ANDROIDOS_KUNGFU.CI
Trojan:AndroidOS/Legana.A (Microsoft), Backdoor.AndroidOS.KungFu.hi (Kaspersky)
Android OS


Threat Type: Spyware
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This is the latest variant of DroidKungFu.
To get a one-glance comprehensive view of the behavior of this Spyware, refer to the Threat Diagram shown below.
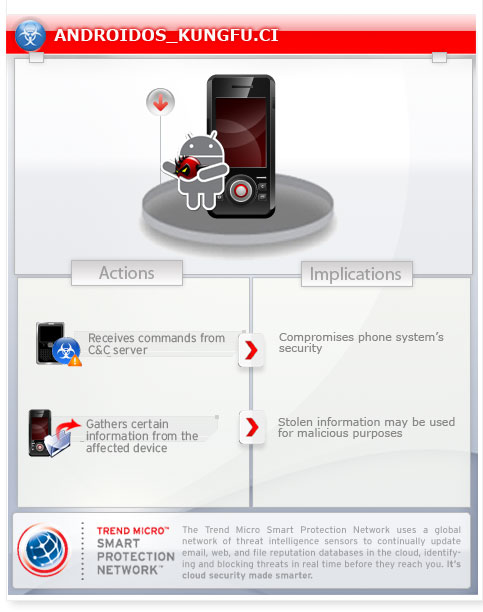
This spyware arrives via a Trojanized version of the Android applications OneKeyVpn (一键翻墙).
It gathers information such as affected phone brand and model, as well as the Android OS version installed. It also connects to C&C servers to receive commands.
This spyware may be manually installed by a user.
TECHNICAL DETAILS
Arrival Details
This spyware may be manually installed by a user.
NOTES:
It arrives via a Trojanized version of the Android applications OneKeyVpn (一键翻墙).
It gathers the following information and writes it to the file /system/etc/.rild_cfg:
- Android version string
- Brand name of the phone
- Device ID (IMEI for GSM)
- Model name of the phone
- SDK version of the framework
- The string cvpn072
It decrypts the file WebView.db.init in its assets folder in the malware APK file and saves the decrypted version as /system/etc/.dhcpcd and /system/xbin/ccb. It then changes the permission of the dropped file /system/xbin/ccb to full permissions to the file owner, and read and execute permissions for the others. It then executes the file /system/xbin/ccb.
It terminates the processes /system/bin/installd and /system/bin/dhcpcd. It then copies /system/bin/installd and /system/bin/dhcpcd to /system/bin/installdd and /system/bin/dhcpcdd, respectively, as backup. It then overwrites the original /system/bin/installd and /system/bin/dhcpcd with /system/xbin/ccb.
It creates the file /data/dhcpcd.lock as a marker to indicate that it has started to communicate with it's C&C server. It then connects to the following C&C servers to receive backdoor commands:
- http://{BLOCKED}h.{BLOCKED}-android.com:8511/search/
- http://{BLOCKED}h.{BLOCKED}8.com:8511/search/
- http://{BLOCKED}h.{BLOCKED}9.com:8511/search/
It may receive the following backdoor commands:
- Download a file
- Execute an application
- Install an APK file
- Update itself
SOLUTION
Step 1
Trend Micro Mobile Security Solution
Trend Micro Mobile Security Personal Edition protects Android smartphones and tablets from malicious and Trojanized applications. The App Scanner is free and detects malicious and Trojanized apps as they are downloaded, while SmartSurfing blocks malicious websites using your device's Android browser.
Download and install the Trend Micro Mobile Security App via Google Play.
Step 2
Remove unwanted apps on your Android mobile device
Did this description help? Tell us how we did.



