JS_ANDRSOPEXP.A
Spying Tool
Android OS


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
This threat is related to attacks that used Android Same Origin Policy (SOP) vulnerability to target Facebook users.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
This Trojan takes advantage of software vulnerabilities to propagate across networks. It propagates via social networking sites by sending malicious links to all the user's contacts. The said links point to a remote URL where a copy of the worm may be downloaded.
TECHNICAL DETAILS
Propagation
This Trojan takes advantage of the following software vulnerabilities to propagate across networks:
It propagates via social networking sites by sending malicious links to all the user's contacts. The said links point to a remote URL where a copy of the worm may be downloaded.
NOTES:
This Android malware does the following:
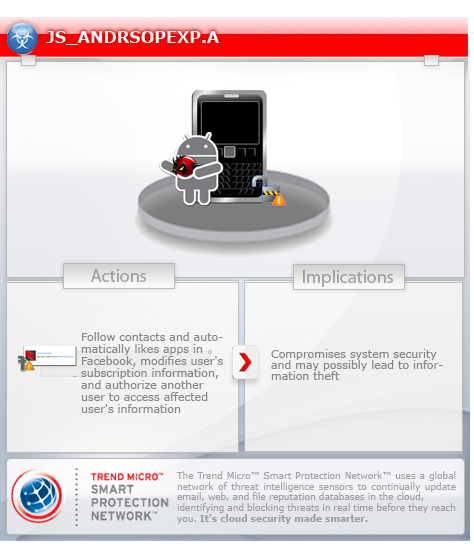
- Automatically follow contacts in Facebook
- Automatically likes apps in Facebook
- Modify user's subscription information
- Authorize another user to access affected user's information such as friends list, likes, friends' likes, basic info, etc.
SOLUTION
Trend Micro Mobile Security Solution
Trend Micro Mobile Security Personal Edition protects Android and iOS smartphones and tablets from malicious and Trojanized applications. It blocks access to malicious websites, increase device performance, and protects your mobile data. You may download the Trend Micro Mobile Security apps from the following sites:
Did this description help? Tell us how we did.


