TSPY_TOXIFBNKR.A
Windows


Threat Type: Spyware
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This malware is involved in the global financial network transfer system Swift hacking incident of April-May 2016. It has certain routines that are tailored to take advantage of the SWIFT messaging network in order to steal funds.
To get a one-glance comprehensive view of the behavior of this Spyware, refer to the Threat Diagram shown below.
This spyware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
TECHNICAL DETAILS
Arrival Details
This spyware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Other Details
This spyware requires the following additional components to properly run:
- %Temp%\WRTU\ldksetup.tmp <- log file of malware's activity
- %Temp%\WRTU\LMutilps32.dat <- configuration file
- fpdfsdk.dll <- DLL required to convert PDF to XML and vice versa
(Note: %Temp% is the Windows temporary folder, where it usually is C:\Windows\Temp on all Windows operating system versions.)
It does the following:
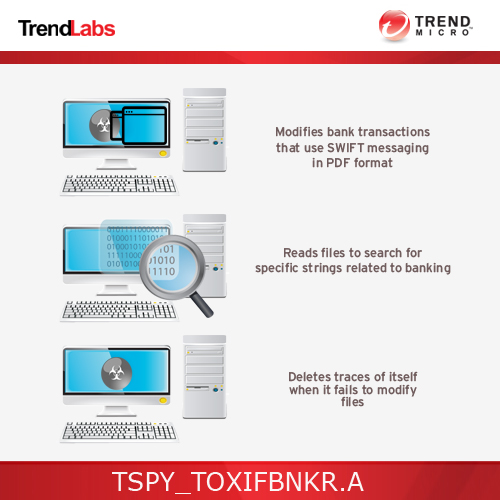
- Modifies bank transactions that use SWIFT Messaging in PDF format
- Triggers when opening a PDF file
- Reads PDF and converts it to XML then saves to a temporary file
- Reads the XML file and parses it to look for the following strings:
- ": Statement Line"
- "Closing Balance (Booked Funds)"
- "POS_TEMP"
- "Opening Balance"
- "Sender"
- ": Debit"
- ": Credit"
- " Debit"
- " Credit"
- "POS_PAGE_START"
- ": Closing Avail Bal (Avail Funds)"
- "Message Trailer"
- "Message Text"
- "Message Header"
- "Instance Type and Transmission"
- "pagecount"
- ": FIN 950" <- SWIFT statement message indicator
- Modify the XML file based on the configuration file
- Converts the modified XML file to PDF then replaces the original PDF file
- Opens modified PDF file with the legitimate Foxit Reader for the user to see
- Triggers when opening a PDF file
- Deletes traces of the malware's activities when modification fails
- Executes mspdclr.exe with the PDF file as parameter
- Deletes the original SWIFT message (in PDF format) file from the logs in the following paths:
- {LOG_PATH}\{SWIFT Code of Bank}{PrtIn/PrtOut}\{SWIFT Message File name}
- {LOG_PATH}\{SWIFT Code of Bank}{PrtIn/PrtOut}\{Year}\{Month}\{Day}\{SWIFT Message File name}
- Where:
LOG_PATH - path of the log files, retrieved from the config file
SWIFT Message File Name - PDF file that failed to be modified/loaded
- Where:
- Execute SQL commands to delete database logs
- The SQL command is executed using the following format:
sqlcmd.exe -S "{SQL_SERVER_PORT}" -E -Q "set nocount on;SQL_QUERY" -h -1 -W -o "OUTPUT_FILE" - Where:
SQL_SERVER_PORT - SQL server protocol retrieved from config file
OUTPUT_FILE - file to receive output from executed SQL command
SQL_QUERY - hardcoded SQL queries
- The SQL command is executed using the following format:
- Logs its activities in %Temp%\WRTU\ldksetup.tmp
(Note: %Temp% is the Windows temporary folder, where it usually is C:\Windows\Temp on all Windows operating system versions.)
NOTES:
This malware must be set to be the default application to handle PDF files or was manually selected by the user to open a PDF file for it to proceed with its malicious routine. Either it is manually registered by the user thinking it is the legitimate Foxit Reader or it has a dropper that registers it as part of its routine.
SOLUTION
Step 1
Before doing any scans, Windows XP, Windows Vista, and Windows 7 users must disable System Restore to allow full scanning of their computers.
Step 2
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 3
Search and delete this folder
- %Temp%\WRTU
Step 4
Scan your computer with your Trend Micro product to delete files detected as TSPY_TOXIFBNKR.A. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


