Mitigating Common Security Threats to Small and Medium Businesses
 The early half of 2017 saw malware such as WannaCry and Petya affecting a large number of organizations around the world. While the larger enterprises made the news, a lot of smaller businesses were affected by these attacks. All organizations, from the largest multinational corporation to smaller single proprietorship businesses, are vulnerable to security risks. However, Small and Medium Businesses (SMBs) are particularly exposed to malicious attacks.
The early half of 2017 saw malware such as WannaCry and Petya affecting a large number of organizations around the world. While the larger enterprises made the news, a lot of smaller businesses were affected by these attacks. All organizations, from the largest multinational corporation to smaller single proprietorship businesses, are vulnerable to security risks. However, Small and Medium Businesses (SMBs) are particularly exposed to malicious attacks.
SMBs face a different set of security challenges compared to larger companies with more resources. This piece takes a closer look at the security threats that SMBs have to deal with, as well as the challenges they might face when implementing proper security measures.
The Main Security Challenges for SMBs:
The reality is that for many SMBs, their limited budget leaves them less room to address security threats as they happen. While larger organizations often have dedicated IT professionals for handling network security, SMBs are less likely to dedicate resources to full-time security handling and monitoring.
Most smaller organizations will have one-size-fits-all IT teams that handle everything from software installation to virus removal. However, these employees are rarely trained to handle cybersecurity issues, and will often resort to using free security solutions that will usually only deliver the bare minimum in terms of detection and prevention.
Essentially, the main problems for SMBs when it comes to cybersecurity can be summed up in two words: money and personnel.
Given the limitations, there are still a number of ways SMBs can maximize their security capabilities. Before we delve into these strategies, let us take a look at some of the most significant threats that SMBs face on a daily basis.
Ransomware
In a way, SMBs make the perfect target for ransomware—they're likely to have enough resources to pay the ransom, but not enough to have proper security teams and might not have a solid backup process in place. Ransomware often arrives via malicious attachments, typically spam mail or downloaded via malicious links.
Larger organizations also often have segmented networks that can prevent ransomware from affecting the entire network system, as well as a large number of backups that they can use in case of infection. On the other hand, ransomware will often have a larger effect on a smaller business' network due to minimal backup policies and a general lack of effective security solutions. Ransomware can be devastating for smaller businesses, as a single infection on a server could wipe critical data or shut down the organization's operations. The challenge usually doesn't lie in the ransom demand itself—in fact, the ransom demand is the least of a small businesses worries. It’s the time and effort required getting systems and servers back online. Some ransomware variants are considered annoyances for organizations with stronger security measures; while they can still cause some damage, they won’t necessarily cripple operations. This isn’t true for many SMBs.
A key to mitigating ransomware attacks is to regularly back up important data. Backups do not have to be expensive or complicated either, as it can be done by simply setting up a regular backup schedule on separate systems. SMBs can also consider regularly backup up their data to offline storages that are not connected to the rest of the company’s network infrastructure.
SMBs should always keep their systems updated with the latest security updates and patches. Many malware exploit vulnerabilities to infect their target, similar to the way WannaCry infected unpatched systems. Larger organizations often have to deal with patch lag due to the challenge of having to update a large number of systems that might also have proprietary software installed. SMBs will usually not have this problem, and thus should apply patches as soon as they're available. In addition, updating software from older, unsupported versions should be a priority, despite the additional costs.
Cybercriminals also often use phishing attacks to target their victims, which makes security awareness equally important. This costs nothing and can be as easy as reading guides on spotting and avoiding phishing attacks. A large number of infections can be prevented by simply educating employees on the strategies cybercriminals use to spread malware.
Distributed Denial of Service Attacks
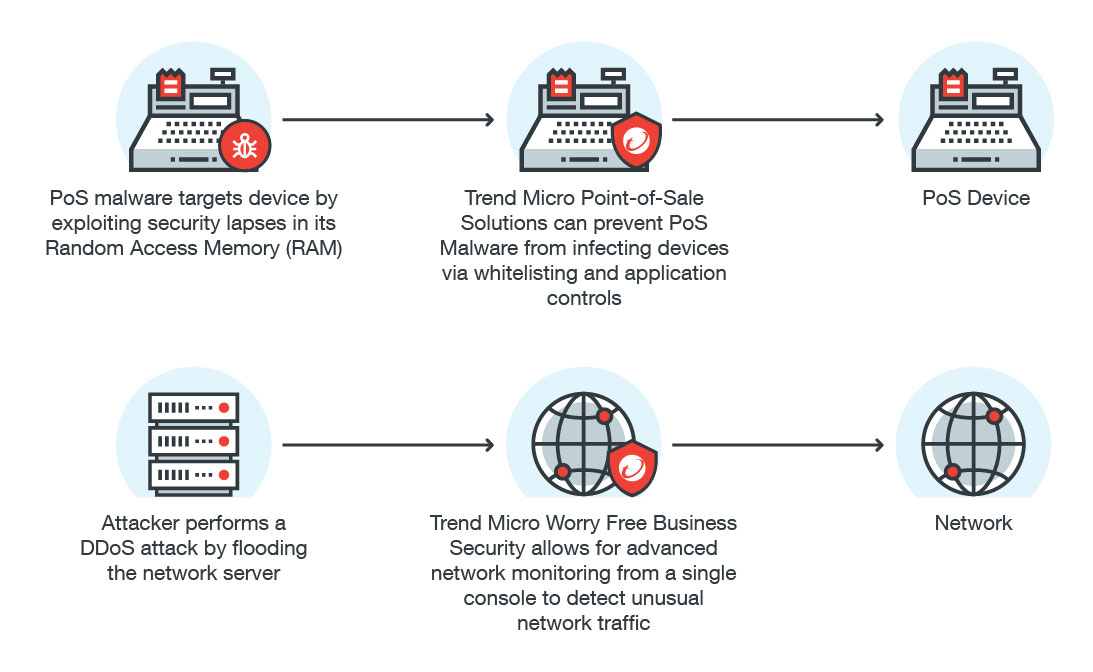
A Distributed Denial of Service (DDoS) attack involves preventing users from accessing certain services – often network based ones—by flooding it with meaningless traffic. Many DDoS attacks are similar to ransomware in that they are usually done as part of an extortion campaign, and like ransomware, these attacks can cripple a company. Again, resources play a significant role here. An SMB hit with a DDoS attack will find it more difficult to recover compared to larger organizations who have access to better protection. SMBs don’t even have to be targeted themselves to be affected by a DDoS attack. For financial reasons, many SMBs turn to IT hosting rather than hosting their own, placing them at risk of becoming collateral damage for any attack that targets their providers. Many small organizations often place a large portion of their operations online, due to the lower costs and simplified logistics. Now imagine a DDoS attack that takes down an online store’s website for days. That means zero transactions, thus zero sales for the company.
For a small organization, there is little that can be done once a DDoS attack is underway, hence the best mitigation strategies involve monitoring and preventing potential attacks before they happen. One of the ways SMBs can prevent or at least minimize DDoS attacks is by overprovisioning bandwidth. While this might be more costly, it can help prevent DDoS attacks from completely overwhelming the organization’s IT services. Another option is to use cloud-based services, which are more scalable when considering DDoS attacks. In addition to not having to maintain network infrastructure for their services on the cloud, SMBs can also take advantage of their service provider’s resources for dealing with DDoS attacks.
Another method that can help organizations keep websites up and running during a DDoS attack is to have a backup website that mirrors all the data contained in the original website. This can serve as a temporary website to keep customers aware of the situation while attacks are happening. While this translates to added costs, but it could be a viable option when considering the risks. Furthermore, there are security solutions that specifically detect and prevent DDoS attacks by monitoring network traffic for any unusual activities, giving organizations enough time to respond.
Point of Sale Attacks
SMBs can fall victim to Point of Sale (PoS) attacks as they can often be easier targets compared to larger organizations with sophisticated tools and preventive security measures. PoS attacks often fall into three main categories: malware, skimmers, and compromised machines. SMBs are vulnerable to all three types. While PoS attacks are different from the earlier examples in that they don’t usually totally cripple a business’s operations, they still cause a significant amount of damage—usually financial—to the affected organization.
Take, for example, PoS malware, which can steal information from SMBs. While this does not directly affect an organization’s operations, it can result in the stolen information being peddled in the underground or used for other malicious purposes. A cybercriminal can also use this information to perform unauthorized transactions. This will lead to chargebacks and disputes with credit card providers, and can result in financial penalties in addition to the losses from the actual PoS attack itself.
Smaller organizations should avoid purchasing PoS products from unreliable sources. As tempting as it might be to save money because they're cheaper, they could cause more problems in the long run if they turn out to be compromised machines or come loaded with malware. It would also be a good idea to migrate to EMV technology if possible, as this can greatly cut down on instances of skimming. Another option is to outsource PoS handling to larger dedicated organizations that can handle processes and security better.
For PoS malware, organizations can look into implementing access controls as well as isolate PoS terminals from the rest of the network. This could help prevent the stolen data from being sent to the attackers C&C servers due to the lack of internet access.
Protecting SMBs from cyber threats can be a challenge, but it can be accomplished with the proper use of easily available security resources, as well using security solutions that are tailored to smaller organizations with a limited budget.
Security solutions do not have to be expensive. SMBs can take advantage of multilayered solutions such as Trend Micro Worry-Free™ Business Security, which provides a comprehensive list of IT security features such as ransomware protection, spam prevention, and centralized management for easier monitoring of endpoints. This solution is designed to make SMB security a hassle-free experience by providing endpoint, web security, and email protection in a single bundle -- allowing SMBs to protect their employees anytime, anywhere. Furthermore, adding application control and whitelisting to Point-of-Sale (PoS) security lets SMBs lock down devices and have control over what applications run on their networks, helping prevent PoS malware from infecting the organization.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One