by David Sancho (Trend Micro Research)
The modern cybercrime landscape has changed much from around a decade ago, when most criminals either built their own toolsets or hired other developers to create them. The skills and knowledge needed meant that gifted programmers often started these worldwide online attacks. Eventually, the people behind these attacks created peer-based communities where they shared and distributed attacktools and knowledge on how to operate them. These evolved into marketplaces where other criminals could purchase very advanced tools they could use to launch attacks that are more dangerous.
These marketplaces still exist today in the form of dedicated websites or online forums. While the developers of these tools know perfectly well how their products are being used, they commonly try to dodge responsibility by placing the onus on the buyer, who is supposed to be solely responsible for the way the software is used. In this case, though, these developers only sell their wares on criminal forums, where there is little doubt regarding their usage.
This article details how these underground vendors peddle their products, as well as the sales tactics they use, with a focus on their similarities with the way legitimate software is sold and marketed.
A Cybercriminal’s Toolkit: Products and Services
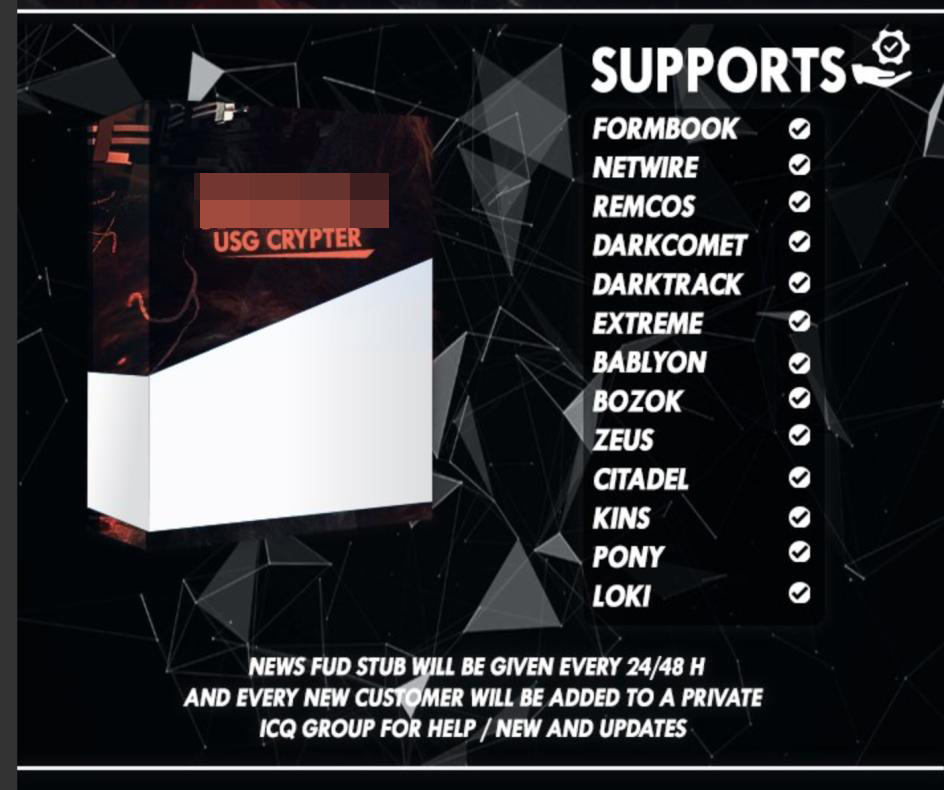
Underground marketplaces offer a variety of products to cybercriminals. While not all of these software suites are marketed for malicious purposes, most of them have potential criminal uses while others are undeniably malicious in nature.
These tools can be categorized into the following:
- Remote Administration Tools. Also known as RATs, these programs allow the user to run commands on a remote machine. When used in a legitimate manner, a network administrator can use it to clean, fix or change settings on a remote machine from a central location, thereby lowering the cost of managing a medium-sized network. When used maliciously, cybercriminals can use a RAT to infect machines, allowing them to spy on the user, steal data, and run other arbitrary programs, or other actions, such as enabling the victim’s webcam to record compromising videos.
- Binary obfuscation and encryption software. These tools alter other programs in order to protect them against analysis and detection. While there is a case to be made for protecting software against hacking, modification, and reverse engineering to protect intellectual property, these products can also be used to protect malicious programs and extend their life before antivirus programs and other defensive software detect them. In fact, most of these software advertisements state compatibility with well-known RATs and trojans. Often, these developers offer zero-detection features, or a guarantee that the encryption is changed when antivirus companies detect the protected files.
- Keyloggers. These programs detect and intercept keystrokes from the user to spy on their behavior and general data input. Keyloggers usually focus on stealing credentials, such as usernames and passwords of websites, online payment sites, online banking or any other online service. There isn’t a valid case for keyloggers to be used legitimately as logging keystrokes violates user privacy.
Business and Marketing Strategies in the Underground
Contrary to the popular notion of the underground being a chaotic place where potential buyers have to go through hoops to purchase their tools, many underground software vendors present their products in a very professional manner. In fact, modern underground software sales pitches often resemble how legitimate software is marketed — from variable pricing and bulk discounts to aftersales support.
These are the most prominent features we have observed:
- As-a-Service licensing model. Underground software is rarely sold as a one-time payment package. Instead, underground developers license their software for a limited period of time. The authors control this by allowing the program to connect to a licensing server that verifies whether the license is currently active or if it has already expired. This is a very common feature that legitimate software uses to detect and disable pirated licenses, and it seems that underground sellers are taking notes. It’s worth highlighting here that NetSeal, a licensing system made for hackers by hackers, was taken down and its creator sentenced by a US court in 2017. The recently arrested author of a crypter program, Cryptex Reborn, used NetSeal as protection.
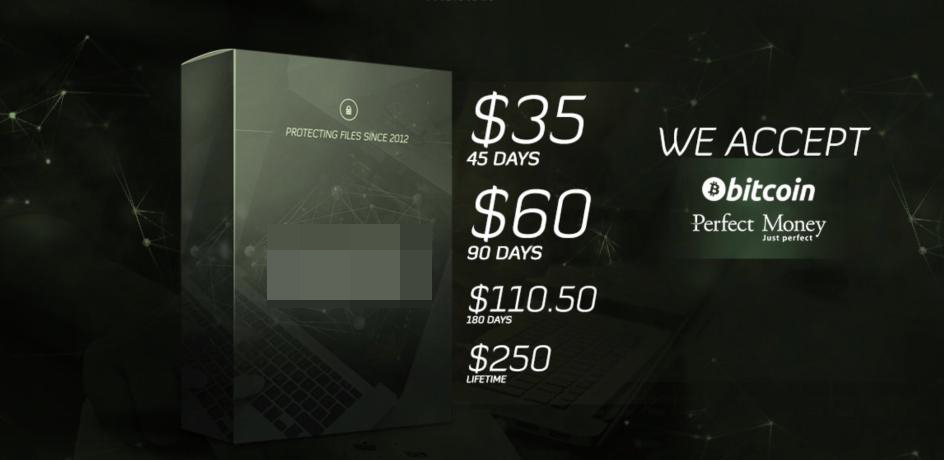
- Different license categories. Some underground software vendors offer different categories with increasing price points and features. The distinction between each category can be conveyed by using different metals that increase in value (bronze/silver/gold/platinum) or simply by adding words such as ‘basic’ or ‘premium’ to the offerings. The prices scale accordingly with the highest categories typically offering a more personalized service for a higher price.
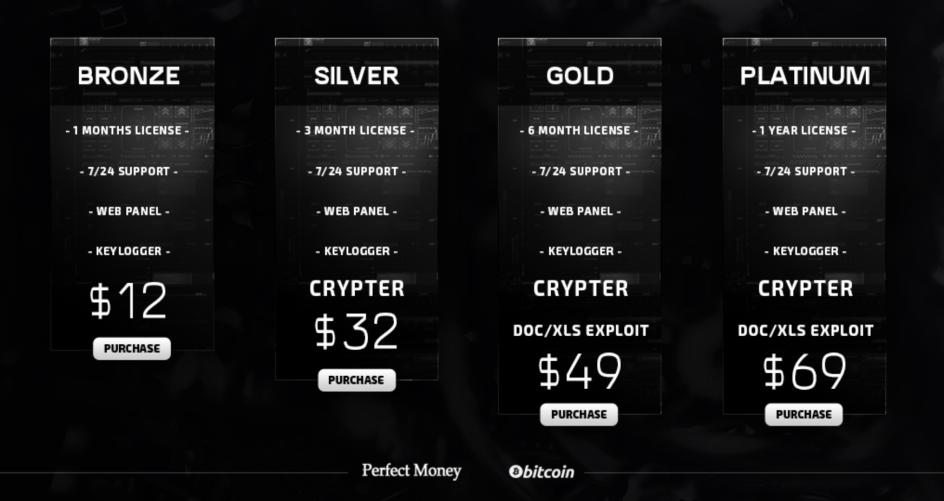
- Professional-looking images and displays. The imagery used to sell the software regularly includes boxes that look similar to physical software packaging, even though every single one of them is delivered digitally. In a similar manner to legitimate software makers, underground sellers have well-designed logos and carefully-chosen brand colors. It’s important to point out that underground software operations are usually one-man shops, but these developers feel the need to spend money on graphic designers (if they aren’t designers themselves) to convey a sense of quality and professionalism. In this respect, the bar is set so high that, by comparison, newcomers with a more pedestrian sales pitch will look unprofessional and less successful.
- Comparison tables. Some of these programs present ‘comparison tables’ showing their main features versus those of their competitors. This is a classic technique used by software vendors to showcase their product's main features benefits against their competition. In underground marketplaces, though, they don’t normally mention their competitors by name. These are very small — almost familiar — environments, so they tend to avoid directly targeting their competition.
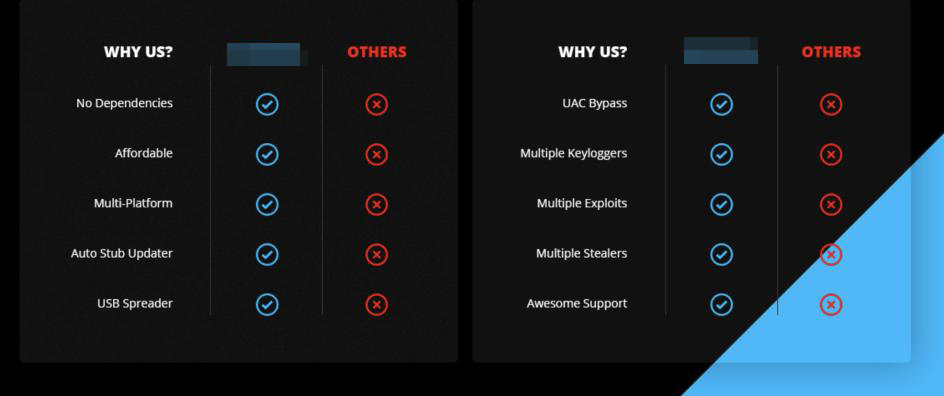
- Different levels of support. In the cases we’ve observed, underground developers offer some level of support. This is usually a personal chat support that promises a certain level of interaction — whether 24/7, a specific time zone or a “response in less than X hours.” Given how important it is for these developers to have good reputation within their community, they strive to keep their customers happy by personally interacting with them and helping solve their problems as quickly as possible. This is something that even some legitimate software vendors cannot provide as consistently, although some software makers do offer chat support as a way to lower their support costs.
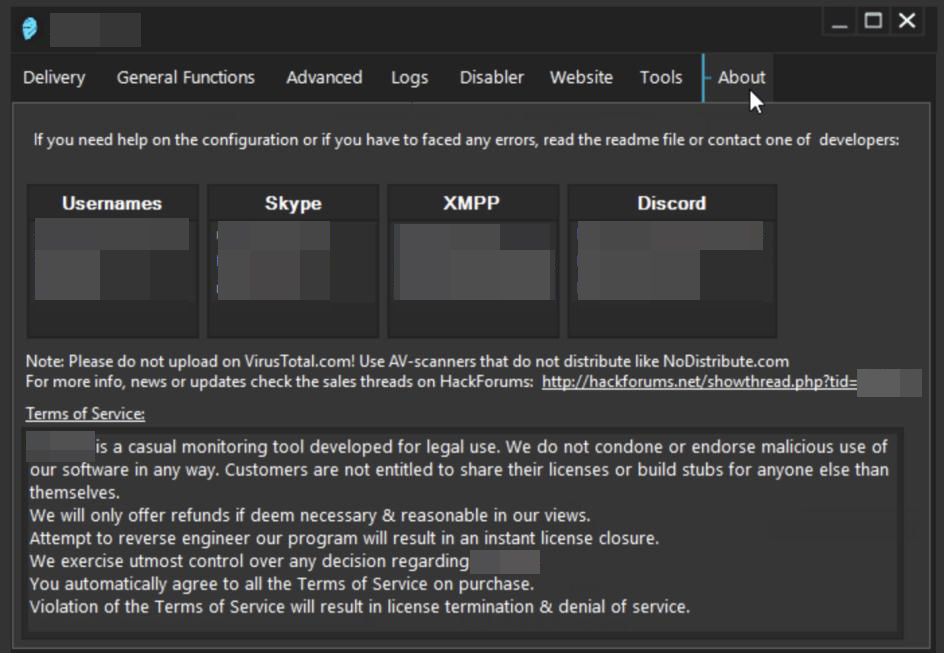
- Establishing reputation via third parties. Software developers strengthen their brand by means of trusted third-parties. Legitimate vendors do this by quoting testing companies, industry magazines, and other relevant organizations. On the other hand, underground vendors regularly utilize a vouching system quoting well-known forum users. Phrases like “recommended by users X and Y” are common. Often, some of the first posts in these products’ selling threads tend to be from known users vouching for the legitimacy and quality of the software, according to their experience.
- Anonymous payment methods. Underground developers often accept payments via anonymous and untraceable methods, like bitcoin and PerfectMoney, with the logos of these cryptocurrencies or services displayed in their marketing materials. Vendors also use other cryptocurrencies such as Monero, Ethereum or Bitcoin Cash. Some of them might accept more mainstream payment methods, but this is a risky proposition, so it’s not as common.
- Providing a free trial. Some of these vendors give a trial license of their software so that potential clients get a taste of the product. This is not something that all of them provide, though.
- Using campaigns and promotions. Some underground developers offer ‘promos’ or time-limited campaigns to promote the product. This is also very common with legitimate software vendors (and in any business in general).

Conclusion
The examples above demonstrate that developers of software often sold on the criminal underground are not disorganized individuals that resort to “shady back-alley deals.” In fact, many of them present their wares in a manner that is similar to the way mainstream software makers reach out to their audience.
It is also important to make a distinction between regular cybercriminals and these developers. Cybercriminal operations are 100% illegal and usually entail much more than just software development. Criminals have more complex operations (including money laundering and trojan distribution) and typically, higher revenue. In contrast, these developers are usually one-man shops that make their money by selling the software they write themselves. In order to stay in business, they need to market themselves well to other cybercriminal parties.
While these developers aren’t the ones directly performing the attacks, in many respects, what they do is just as reprehensible, to the point where they can be considered just as criminally culpable. On top of this, they are well aware of what they do and their strong links with the criminal underground make this crystal clear. As long as there is money to be made from the sale of these tools, we can expect these developers to stay around.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One