ANDROIDOS_FAKE.DQ
Premium Service Abuser
Android OS


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
This Android malware poses as the Farm Frenzy game to lure users into downloading its copy on their Android-based phones.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
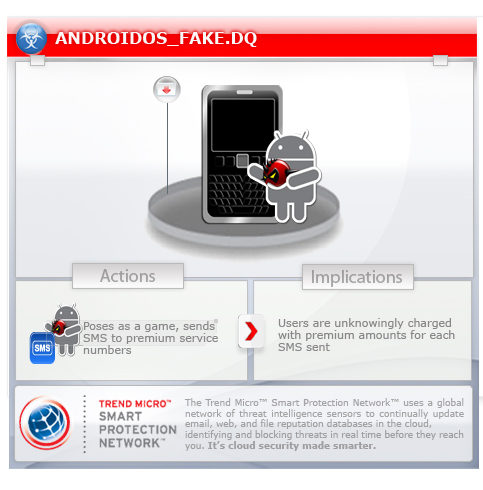
When users run the app and click on the first button, it sends an SMS to a premium service based on the network operator. This routine bills the affected user unknowingly.
This Trojan may be manually installed by a user.
TECHNICAL DETAILS
Arrival Details
This Trojan may be unknowingly downloaded by a user while visiting the following malicious websites:
- {BLOCKED}ndroida.org
It may be manually installed by a user.
NOTES:
This malicious app poses as the Farm Frenzy game.
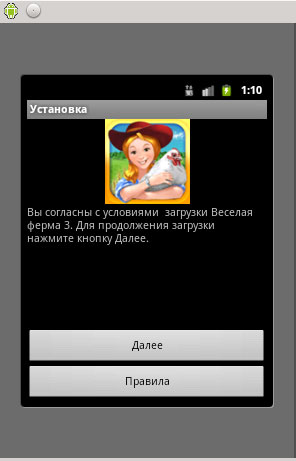
When users run the app on their phones and click on the first button, it sends an SMS to the following premium service numbers that are based on the network operator:
- 8883
- 8887
- 6151
- 1
- 2855
- 9151
- 9685
- 9684
The screen then displays a Russian message:
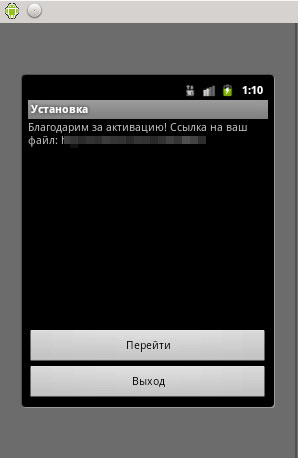
When users clicked on the first button/option, it allows this malware to open their phone's browser and connect to the following URL:
- http://{BLOCKED}te.net/?u=848053
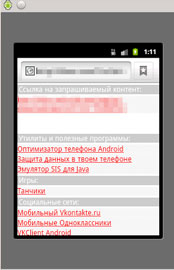
It then redirects users to the following URL:
- http://{BLOCKED}o.com/?u=http%3A%2F%2Fdlya-androida.org%2Fengine%2Fdownload.php%3Fid%3D199
SOLUTION
Step 1
Scan your computer with your Trend Micro product to delete files detected as ANDROIDOS_FAKE.DQ. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Step 2
Remove unwanted apps on your Android mobile device
Did this description help? Tell us how we did.


