Malware in Email Threads: Info Stealers being delivered using Cloud Sharing Services
August 23, 2023
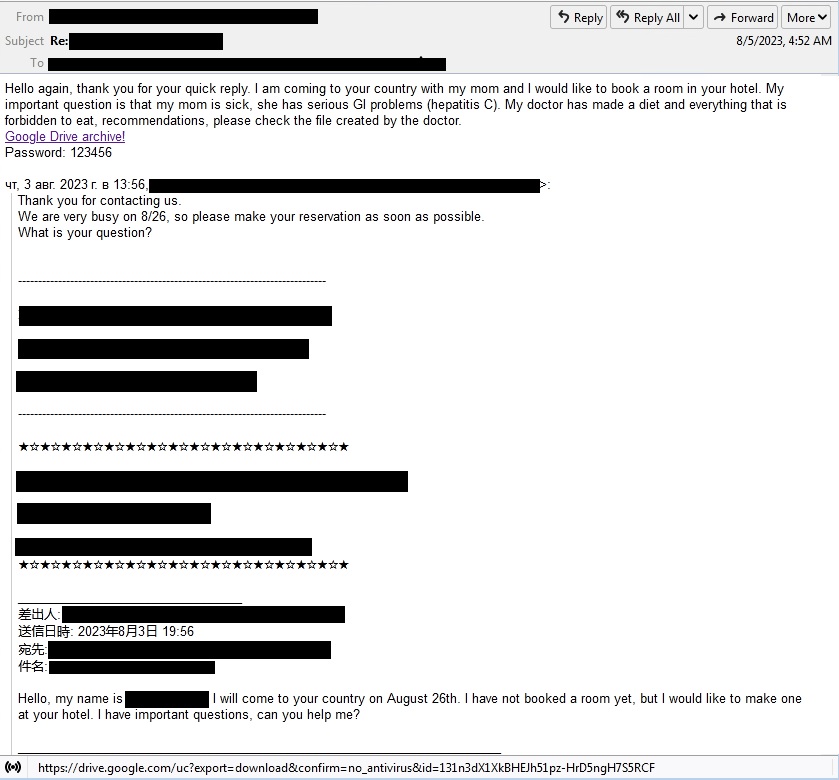
The abuse of cloud sharing services such as Google Drive and Google Docs was last seen in March 2023, in which threat actors targeted Latin American countries, distributing payment-related emails containing malware such as REMCOSRAT. This time, we observed a spam email that initiated a discussion about hotel reservations.
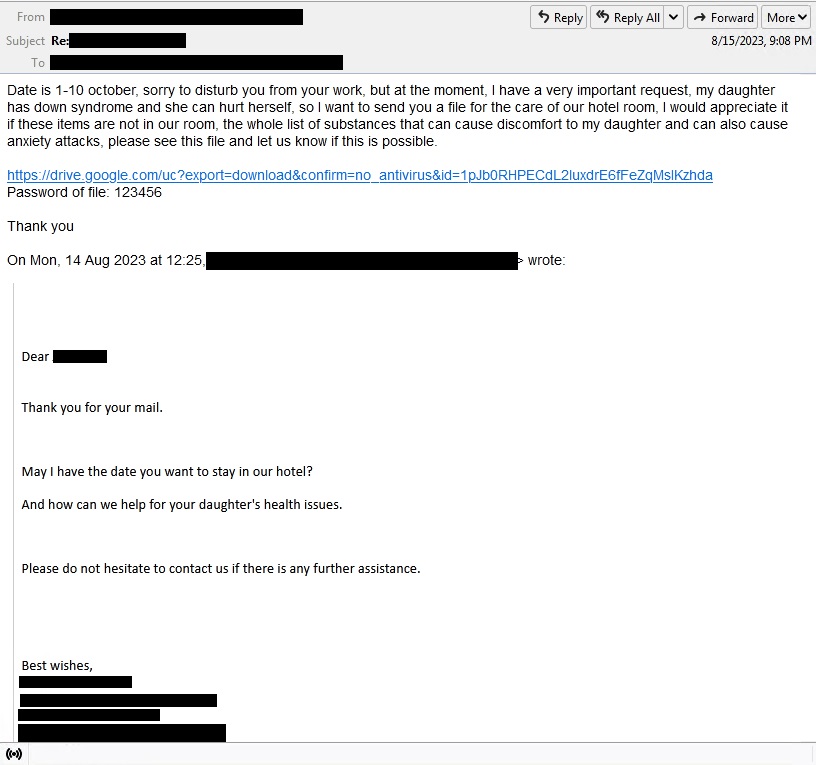
As seen in the email, a booking request is initiated to start an email thread. When the victim replies to the email, the malicious actor will claim that a family member has a medical concern and that it will need a special request from the hotel, urging the victim to open a Google Drive link along with the password to decompress the downloaded archive.
Upon investigating the downloaded archives, the sample contained a huge, bloated executable file with a file size reaching more than 600 MB, along with a video file to appear more legitimate. Further checking of the executable file shows that the samples were padded by null bytes:

The inflated executable file that is downloaded from the link contains known malware families, including but not limited to NEGASTEAL which is known to be an info stealer.
These spam emails are already blocked by Trend Micro Email Security Solutions, but to further protect against this kind of threat, be careful opening unusual files downloaded from a link.
Related URLs:
hxxps[://]drive[.]google[.]com/uc?export=download&confirm=no_antivirus&id=131n3dX1XkBHEJh51pz-HrD5ngH7S5RCF = 78. Malware Accomplice
SPAM BLOCKING DATE / TIME: August 23, 2023 GMT-8
TMASE INFO
- ENGINE:9.0.1004
- PATTERN:2.7832.000
