YouTube Creators New Target of Info-Stealer Malware
August 23, 2023
Recently, there has been a spike in incidents involving information-stealing malware, commonly known as info-stealers, which uses cloud sharing services to attack victims. Threat actors have been leveraging this kind of attack in an innovative way through the distribution of spam emails, in this case by targeting content creators on YouTube.
A lot of YouTube creators provide their email address on their channel for business opportunities. Attackers see this as a chance to approach these creators by delivering a supposed to be business email pretending to be a known brand.

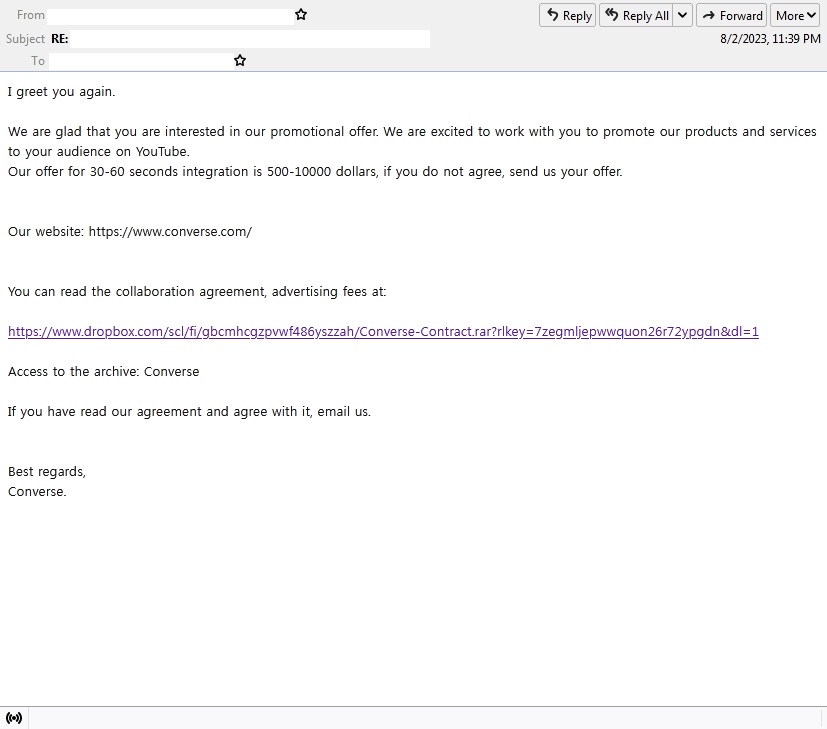
In the email, the subject line has 'Re:' to deceive the victim into thinking that they are receiving a reply to an email thread. The body of the email contains a brief detail on how the brand is thrilled to do a video advertisement collaboration with the YouTube creator to promote their products. And to further lure the victim, they include how much money the creator will earn if this collaboration happens.
The recipient will find a link in the latter part of the email deemed to be the agreement and advertising fees, together with the password for the archive.
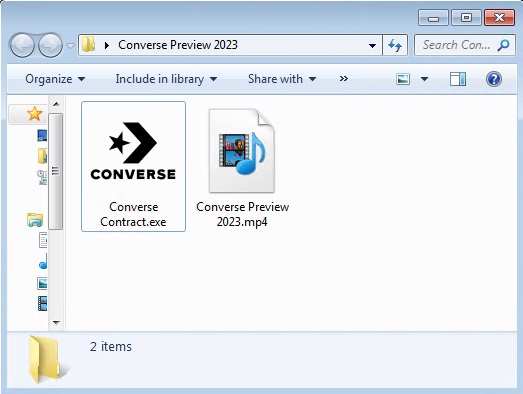
The link leads to Dropbox, where the victim will need to download an archive. Upon extraction, the archive contains a video that is related to the brand and an executable file. The file 'Converse Contract.exe' has a file size of more than 600 megabytes, which is unusual for a supposed contract. The use of insanely large executable files is one of the techniques used by info-stealer malware. It indicates that there is an unreasonable number of null bytes, which helps protect the file from being detected by antimalware products. The executable file is now detected by Trend Micro as TrojanSpy.Win32.VIDAR.SSBA. Vidar is a known info-stealer malware that operates as malware-as-a-service.
These spam emails are already blocked by Trend Micro Email Security Solutions. To alleviate the risk of falling for this kind of attack, users are advised to be cautious in downloading and opening suspicious files even if these came from seemingly known sources.
Related URLs: hxxps[://]www[.]dropbox[.]com/scl/fi/gbcmhcgzpvwf486yszzah/Converse-Contract[.]rar?rlkey=7zegmljepwwquon26r72ypgdn&dl=1 78. Malware Accomplice
SPAM BLOCKING DATE / TIME: August 23, 2023 GMT-8
TMASE INFO
- ENGINE:9.0.1004
- PATTERN:2.7832.000
