TROJ_ALUREON.ALW
Windows 2000, Windows XP, Windows Server 2003


Threat Type: Trojan
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This Trojan attempts to overwrite the Master Boot Record (MBR) with its codes. However, this may cause problems in the system such as boot failure.
It attempts to perform certain queries on the affected system.
It creates several components in a hidden device, depending on whether the machine is 32 or 64 bit.
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It does not have any propagation routine.
It also has rootkit capabilities, which enables it to hide its processes and files from the user.
It does not have any information-stealing capability.
It deletes the initially executed copy of itself.
TECHNICAL DETAILS
Arrival Details
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Trojan drops the following copies of itself into the affected system:
- %User Temp%\Realtek_AC97.exe
- %User Temp%\{random}.exe
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000, XP, and Server 2003, or C:\Users\{user name}\AppData\Local\Temp on Windows Vista and 7.)
Its DLL component is injected to the following process(es):
- svchost.exe
Propagation
This Trojan does not have any propagation routine.
Rootkit Capabilities
This Trojan also has rootkit capabilities, which enables it to hide its processes and files from the user.
Information Theft
This Trojan does not have any information-stealing capability.
Other Details
This Trojan deletes the initially executed copy of itself
NOTES:
It attempts to overwrite the Master Boot Record (MBR) with its codes to automatically execute its components upon system boot.
It attempts to perform the following queries on the affected system:
- SELECT * FROM Win32_BIOS WHERE Manufacturer LIKE "%Xen%"
- SELECT * FROM Win32_BIOS WHERE Manufacturer LIKE "%QEMU%"
- SELECT * FROM Win32_BIOS WHERE Manufacturer LIKE "%Bochs%"
- SELECT * FROM Win32_DiskDrive WHERE Model LIKE "%Xen%"
- SELECT * FROM Win32_DiskDrive WHERE Model LIKE "%QEMU%"
- SELECT * FROM Win32_DiskDrive WHERE Model LIKE "%Bochs%"
- SELECT * FROM Win32_DiskDrive WHERE Model LIKE "%Red Hat%"
- SELECT * FROM Win32_SCSIController WHERE Name LIKE "%Citrix%"
- SELECT * FROM Win32_SCSIController WHERE Manufacturer LIKE "%Xen%"
- SELECT * FROM Win32_SCSIController WHERE Manufacturer LIKE "%Red Hat%"
- SELECT * FROM Win32_Processor WHERE Name LIKE "%QEMU%"
- SELECT * FROM Win32_Process WHERE Name = "CaptureClient.exe"
These queries are used by the malware to identify if it is running under a sandbox or virtual machine.
It creates the following components in a hidden file system, depending on whether the machine is 32 or 64 bit:
- cmd32.dll / cmd64.dll - TROJ_ALUREON.ALW
- dbg32 / dbg64 - TROJ_TDSS.ADH, TROJ_TDSS.BME
- drv32.sys / drv64.sys - TROJ_ALUREON.ALW
- ldr32.exe / ldr64.exe - TROJ_TDSS.BMG, TROJ_TDSS.BMH
- main - configuration file
This malware connects to the following URLs to download additional components:
- http://{BLOCKED}don-{random numbers}.com/cat/v3
- http://{BLOCKED}at-{random numbers}.com/cat/v3
- http://{BLOCKED}en-{random numbers}.com/cat/v3
- http://{BLOCKED}ck-{random numbers}.com/cat/v3
- http://{BLOCKED}ila.com/cat/v3
- http://{BLOCKED}zuck.com/cat/v3
- http://{BLOCKED}etclick.com/cat/v3
Note that the URLs generated may change from time to time.
The malware appends the following to the URLs above:
- /files/mods/cmd32
- /files/mods/bbr232
- /files/mods/serf332
A sample download URL would be:
- http://{BLOCKED}852171.com/cat/v3/files/mods/cmd32
The downloaded files are encrypted. After decryption, the downloaded files bbr232 and serf332 are then injected into any of the following processes:
- iexplore.exe
- explorer.exe
- firefox.exe
- safari.exe
- chrome.exe
- WebKit2WebProce
- WebKit2WebProc
It stores its backup configuration files in images hosted at the following legitimate websites:
- http://{BLOCKED}yq.wordpress.com/
- http://{BLOCKED}aqevi.livejournal.com/
- http://{BLOCKED}vubi.wordpress.com/
- http://{BLOCKED}ejuq.livejournal.com/
- http://{BLOCKED}vesoja.wordpress.com/
The malware downloads the pages of the URLs above and then searches for the following tags:
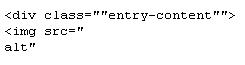
It then extracts the "jpg" file pointed to by the "img src" tag, and downloads the JPG file. The downloaded JPEGs contain encrypted configuration files which include details about the malware's modules, servers, and backup configuration URLs.
The downloaded files are all stored in its hidden file system.
SOLUTION
Step 1
Before doing any scans, Windows XP, Windows Vista, and Windows 7 users must disable System Restore to allow full scanning of their computers.
Step 2
Restore your system's Master Boot Record (MBR)
To restore your system's Master Boot Record (MBR):
• On Windows 2000, XP, and Server 2003:
- Insert your Windows Installation CD into your CD drive then restart your computer.
- When prompted, press any key to boot from the CD.
- On the Main Menu, type r to enter the Recovery Console.
(Note for Windows 2000: After pressing r, type c to choose the Recovery Console on the repair options screen.) - Type the number that corresponds to the drive and folder that contains Windows (usually C:\WINDOWS) and press Enter.
- Type your Administrator password and press Enter.
- In the input box, type the following then press Enter:
fixmbr {affected drive} - Type exit and press Enter to restart the system normally.
• On Windows Vista and 7:
- Insert your Windows Installation DVD into the DVD drive, then press the restart button on your computer.
- When prompted, press any key to boot from the DVD.
- Depending on your Windows Installation DVD, you might be required to choose the installation language. On the Install Windows window, choose your language, locale, and keyboard layout or input method. Click Repair your computer.
- Select Use recovery tools that can help fix problems starting Windows. Select your installation of Windows. Click Next.
- If the Startup Repair window appears, click Cancel, Yes, then Finish.
- In the System Recovery Options menu, click Command Prompt.
- In the Command Prompt window, type the following then press Enter:
BootRec.exe /fixmbr - Type exit and press Enter to close the Command Prompt window.
- Click Restart to restart your computer normally.
Step 3
Scan your computer with your Trend Micro product to delete files detected as TROJ_ALUREON.ALW. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


