By Alex Y. Chen and York Li
CAPTCHA, which stands for Completely Automated Public Turing test to tell Computers and Humans Apart, plays a crucial role in enhancing security measures and preventing unauthorized access. It functions as a challenge-response mechanism designed to differentiate between automated bots and human users.
CAPTCHA technology has advanced remarkably in recent years, so much so that many service providers offer free CAPTCHA tools to protect websites from cyberattacks. However, malicious actors have started using CAPTCHA authentication services offered by phishing websites to evade detection. Since CAPTCHA is designed to block automated bots, these services make the detection of phishing attempts more challenging.
Consequently, traditional detection methods have become inadequate in tackling current needs. This blog entry discusses how Trend Micro addresses this challenge through a platform anchored on behavior-based AI protection technology to detect phishing websites as an effective countermeasure against more advanced evasion techniques.
CAPTCHA evasion techniques for phishing
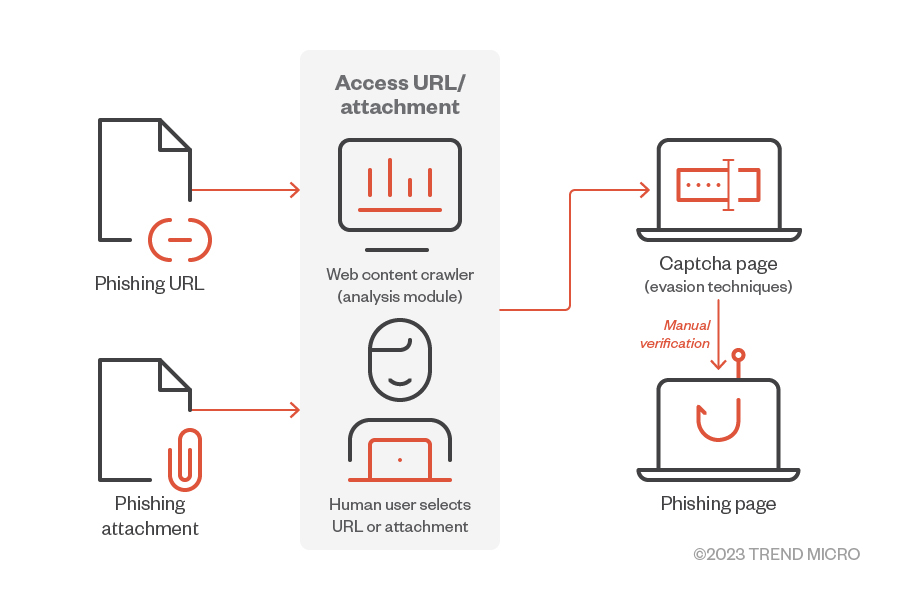
Figure 1. CAPTCHA evasion techniques for phishing
In the past, crawlers from an analysis module could access the content of phishing websites, allowing for detection based on specific features and metadata associated with the website content. However, with the introduction of CAPTCHA, traditional methods have not been able to detect many crucial clues and information, thus rendering existing solutions ineffective.
In the next section, we provide some cases that show how phishing websites use CAPTCHA evasion techniques.
- Phishing mail samples
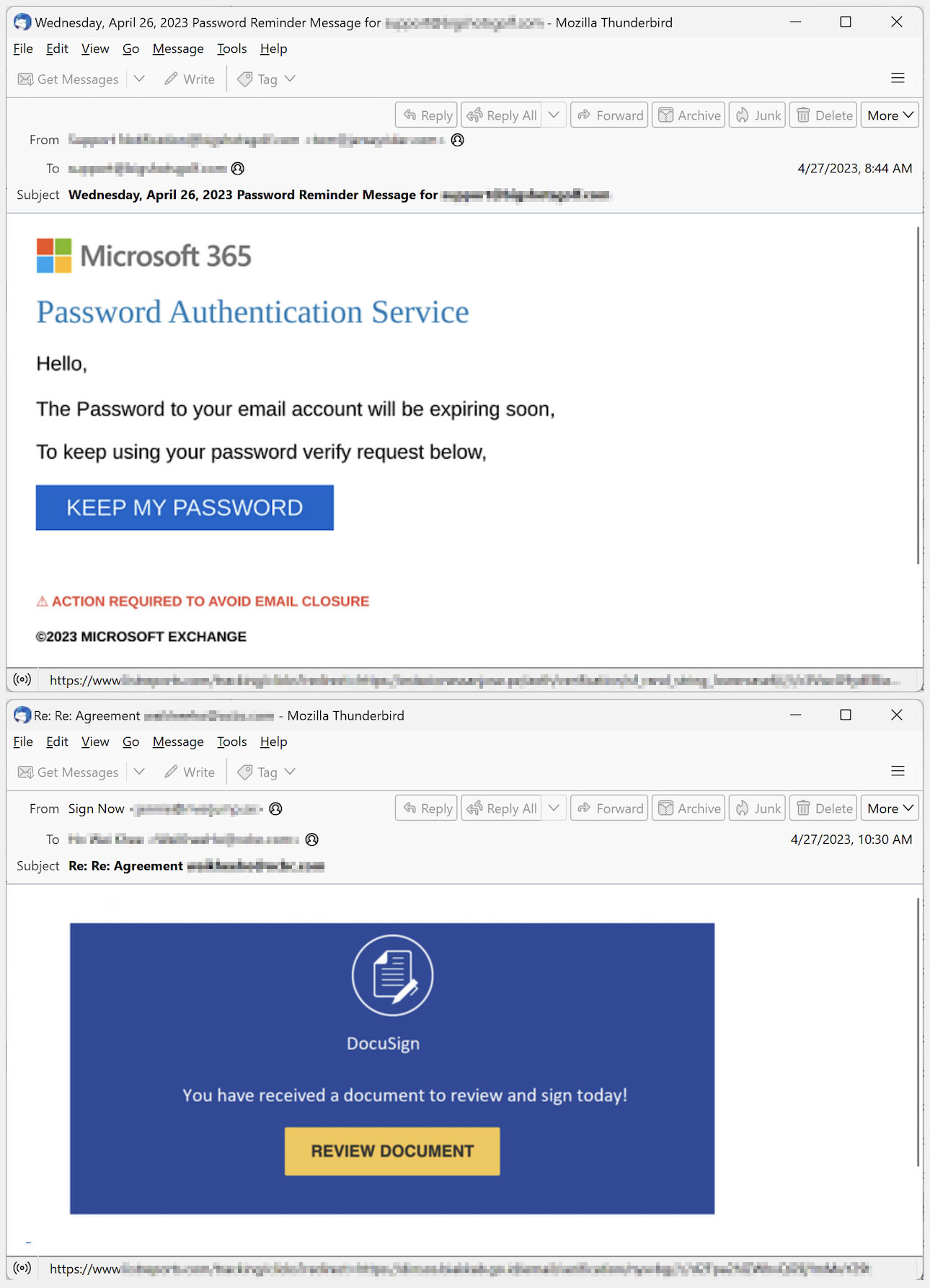
Figure 2. Example of a phishing email using malicious URLs in the email copy
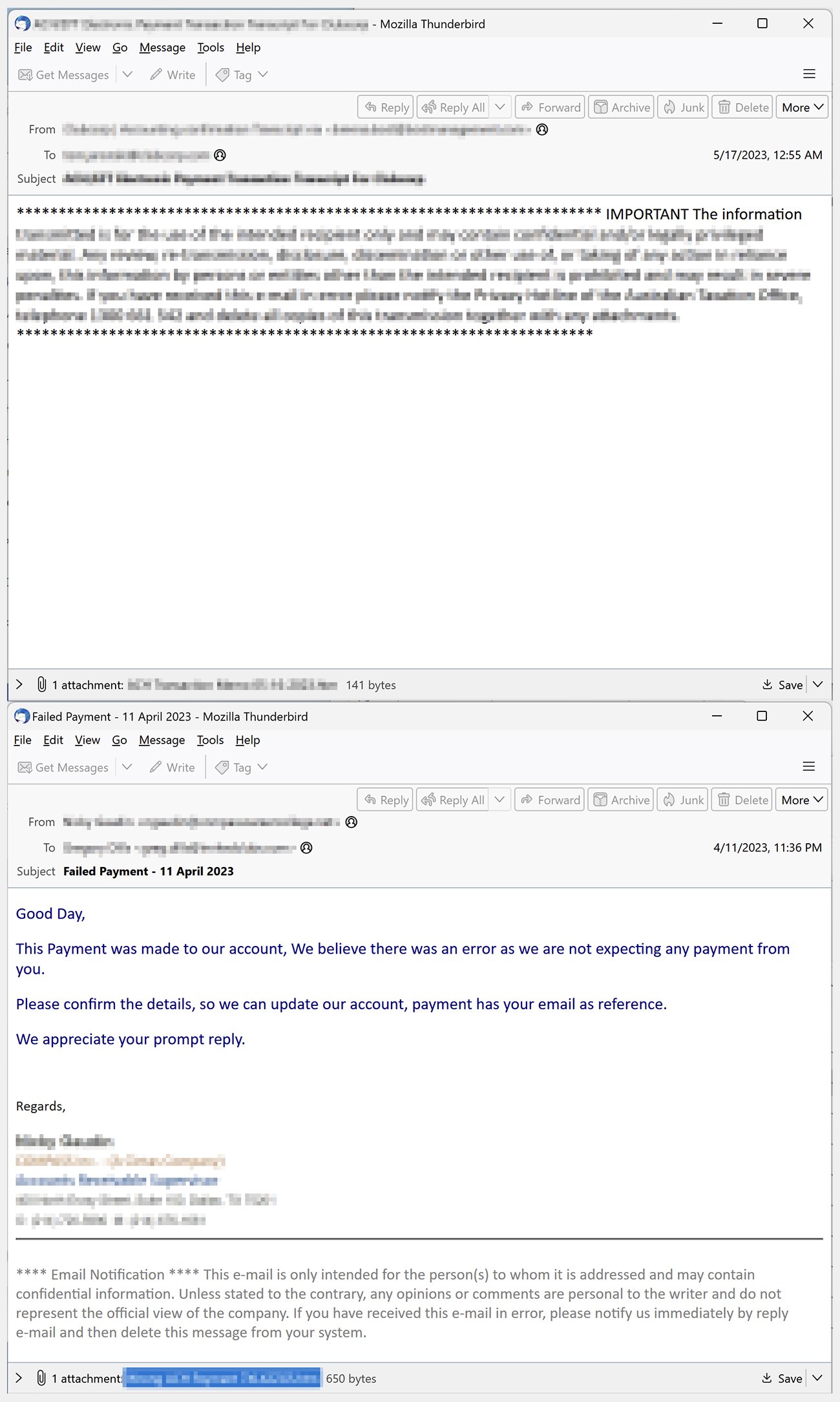
Figure 3. Examples of phishing emails using malicious URLs as attachments
We’ve observed that this type of phishing link is typically disseminated through email, using enticing content that often mimics notifications from well-known websites and services. We’ve also seen phishing emails that include fake discussion threads within an email chain to give them a semblance of authenticity. Malicious actors embed phishing links in different parts of the email, such as in the body, within images, or attached as files rendered in formats like HTML, PDF, and ZIP, among others.
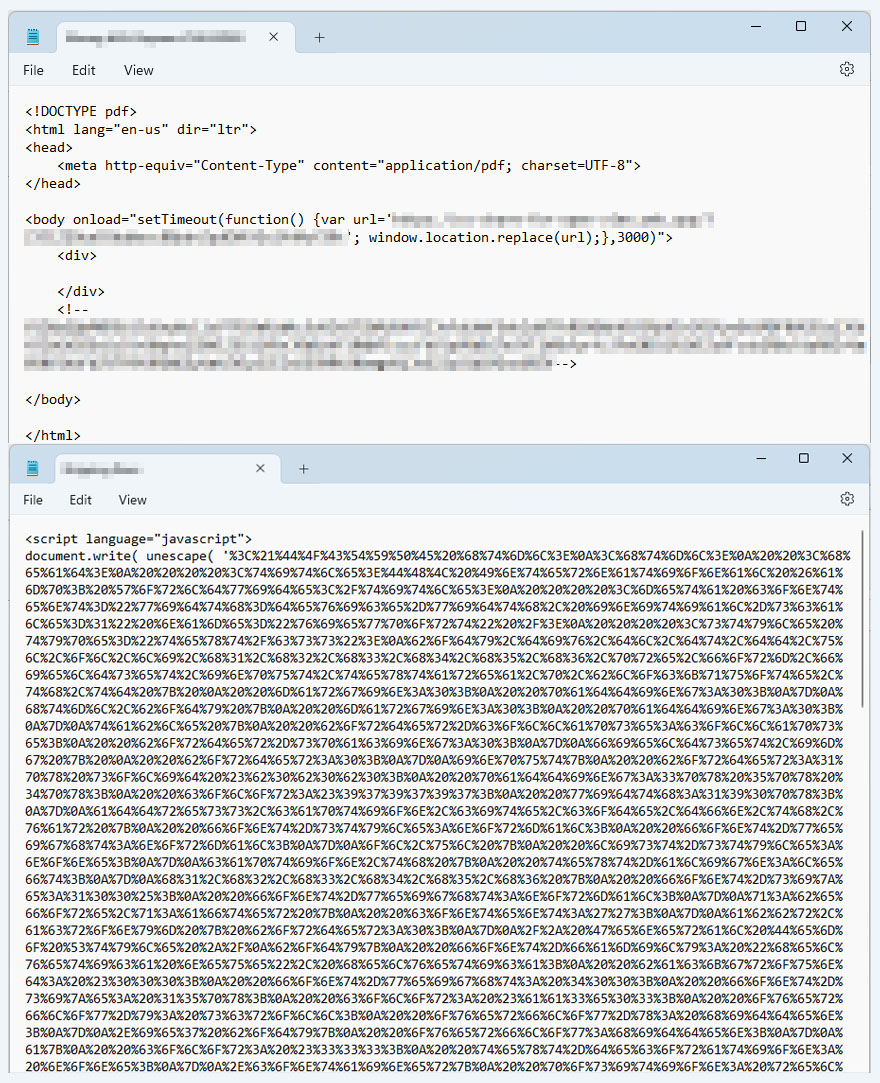
Figure 4. Examples of phishing emails using malicious URLs in their HTML attachment
We’ve observed malicious actors not only employing different methods of attaching files to evade detection but also using unique file extensions and employing content obfuscation techniques. HTML attachments offer users more flexibility, making them a common choice for hackers aiming to obfuscate content or use JavaScript (JS) code to dodge detection. While these techniques have minimal impact on user experience, they nonetheless present significant challenges for traditional detection mechanisms.
- CAPTCHA pages
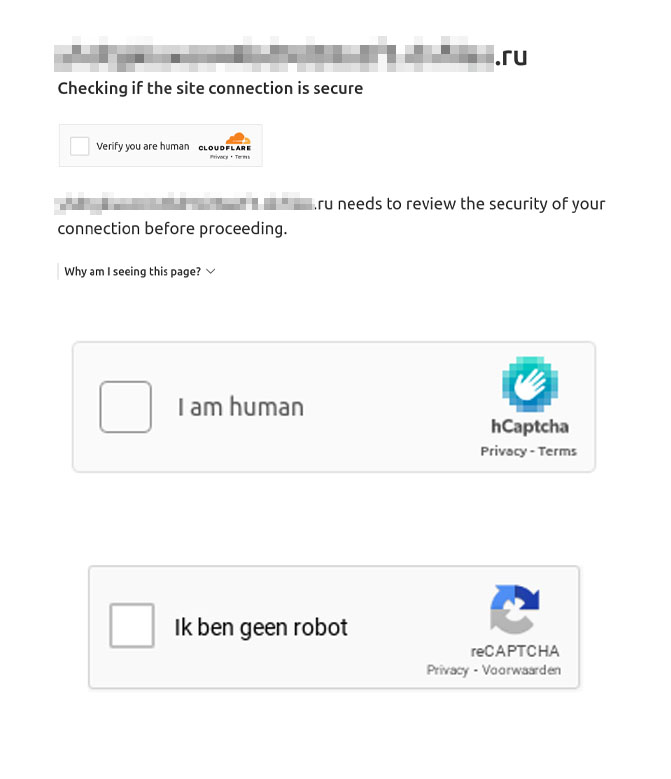
Figure 5. Sample emails using CAPTCHA in webpages
There are many kinds and forms of CAPTCHA available. Traditional CAPTCHA methods use text or image recognition for verification. However, a new kind of CAPTCHA utilizes multiple data points to comprehensively assess if further manual verification is necessary. These more recent CAPTCHA systems are not any more challenging than prior systems and do not require additional actions. When entering the manual verification stage, users simply need to select a button to pass. However, these new verification systems pose significant challenges for traditional phishing detection mechanisms as they can get stuck on the webpages and be unable to access any page content information.
- Phishing pages
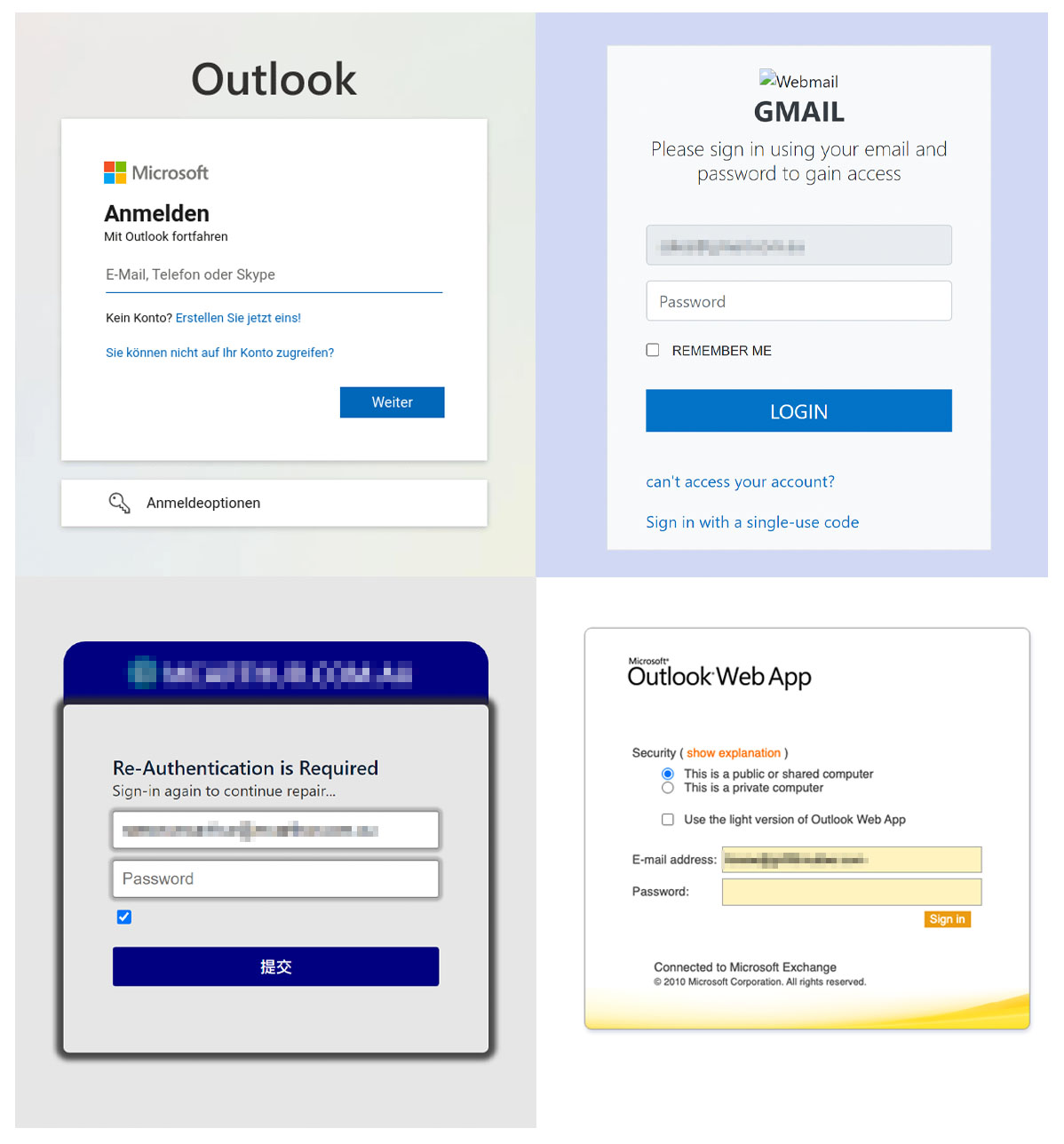
Figure 6. Sample phishing pages
After a user gets through the CAPTCHA phase, the phishing website page is displayed, often resembling familiar pages such as the login pages for Microsoft, Webmail, and the Outlook web app, among others. Usually, these types of phishing websites use methods like those that use traditional phishing methods.
Challenges with detection
The biggest challenge of this attack technique for security products that perform analysis module lies in the fact that humans can easily pass the verification stage, while detection technologies for attacks that use CAPTCHA evasion techniques are often hindered from doing so by several factors.
These types of CAPTCHA authentication services are typically offered for free and might even be integrated with the Content Delivery Network (CDN) features of service providers. As a result, CAPTCHA is commonly found in legitimate websites and the contents on CAPTCHA pages are deemed legitimate, making it difficult for detection technologies to distinguish between CAPTCHA on legitimate websites and CAPTCHA on malicious ones.
Malicious actors are employing an increasingly diverse range of evasion techniques. Traditional detection methods that rely solely on a single aspect for analysis increase their likelihood of rendering themselves ineffective. Such is the case for detection methods that only take into account URL features or webpage content analysis from Trend Micro Web Reputation Services and those that base their detection on email behavior analysis from Trend Micro™ Email Reputation Service. Reliance on a single aspect for detection not only creates blind spots but also increases the risk of false alarms, leading to inaccurate triggering of detection mechanisms.
Detections of phishing attempts using malicious URLs are on the rise
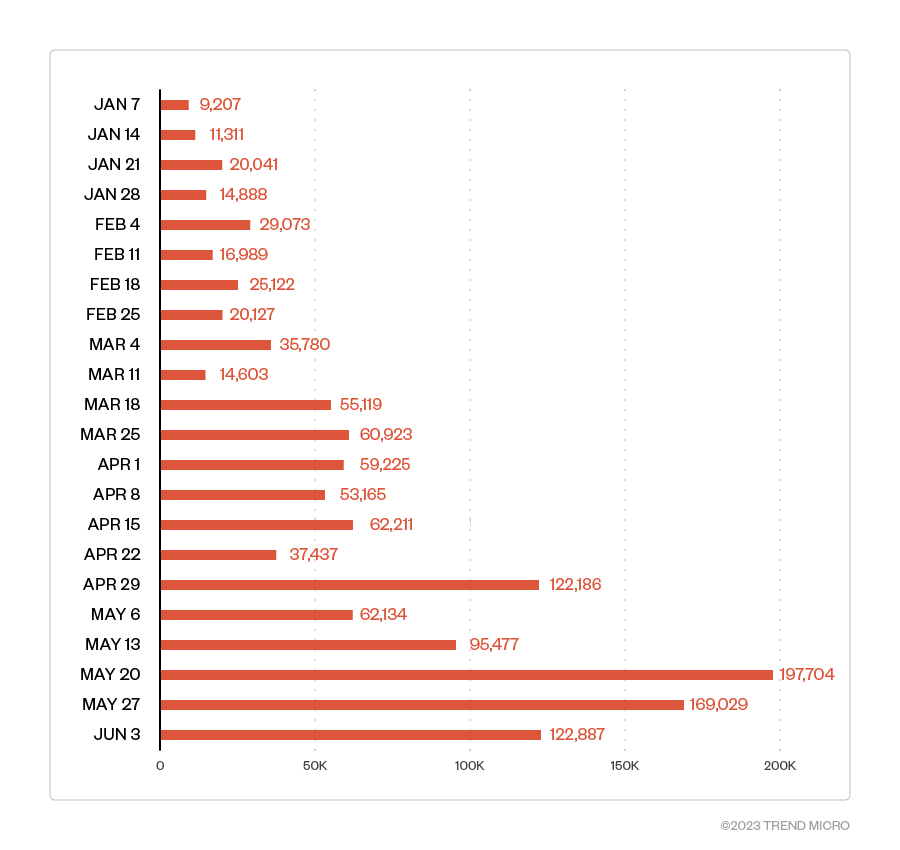
Figure 7. Detections of phishing attempts that used CAPTCHA evasion techniques with embedded malicious URLs
Our monitoring from January 1 to June 3, 2023 shows that there has been a significant increase in the evasion techniques used in CAPTCHA for phishing websites. Notably, the usage in the second quarter was more than double compared to the first quarter. Hackers are taking advantage of the difficulty in detection and have thus been extensively abusing CAPTCHA authentication services for their ill intent.
Behavior-Based AI protection
As mentioned earlier, a method’s reliance on a single aspect for detection is insufficient to address current threats. Trend combines various aspects, including product features, email, web, and file threat analysis, to analyze user behavior when receiving emails and examine a range of information within emails. As a result, the confidence and accuracy of detection can be significantly improved by integrating data from multiple aspects and employing AI-based analysis and detection.
Aside from real-time detection, the back-end system that handles undetected emails with malicious URLs or attachments leverages big data analysis to incorporate more dimensions of information and features for advanced analysis and detection. If malicious emails are discovered subsequently, Trend Micro™ Retro Scan™ technology is utilized to recall those emails, minimizing the impact of malicious threats.
Behavior-based AI protection is not limited to CAPTCHA evasion techniques for phishing. In an era of rapidly evolving and diverse threat techniques, this technology provides smarter, faster, and more comprehensive solutions to address a wide range of threats, ensuring real-time protection for users.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Artículos Recientes
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One