Fake Legal Notification Spam Comes With Malware
Data de publicação: 03 outubro 2014
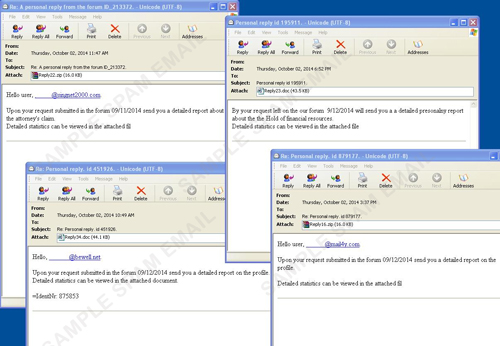
Have you ever received an e-mail that says they’re getting back to you regarding something that you have talked about before? To make it even more convincing, the follow-up e-mail asks you to open an attached file for you to review regarding that 'subject'. Beware of these mails - this is a classic social engineering tactic designed to get you infected with malware.
We recently discovered a spam attack that purports itself as a legitimate follow up mail. Some variants of the said spam looks legitimate, as it informs the recipient about a certain request submitted in a forum regarding an attorney’s claim or a financial report. Since the spammer already established itself as a reply to a hoax request from the recipient, it then continues by asking the potential victim to view the attachment that the victim allegedly requested. This attachment varies from one spam sample to another as it can be a plain Microsoft Word document or an encrypted one. Regardless of what type of file was attached, this document is verified to be malicious and is currently detected by Trend Micro as TROJ_ZLOD.FB.
Opening the document will not show any pop ups or symptoms that it is indeed malicious so users will initially see the file as harmless. The Word document only shows instructions on how one can retrieve the message it carries by enabling the macro feature - which, if followed, then allows the file to execute its malicious routines.
In this particular case, the document contains a macro that downloads malware onto the system from a verified malicious URL. The downloaded file ‘ubanner.png’ is verified to be malicious and detected as BKDR_ANDROM.WSUL.
This technique is not something new. Spammers have been absuing this particular feature because not everyone are aware that this can be used to carry malicious program and that this can sometimes pass off as normal file when scanned by security software. Again, we advise users to always verify first before opening file attachments.
Data/Hora do bloqueio de spam: 03 outubro 2014 GMT-8
TMASE
- Versão do mecan
- Patrón TMASE: 0994