copies of itself into the affected system:
- //Library/Receipts/FlashPlayer.pkg
It drops the following component file(s):
- //Library/Receipts/FlashPlayer.pkg/Contents/Archive.bom
- //Library/Receipts/FlashPlayer.pkg/Contents/Info.plist
- //Library/Receipts/FlashPlayer.pkg/Contents/PkgInfo
- //Library/Receipts/FlashPlayer.pkg/Contents/Resources/en.lproj/background
- //Library/Receipts/FlashPlayer.pkg/Contents/Resources/en.lproj/Description.plist
- //Library/Receipts/FlashPlayer.pkg/Contents/Resources/package_version
- //Library/Receipts/FlashPlayer.pkg/Contents/Resources/preinstall - contains the malicious script
- //~/bzab.km
It creates the following folders:
- //~/
NOTES:
It poses as a fake Flash Player installer package.
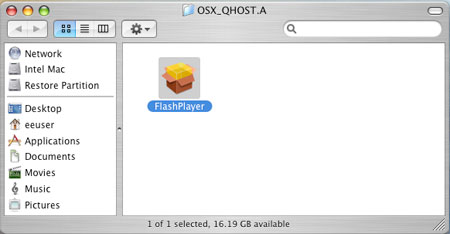
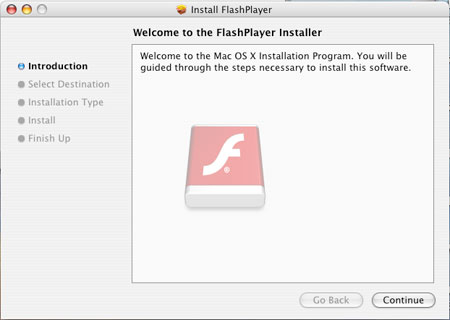
Upon execution, it prompts the installation of a Flash Player application:
This Trojan adds the following strings to "private/etc/hosts":
- {BLOCKED}.{BLOCKED}4.160.26 google.com
- {BLOCKED}.{BLOCKED}4.160.26 google.ae
- {BLOCKED}.{BLOCKED}4.160.26 google.as
- {BLOCKED}.{BLOCKED}4.160.26 google.at
- {BLOCKED}.{BLOCKED}4.160.26 google.az
- {BLOCKED}.{BLOCKED}4.160.26 google.ba
- {BLOCKED}.{BLOCKED}4.160.26 google.be
- {BLOCKED}.{BLOCKED}4.160.26 google.bg
- {BLOCKED}.{BLOCKED}4.160.26 google.bs
- {BLOCKED}.{BLOCKED}4.160.26 google.ca
- {BLOCKED}.{BLOCKED}4.160.26 google.cd
- {BLOCKED}.{BLOCKED}4.160.26 google.com.gh
- {BLOCKED}.{BLOCKED}4.160.26 google.com.hk
- {BLOCKED}.{BLOCKED}4.160.26 google.com.jm
- {BLOCKED}.{BLOCKED}4.160.26 google.com.mx
- {BLOCKED}.{BLOCKED}4.160.26 google.com.my
- {BLOCKED}.{BLOCKED}4.160.26 google.com.na
- {BLOCKED}.{BLOCKED}4.160.26 google.com.nf
- {BLOCKED}.{BLOCKED}4.160.26 google.com.ng
- {BLOCKED}.{BLOCKED}4.160.26 google.ch
- {BLOCKED}.{BLOCKED}4.160.26 google.com.np
- {BLOCKED}.{BLOCKED}4.160.26 google.com.pr
- {BLOCKED}.{BLOCKED}4.160.26 google.com.qa
- {BLOCKED}.{BLOCKED}4.160.26 google.com.sg
- {BLOCKED}.{BLOCKED}4.160.26 google.com.tj
- {BLOCKED}.{BLOCKED}4.160.26 google.com.tw
- {BLOCKED}.{BLOCKED}4.160.26 google.dj
- {BLOCKED}.{BLOCKED}4.160.26 google.de
- {BLOCKED}.{BLOCKED}4.160.26 google.dk
- {BLOCKED}.{BLOCKED}4.160.26 google.dm
- {BLOCKED}.{BLOCKED}4.160.26 google.ee
- {BLOCKED}.{BLOCKED}4.160.26 google.fi
- {BLOCKED}.{BLOCKED}4.160.26 google.fm
- {BLOCKED}.{BLOCKED}4.160.26 google.fr
- {BLOCKED}.{BLOCKED}4.160.26 google.ge
- {BLOCKED}.{BLOCKED}4.160.26 google.gg
- {BLOCKED}.{BLOCKED}4.160.26 google.gm
- {BLOCKED}.{BLOCKED}4.160.26 google.gr
- {BLOCKED}.{BLOCKED}4.160.26 google.ht
- {BLOCKED}.{BLOCKED}4.160.26 google.ie
- {BLOCKED}.{BLOCKED}4.160.26 google.im
- {BLOCKED}.{BLOCKED}4.160.26 google.in
- {BLOCKED}.{BLOCKED}4.160.26 google.it
- {BLOCKED}.{BLOCKED}4.160.26 google.ki
- {BLOCKED}.{BLOCKED}4.160.26 google.la
- {BLOCKED}.{BLOCKED}4.160.26 google.li
- {BLOCKED}.{BLOCKED}4.160.26 google.lv
- {BLOCKED}.{BLOCKED}4.160.26 google.ma
- {BLOCKED}.{BLOCKED}4.160.26 google.ms
- {BLOCKED}.{BLOCKED}4.160.26 google.mu
- {BLOCKED}.{BLOCKED}4.160.26 google.mw
- {BLOCKED}.{BLOCKED}4.160.26 google.nl
- {BLOCKED}.{BLOCKED}4.160.26 google.no
- {BLOCKED}.{BLOCKED}4.160.26 google.nr
- {BLOCKED}.{BLOCKED}4.160.26 google.nu
- {BLOCKED}.{BLOCKED}4.160.26 google.pl
- {BLOCKED}.{BLOCKED}4.160.26 google.pn
- {BLOCKED}.{BLOCKED}4.160.26 google.pt
- {BLOCKED}.{BLOCKED}4.160.26 google.ro
- {BLOCKED}.{BLOCKED}4.160.26 google.ru
- {BLOCKED}.{BLOCKED}4.160.26 google.rw
- {BLOCKED}.{BLOCKED}4.160.26 google.sc
- {BLOCKED}.{BLOCKED}4.160.26 google.se
- {BLOCKED}.{BLOCKED}4.160.26 google.sh
- {BLOCKED}.{BLOCKED}4.160.26 google.si
- {BLOCKED}.{BLOCKED}4.160.26 google.sm
- {BLOCKED}.{BLOCKED}4.160.26 google.sn
- {BLOCKED}.{BLOCKED}4.160.26 google.st
- {BLOCKED}.{BLOCKED}4.160.26 google.tl
- {BLOCKED}.{BLOCKED}4.160.26 google.tm
- {BLOCKED}.{BLOCKED}4.160.26 google.tt
- {BLOCKED}.{BLOCKED}4.160.26 google.us
- {BLOCKED}.{BLOCKED}4.160.26 google.vu
- {BLOCKED}.{BLOCKED}4.160.26 google.ws
- {BLOCKED}.{BLOCKED}4.160.26 google.co.ck
- {BLOCKED}.{BLOCKED}4.160.26 google.co.id
- {BLOCKED}.{BLOCKED}4.160.26 google.co.il
- {BLOCKED}.{BLOCKED}4.160.26 google.co.in
- {BLOCKED}.{BLOCKED}4.160.26 google.co.jp
- {BLOCKED}.{BLOCKED}4.160.26 google.co.kr
- {BLOCKED}.{BLOCKED}4.160.26 google.co.ls
- {BLOCKED}.{BLOCKED}4.160.26 google.co.ma
- {BLOCKED}.{BLOCKED}4.160.26 google.co.nz
- {BLOCKED}.{BLOCKED}4.160.26 google.co.tz
- {BLOCKED}.{BLOCKED}4.160.26 google.co.ug
- {BLOCKED}.{BLOCKED}4.160.26 google.co.uk
- {BLOCKED}.{BLOCKED}4.160.26 google.co.za
- {BLOCKED}.{BLOCKED}4.160.26 google.co.zm
- {BLOCKED}.{BLOCKED}4.160.26 google.com
- {BLOCKED}.{BLOCKED}4.160.26 google.com.af
The behavior described above is used to redirect the user to their server.
SOLUTION
NOTES:
Deleting Malware Folder
Go to your root folder and drag the ~ folder to the Trash. You may also right-click on the application then select Move to Trash.
Deleting Malware File
Go to your Library > Receipts folder and drag FlashPlayer.pkg to the Trash. You may also right-click on the application then select Move to Trash.
Restoring the /private/etc/hosts file.
A. Open the Terminal and type the following command:
- sudo nano /private/etc/hosts
B. Remove the following strings added by the malware:
- {BLOCKED}.{BLOCKED}4.160.26 google.com
- {BLOCKED}.{BLOCKED}4.160.26 google.ae
- {BLOCKED}.{BLOCKED}4.160.26 google.as
- {BLOCKED}.{BLOCKED}4.160.26 google.at
- {BLOCKED}.{BLOCKED}4.160.26 google.az
- {BLOCKED}.{BLOCKED}4.160.26 google.ba
- {BLOCKED}.{BLOCKED}4.160.26 google.be
- {BLOCKED}.{BLOCKED}4.160.26 google.bg
- {BLOCKED}.{BLOCKED}4.160.26 google.bs
- {BLOCKED}.{BLOCKED}4.160.26 google.ca
- {BLOCKED}.{BLOCKED}4.160.26 google.cd
- {BLOCKED}.{BLOCKED}4.160.26 google.com.gh
- {BLOCKED}.{BLOCKED}4.160.26 google.com.hk
- {BLOCKED}.{BLOCKED}4.160.26 google.com.jm
- {BLOCKED}.{BLOCKED}4.160.26 google.com.mx
- {BLOCKED}.{BLOCKED}4.160.26 google.com.my
- {BLOCKED}.{BLOCKED}4.160.26 google.com.na
- {BLOCKED}.{BLOCKED}4.160.26 google.com.nf
- {BLOCKED}.{BLOCKED}4.160.26 google.com.ng
- {BLOCKED}.{BLOCKED}4.160.26 google.ch
- {BLOCKED}.{BLOCKED}4.160.26 google.com.np
- {BLOCKED}.{BLOCKED}4.160.26 google.com.pr
- {BLOCKED}.{BLOCKED}4.160.26 google.com.qa
- {BLOCKED}.{BLOCKED}4.160.26 google.com.sg
- {BLOCKED}.{BLOCKED}4.160.26 google.com.tj
- {BLOCKED}.{BLOCKED}4.160.26 google.com.tw
- {BLOCKED}.{BLOCKED}4.160.26 google.dj
- {BLOCKED}.{BLOCKED}4.160.26 google.de
- {BLOCKED}.{BLOCKED}4.160.26 google.dk
- {BLOCKED}.{BLOCKED}4.160.26 google.dm
- {BLOCKED}.{BLOCKED}4.160.26 google.ee
- {BLOCKED}.{BLOCKED}4.160.26 google.fi
- {BLOCKED}.{BLOCKED}4.160.26 google.fm
- {BLOCKED}.{BLOCKED}4.160.26 google.fr
- {BLOCKED}.{BLOCKED}4.160.26 google.ge
- {BLOCKED}.{BLOCKED}4.160.26 google.gg
- {BLOCKED}.{BLOCKED}4.160.26 google.gm
- {BLOCKED}.{BLOCKED}4.160.26 google.gr
- {BLOCKED}.{BLOCKED}4.160.26 google.ht
- {BLOCKED}.{BLOCKED}4.160.26 google.ie
- {BLOCKED}.{BLOCKED}4.160.26 google.im
- {BLOCKED}.{BLOCKED}4.160.26 google.in
- {BLOCKED}.{BLOCKED}4.160.26 google.it
- {BLOCKED}.{BLOCKED}4.160.26 google.ki
- {BLOCKED}.{BLOCKED}4.160.26 google.la
- {BLOCKED}.{BLOCKED}4.160.26 google.li
- {BLOCKED}.{BLOCKED}4.160.26 google.lv
- {BLOCKED}.{BLOCKED}4.160.26 google.ma
- {BLOCKED}.{BLOCKED}4.160.26 google.ms
- {BLOCKED}.{BLOCKED}4.160.26 google.mu
- {BLOCKED}.{BLOCKED}4.160.26 google.mw
- {BLOCKED}.{BLOCKED}4.160.26 google.nl
- {BLOCKED}.{BLOCKED}4.160.26 google.no
- {BLOCKED}.{BLOCKED}4.160.26 google.nr
- {BLOCKED}.{BLOCKED}4.160.26 google.nu
- {BLOCKED}.{BLOCKED}4.160.26 google.pl
- {BLOCKED}.{BLOCKED}4.160.26 google.pn
- {BLOCKED}.{BLOCKED}4.160.26 google.pt
- {BLOCKED}.{BLOCKED}4.160.26 google.ro
- {BLOCKED}.{BLOCKED}4.160.26 google.ru
- {BLOCKED}.{BLOCKED}4.160.26 google.rw
- {BLOCKED}.{BLOCKED}4.160.26 google.sc
- {BLOCKED}.{BLOCKED}4.160.26 google.se
- {BLOCKED}.{BLOCKED}4.160.26 google.sh
- {BLOCKED}.{BLOCKED}4.160.26 google.si
- {BLOCKED}.{BLOCKED}4.160.26 google.sm
- {BLOCKED}.{BLOCKED}4.160.26 google.sn
- {BLOCKED}.{BLOCKED}4.160.26 google.st
- {BLOCKED}.{BLOCKED}4.160.26 google.tl
- {BLOCKED}.{BLOCKED}4.160.26 google.tm
- {BLOCKED}.{BLOCKED}4.160.26 google.tt
- {BLOCKED}.{BLOCKED}4.160.26 google.us
- {BLOCKED}.{BLOCKED}4.160.26 google.vu
- {BLOCKED}.{BLOCKED}4.160.26 google.ws
- {BLOCKED}.{BLOCKED}4.160.26 google.co.ck
- {BLOCKED}.{BLOCKED}4.160.26 google.co.id
- {BLOCKED}.{BLOCKED}4.160.26 google.co.il
- {BLOCKED}.{BLOCKED}4.160.26 google.co.in
- {BLOCKED}.{BLOCKED}4.160.26 google.co.jp
- {BLOCKED}.{BLOCKED}4.160.26 google.co.kr
- {BLOCKED}.{BLOCKED}4.160.26 google.co.ls
- {BLOCKED}.{BLOCKED}4.160.26 google.co.ma
- {BLOCKED}.{BLOCKED}4.160.26 google.co.nz
- {BLOCKED}.{BLOCKED}4.160.26 google.co.tz
- {BLOCKED}.{BLOCKED}4.160.26 google.co.ug
- {BLOCKED}.{BLOCKED}4.160.26 google.co.uk
- {BLOCKED}.{BLOCKED}4.160.26 google.co.za
- {BLOCKED}.{BLOCKED}4.160.26 google.co.zm
- {BLOCKED}.{BLOCKED}4.160.26 google.com
- {BLOCKED}.{BLOCKED}4.160.26 google.com.af
Restart your machine
Scan your computer with your Trend Micro product for files detected as OSX_QHOST.A. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


