TRICKBOT
Windows


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
Trickbot is a banking trojan used in attacks usually against small- and medium-sized businesses. It is designed to access online accounts, especially bank accounts, to obtain Personally Identifiable Information (PII). The obtained data is mostly used in identity fraud.
Some of Trickbot's modules steal credentials for remote computer access. Other variants target passwords used in Virtual Networking Computing (VCN), PuTTY, and Remote Desktop Protocol (RDP). The other modules perform tasks for stealing bank information, system or network reconnaissance, credential harvesting, and network propagation.
Trickbot discovered in 2019 has an additional spamming module known as TrickBooster. This module sends spam mails from infected computers to increase the spread of Trickbot infections. It then removes the sent messages from both Outbox and Sent item folders to avoid detection. It is commonly distributed in spearphishing attacks by using fake invoices and bank documents. It can also use a vulnerability in Server Message Block (SMB) to quickly propagate to other systems on the same network. Emotet, another widespread Trojan malware is also known to drop Trickbot as part of its secondary infection in Emotet-infected machines.
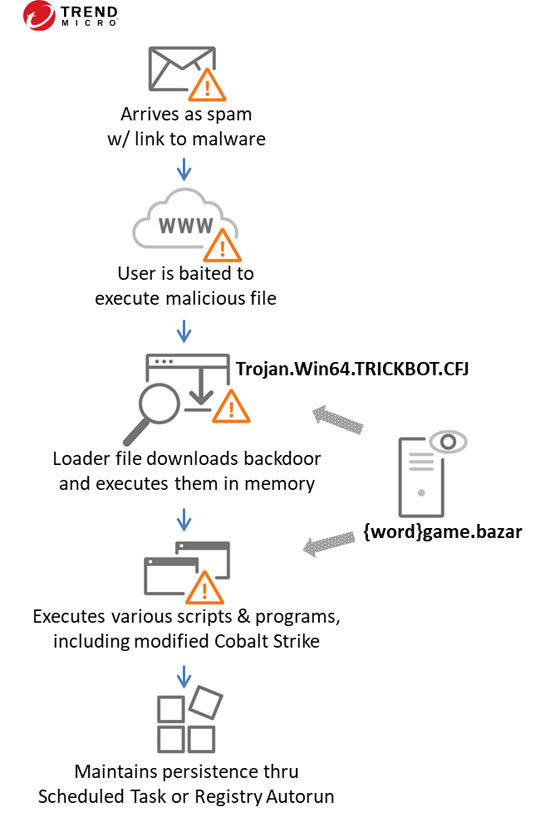
The same group behind Trickbot is believed to develop a new backdoor module called BazarBackdoor, as observed in 2020. This is based on spam origin, method of operation, and code overlap analysis. Both utilize the same crypter and email chains as previous Trickbot campaigns, as well as the Emercoin DNS resolution service for C&C server communication. The disguised file here is BazarBackdoor, named after its .bazar C&C DNS domains. This is a lightweight malware aimed to evade detection. Once executed, it connects to C&C and downloads its backdoor payload to memory. The backdoor’s goal is to execute binaries, scripts, and modules, kill processes and remove itself from the compromised machine.
It is capable of the following:
- Information Theft
- Rootkit
- Propagation
- Downloading files
- Stealth and fileless operation
- Backdoor commands
- Network compromise via Cobalt Strike
A typical Trickbot infection is below: