Russian Spam Delivers SHADE Ransomware via Link Embedded in PDF
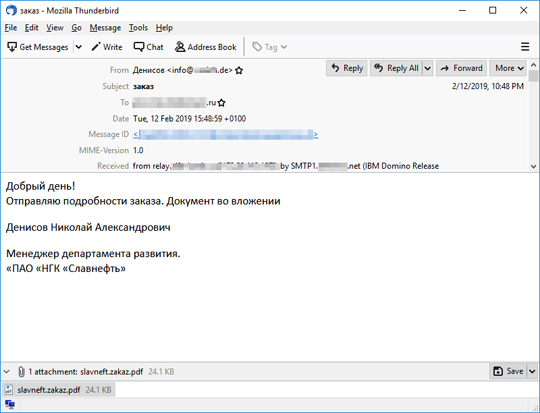
We have observed a recent spike in spam in Russian language. The spammed message delivers a SHADE ransomware variant via embedded link in the attached .PDF. Upon investigation, this campaign used compromised websites in the .PDF. When accessed, it downloads the archive file. The attached .PDF looks like the following:

The URLs which the malware connects to may have any of the following:
- hxxp://{domain}/wp-content/languages/plugins/slavneft.zakaz[.]zip
- hxxp://{domain}/wp-admin/css/colors/blue/slavneft.zakaz[.]zip
- hxxp://{domain}/wp-content/cache/blogs/slavneft.zakaz[.]zip
- hxxp:/{domain}/cli/PhilipMorris[.]zip
- hxxp://{domain}/includes/PhilipMorris[.]zip
Upon clicking the image in the .PDF, it downloads an archive file containing a JavaScript downloader, detected as Trojan.JS.SHADE.THBBBAI, of the SHADE ransomware:
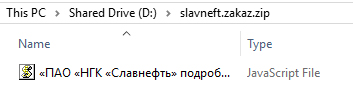
The downloaded ransomware is detected as TROJ_FRS.VSN0FB19. Users are advised to carefully check unsolicited emails and always exercise caution before opening any attachments or clicking on URLs to avoid being infected with malware. Trend Micro users are already protected from these spam emails. Recipients of this spam are advised to ignore them.
- ENGINE:8.0
- PATTERN:4446
