Ransom.MSIL.OSNO.AA
Trojan-Ransom.Osno (Ikarus); Trojan:Win32/Ymacco.AAC6 (Microsoft)
Windows


Threat Type: Ransomware
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It steals email account information. It steals certain information from the system and/or the user.
It encrypts files with specific file extensions. It encrypts files found in specific folders.
TECHNICAL DETAILS
Arrival Details
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Ransomware adds the following folders:
- %User Temp%\Dirs -> contains stolen filenames and folder names from targeted folders
- %User Temp%\{MD5 hash of Username + "Osno"}\{MD5 Hash of Machine Name + "-Logs"}
- %User Temp%\{Created folder}\Wallets -> stores stolen wallet files
- %User Temp%\{Created folder}\discord -> stores stolen discord files
- %User Temp%\{Created folder}\telegram{random number} -> stores stolen telegram files
- %User Temp%\{Created folder}\Jabber\Pidgin -> stores stolen Pidgin files
- %User Temp%\{Created folder}\Jabber\Psi+\profiles\default -> stores stolen Psi files
- %User Temp%\{Created folder}\Skype -> stores stolen Skype files
- %User Temp%\{Created folder}\ProtonVPN -> stores stolen Proton VPN files and config
- %User Temp%\{Created folder}\FTP\Total Commander -> stores Total Commander ftp config/ files
- %User Temp%\{Created folder}\Mega Limited\MEGAsync -> stores MEGAsync database files and config files
- %User Temp%\{Created folder}\Torrents -> stores stolen torrent files
- %User Temp%\{Created folder}\Steam -> stores stolen Steam files and credentials
- %User Temp%\{Created folder}\Steam\Apps
- %User Temp%\{Created folder}\Steam\ssnf -> stores copy of steam ssfn files
- %User Temp%\{Created folder}\Steam\configs -> stores stolen steam config files
- %User Temp%\{Created folder}\Uplay -> stores stolen Ubisoft/Uplay files
- %User Temp%\{Created folder}\Minecraft -> stores stolen Minecraft files
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
It drops the following files:
- %User Temp%\{Created folder}\screen.jpeg -> screenshot of the screen
- %User Temp%\{Created folder}\processes.txt -> list of all running processes
- %User Temp%\{Created folder}\Jabber\Pidgin\Pidgin.log -> stolen Pidgin credentials
- %User Temp%\{Created folder}\others.txt -> other application credentials/information
- %User Temp%\{Created folder}\Dirs\Desktop.txt
- %User Temp%\{Created folder}\Dirs\Documents.txt
- %User Temp%\{Created folder}\Dirs\Pictures.txt
- %User Temp%\{Created folder}\Dirs\Videos.txt
- %User Temp%\{Created folder}\Dirs\Startup.txt
- %User Temp%\{Created folder}\Dirs\Downloads.txt
- %User Temp%\{Created folder}\Dirs\Temp.txt
- %User Temp%\{Created folder}\Dirs\DRIVE-{removable drive letter}.txt
- %User Temp%\{Created folder}\Cookies.txt -> stores browser cookies
- %User Temp%\{Created folder}\Hardware & Soft.txt -> stores hardware and software specifications of the infected machine
- %User Temp%\{Created folder}\Steam\Apps\SteamApps.txt -> stores list of apps installed in the steam application of infected machine
- %User Temp%\{Created folder}\Steam\SteamInfo.txt -> stores steam saved passwords
- %User Temp%\{Created folder}\{MD5 hash of machine name}-mat-debug.tmp - zip file of %User Temp%\{Created folder}
- %Desktop%\Osno Decryptor.exe -> locks screen and displays ransom note
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %Desktop% is the current user's desktop, which is usually C:\Documents and Settings\{User Name}\Desktop on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\Desktop on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
It adds the following processes:
- "cmd.exe /C tasklist /FO TABLE > %User Temp%\{Created folder}\processes.txt
- "cmd.exe" /C chcp 65001 && netsh wlan show profile | findstr All
- %Desktop%\Osno Decryptor.exe
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %Desktop% is the current user's desktop, which is usually C:\Documents and Settings\{User Name}\Desktop on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\Desktop on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
Process Termination
This Ransomware terminates the following processes if found running in the affected system's memory:
- HTTPDebuggerSvc
- HTTPDebuggerUI
Information Theft
This Ransomware steals email account information.
It steals the following information:
- List of running processes
- Username
- Machine Name
- Directories and Subdirectories
- Wallets
- Screenshot of the screen
- Authy Desktop Files
- Voip information (Discord, Telegram, Jabber Pidgin and Psi, Skype)
- Cookies and Credentials from browsers
- VPN Credentials (ProtonVPN, HMA! Pro VPN, NordVPN)
- Ftp clients credentials (FileZilla, Total Commander)
- Megasync configuration/database files (.cfg and .db)
- Torrent files (uTorrent and Bittorrent)
- List of steam apps
- Steam credentials (stored in ssfn file)
- Steam Config file
- Minecraft files, versions, and installed mods
- Email files and passwords
- SMTP Email Address
- SMTP Server
- POP3 Server
- POP3 User Name
- SMTP User Name
- NNTP Email Address
- NNTP User Name
- NNTP Server
- IMAP Server
- IMAP User Name
- HTTP User
- HTTP Server URL
- POP3 User
- IMAP User
- HTTPMail User Name
- HTTPMail Server
- SMTP User
- POP3 Password2
- IMAP Password2
- NNTP Password2
- HTTPMail Password2
- SMTP Password2
- POP3 Password
- IMAP Password
- NNTP Password
- HTTPMail Password
- SMTP Password
- Date Infected
- Motherboard manufacturer
- Monitor Count
- Display Resolution
- HWID
- Processor (CPU)
- GPU
- Memory (RAM)
- Operating System
- Serial ID
- IP Address
- Country
- City
- Region
- ISP
- Timezone
- Installed AntiVirus
- Firewall
- List of Installed Applications
- User Privilege (isAdmin)
Stolen Information
This Ransomware sends the gathered information via HTTP POST to the following URL:
- https://api.telegram.org/bot ({BLOCKED}.154.167.220)
Other Details
This Ransomware connects to the following URL(s) to get the affected system's IP address:
- http://ip-api.com/xml/
It does the following:
- Uses an antidump function
- Targets the following wallets:
- Zcash
- Armory
- Bytecoin
- Jaxx
- Exodus
- Ethereum
- Electrum
- AtomicWallet
- Guarda
- Coinomi
- Copies Authy desktop files from the following folders:
- %Application Data%\Authy Desktop\Local Storage\leveldb
- Looks in these registries for the following wallets:
- Litecoin
- Dash
- Bitcoin
- Looks for voip files in the following folders:
- %Application Data%\discord\Local Storage\leveldb
- Looks for skype files in the following folders:
- %Application Data%\Microsoft\Skype for Desktop\Local Storage
- If OS is "Intel(R) Xeon(R)", plants RDP in the server
- Targets cookies and credentials from the following browsers:
- Chromium
- opera
- OperaGX
- Vivaldi
- Brave
- EdgeChromium
- Orbitum
- Amigo
- Yandex
- 360 Browser
- Comodo Dragon
- Mozilla Browsers
- Mozilla\Firefox
- Waterfox
- K-Meleon
- Thunderbird
- Comodo\IceDragon
- 8pecxstudios\Cyberfox
- NETGATE Technologies\BlackHaw
- Moonchild Productions\Pale Moon
- Notable Cookies targeted:
- mybbuser
- NetflixId
- xf_user
- breakingin_device_key
- breakingin_login_key
- breakingin_member_id
- sp_dc
- user_session
- SecureNetflixId
- shoppy_session
(Note: %Application Data% is the current user's Application Data folder, which is usually C:\Documents and Settings\{user name}\Application Data on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Roaming on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
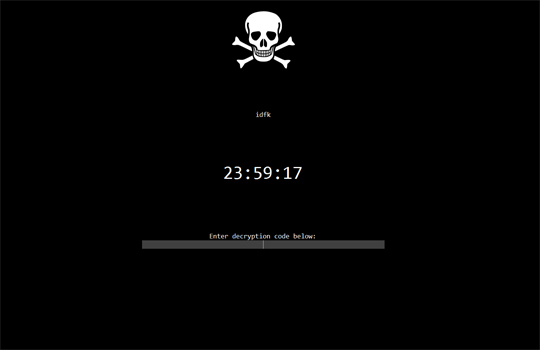
It locks the screen and displays the following image:
Ransomware Routine
This Ransomware encrypts files with the following extensions:
- .zip
- .ppt
- .doc
- .docx
- .rtf
- .jpg
- .jpeg
- .png
- .img
- .gif
- .mp3
- .mp4
- .mpeg
- .mov
- .avi
- .wmv
- .txt
- .html
- .php
- .js
- .css
- .odt
- .sqlite3
- .ink
- .ods
- .odp
- .odm
- .odc
- .odb
- .docm
- .wps
- .xls
- .xlsx
- .xlsm
- .xlsb
- .xlk
- .ppt
- .pptx
- .pptm
- .mdb
- .accdb
- .pst
- .dwg
- .dxf
- .dxg
- .wpd
- .wb2
- .mdf
- .psd
- .pdd
- .eps
- .ai
- .indd
- .cdr
- .jpe
- .log
- .py
- .dbf
- .ps1
- .dng
- .3fr
- .arw
- .srf
- .sr2
- .bay
- .crw
- .cr2
- .dcr
- .rwl
- .rw2
- .pyc
- .kdc
- .erf
- .mef
- .mrw
- .nef
- .nrw
- .orf
- .raf
- .raw
- .r3d
- .ptx
- .css
- .pef
- .srw
- .x3f
- .der
- .cer
- .crt
- .pem
- .pfx
- .p12
- .p7b
- .p7c
- .sqlite
- .js
- .rb
- .xml
- .wmi
- .sh
- .asp
- .aspx
- .plist
- .sql
- .vbs
- .litesql
- .dotx
- .db3
- .backup
- .xlm
- .rtf
- json
- .lua
- .tiff
- .tif
- csproj
- .sln
- .crt
- .csv
- .flv
- .vlf
- .rar
- .7zip
- .acc
- .lnk
- .cs
- .h
- .cpp
- .c
- .sg
- mid
- .wav
- .7z
- .exe
- .db
It encrypts files found in the following folders:
- %Desktop%
- %User Profile%\Documents
- %Application Data%
- %User Profile%\Pictures
- %User Profile%\Music
- %User Profile%\Videos
- Other Drives
(Note: %Desktop% is the current user's desktop, which is usually C:\Documents and Settings\{User Name}\Desktop on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\Desktop on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %User Profile% is the current user's profile folder, which is usually C:\Documents and Settings\{user name} on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name} on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %Application Data% is the current user's Application Data folder, which is usually C:\Documents and Settings\{user name}\Application Data on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Roaming on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
It appends the following extension to the file name of the encrypted files:
- .osnoed
SOLUTION
Step 1
Trend Micro Predictive Machine Learning detects and blocks malware at the first sign of its existence, before it executes on your system. When enabled, your Trend Micro product detects this malware under the following machine learning name:
- Troj.Win32.TRX.XXPE50FFF038
Step 2
Before doing any scans, Windows 7, Windows 8, Windows 8.1, and Windows 10 users must disable System Restore to allow full scanning of their computers.
Step 3
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 4
Restart in Safe Mode
Step 5
Search and delete this file
Step 6
Search and delete this folder
- %User Temp%\Dirs -> contains stolen filenames and folder names from targeted folders
- %User Temp%\{MD5 hash of Username + "Osno"}\{MD5 Hash of Machine Name + "-Logs"}
- %User Temp%\{Created folder}\Wallets -> stores stolen wallet files
- %User Temp%\{Created folder}\discord -> stores stolen discord files
- %User Temp%\{Created folder}\telegram{random number} -> stores stolen telegram files
- %User Temp%\{Created folder}\Jabber\Pidgin -> stores stolen Pidgin files
- %User Temp%\{Created folder}\Jabber\Psi+\profiles\default -> stores stolen Psi files
- %User Temp%\{Created folder}\Skype -> stores stolen Skype files
- %User Temp%\{Created folder}\ProtonVPN -> stores stolen Proton VPN files and config
- %User Temp%\{Created folder}\FTP\Total Commander -> stores Total Commander ftp config/ files
- %User Temp%\{Created folder}\Mega Limited\MEGAsync -> stores MEGAsync database files and config files
- %User Temp%\{Created folder}\Torrents -> stores stolen torrent files
- %User Temp%\{Created folder}\Steam -> stores stolen Steam files and credentials
- %User Temp%\{Created folder}\Steam\Apps
- %User Temp%\{Created folder}\Steam\ssnf -> stores copy of steam ssfn files
- %User Temp%\{Created folder}\Steam\configs -> stores stolen steam config files
- %User Temp%\{Created folder}\Uplay -> stores stolen Ubisoft/Uplay files
- %User Temp%\{Created folder}\Minecraft -> stores stolen Minecraft files
Step 7
Restart in normal mode and scan your computer with your Trend Micro product for files detected as Ransom.MSIL.OSNO.AA. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Step 8
Restore encrypted files from backup.
Did this description help? Tell us how we did.