Fake Messaging App Installers Promoted on Fraudulent Download Sites, Target Russian Users
 Analysis and Insights by Raphael Centeno
Analysis and Insights by Raphael Centeno
Fake installers of popular messaging apps are being propagated via fraudulent download sites, as disclosed in a series of tweets by a security researcher from CronUp. We also encountered samples of the said files. The sites and the apps are in the Russian language and are aiming to bait Russian users.
Adware, or advertising-supported software, is any piece of software or application that displays advertisements, which appear as pop-up or pop-under windows. Most users unwittingly install adware by downloading freeware like toolbars, HD wallpapers, or widgets on PCs, or through some mobile apps. Although not outright malicious and considered as grayware, unwanted ads can be disruptive to some users. Adware can also possibly cause slower device and network performance.
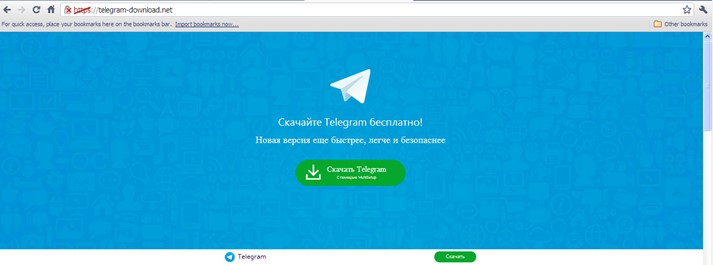
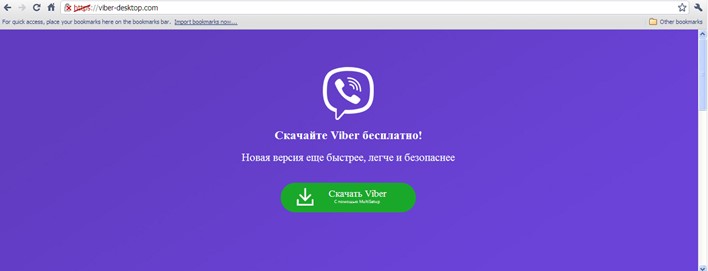
Figure 2. Fake download site for Viber app

Figure 3. Fake download site for WhatsApp

Figure 4. Fake download site for Zoom app
Fake apps are not the only ones used in suspicious activities; in fact, even legitimate installers (those found in fraudulent websites and not from official download sites) are not spared. Many cybercriminals bundle malicious files with legitimate installers of apps for communication and other uses. Once these files are downloaded, threat actors can possibly spread malware or gain unauthorized access to the users’ devices and systems.
Steering clear of fake apps
The coronavirus pandemic has forced many organizations to transition to a work-from-home setup. These arrangements heavily depend on communication apps to facilitate real-time interaction between remote team members, which is why securing the tools used in this setup is important.
[Related: Working From Home? Here’s What You Need for a Secure Setup]
Users should only download apps from their official download sites. If downloading from app stores such as the App Store or Google Play, users should examine whether the apps are legitimate or replicas. Tell-tale signs of counterfeit apps include a low number of downloads, low ratings, and bad feedback. Whether downloading from download sites or app stores, users should scrutinize the apps as fake apps and fraudulent download sites imitate the name and the design of their genuine counterparts.
Incorporating a multilayered approach to security can also safeguard users against such threats.
Indicators of Compromise
URL
- www[.]my-skype-now[.]com
- www[.]nod32-downloads[.]com
- www[.]skype-msetup[.]ru
- www[.]telegram-download[.]net
- www[.]viber-desktop[.]com
- www[.]whatsapp-msetup[.]ru
- www[.]zoom-download[.]com
| File Name | SHA-256 | Trend Micro Pattern Detection |
| nod32_msetup_[30894859].exe | c3bd85744c78695db241d14ccce676558eafccdecc33d79ab3c5904457c0ea11 | PUA.Win32.MulSetup.THA |
| telegram_msetup_[30894476].exe | c3bd85744c78695db241d14ccce676558eafccdecc33d79ab3c5904457c0ea11 | PUA.Win32.MulSetup.THA |
| viber_msetup_[30894239].exe |
c3bd85744c78695db241d14ccce676558eafccdecc33d79ab3c5904457c0ea11 | PUA.Win32.MulSetup.THA |
| zoom_msetup_[30893603].exe | c3bd85744c78695db241d14ccce676558eafccdecc33d79ab3c5904457c0ea11 | PUA.Win32.MulSetup.THA |
| zoom_msetup_[30894479].exe | c3bd85744c78695db241d14ccce676558eafccdecc33d79ab3c5904457c0ea11 | PUA.Win32.MulSetup.THA |
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One