PHP_C99SHEL.SMC
Backdoor:PHP/C99shell.G(Microsoft), Backdoor.PHP.C99Shell.AQ(Fsecure), Malware_fam.B(Fortinet), PHP/Rst.AK(ESET)
Windows 2000, Windows Server 2003, Windows XP (32-bit, 64-bit), Windows Vista (32-bit, 64-bit), Windows 7 (32-bit, 64-bit)


Threat Type: Backdoor
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This malware is part of an attempted PHP backdoor attack via spam that took place on March 2014. Users affected by this malware would be shown a user interface of the malware's control panel, which shows its backdoor capabilities.
To get a one-glance comprehensive view of the behavior of this Backdoor, refer to the Threat Diagram shown below.

TECHNICAL DETAILS
Arrival Details
This malware arrives via the following means:
- embedded in mass-mailed email message.
- uploaded in a web server by malicious user
NOTES:
This malicious PHP script may be uploaded and installed on a web server by a remote malicious user via FTP after gaining access to the said server.
Once this PHP script is installed, the user may then launch a backdoor on the affected system.
Opening the page, the malicious user is shown the following GUI:
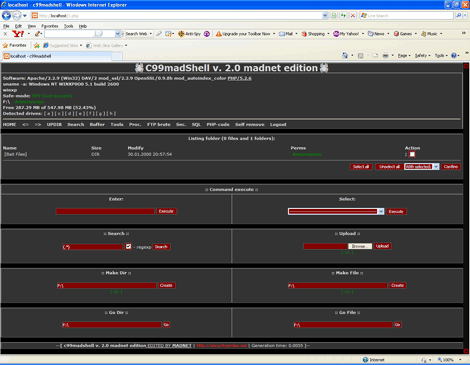
- Detect available drives on the system
- List files and folders
- Provide user full access to files and folders
- Search files with specific contents
- Create file and folder
- View file and folder information
- Execute shell commands
- View list of processes running on the system
- Bind standard input/output of the command interpreter to assigned TCP port
- Bind standard input/ output of the command interpreter to data from certain IRC server (Datapipe)
- Manage SQL databases
- Execute PHP code
- Remove itself from the server
- Scan FTP accounts for weak passwords using brute force and log them to file and e-mail
- Upload/dowload files to/from the web server
- Crack winnt passwords
SOLUTION
Step 1
Before doing any scans, Windows XP, Windows Vista, and Windows 7 users must disable System Restore to allow full scanning of their computers.
Step 2
Scan your computer with your Trend Micro product to clean files detected as PHP_C99SHEL.SMC. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


