QAKBOT
Qakbot, Qbot
Windows


Threat Type: Worm
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
QAKBOT, also known as QBOT, is a banking Trojan discovered in 2007. Its main purpose is to steal banking credentials and other financial information. It continuously evolves with variants having worm-like capabilities, able to drop additional malware, log user keystrokes, and create a backdoor to compromised machines. It also uses advance or new techniques to evade detection and avoid reverse analysis.
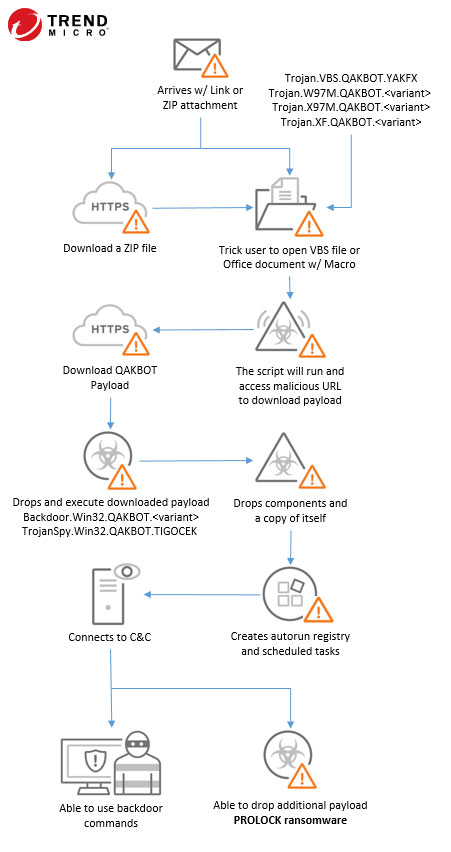
QAKBOT's new variants were found to be dropped by other malware such as EMOTET, or distributed via spam campaigns using context-aware spam or emails that are disguised as a reply to a previous email thread. The mail content has a link to download a ZIP file or may include the file as an attachment. The content of the compressed file is a VBS file or a weaponized MS Office document that drops and executes the QAKBOT payload. It proceeds to drop its component and a copy of itself on the compromised machine. It creates an autorun registry and scheduled task for its persistence. It also injects itself to an explorer.exe process. If it has successful connection to the C&C server, it is now able to send the stolen credentials information, able to extracts email threads from MS Outlook clients, remote access the compromised machine, and used to drop other malware such as PROLOCK ransomware.
Its behaviors include:
- Steals banking credentials and other financial information
- Uses anti-analysis and anti-debug techniques
- Drops copy of itself and components to compromised machine
- Creates autorun registry and scheduled task for persistence
- Deliver other malware payload such as PROLOCK ransomware
QAKBOT typically follows the infection chain depicted below: