OSX_FLASHBCK.A
OSX/Flshplyr-A (Sophos); OSX.Flashback (Symantec); Trojan-Downloader:OSX/Flashback.C (F-Secure)
Mac OS X 10.5 and later


Threat Type: Trojan
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This Trojan poses as a Flash Player installer. It requires an administrator password before it continues the installation.
It connects to a link to download additional installation and configuration files. However, as of this writing, site is inaccessible.
It restarts any instances of Safari.
It disables the Xprotect, an antimalware system built in to recent releases of Mac OS X. It unloads the XProtectUpdater daemon then modifies files by deleting their contents.
This Trojan may be unknowingly downloaded by a user while visiting malicious websites.
TECHNICAL DETAILS
Arrival Details
This Trojan may be unknowingly downloaded by a user while visiting malicious websites.
It may be downloaded from the following remote sites:
- http://{BLOCKED}pdatemanager.org/FlashPlayer-11-4-macos.zip
- http://{BLOCKED}pdatemanager.org/flashplugin/4ff
NOTES:
This malware poses as a Flash Player installer:
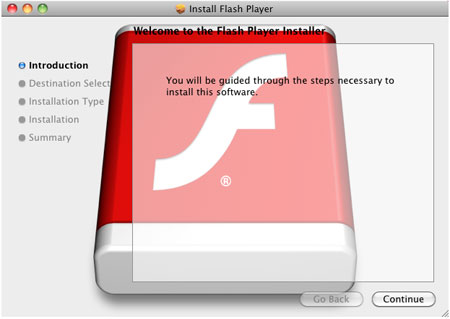
It requires an administrator password before it continues the installation.
This malware checks if the following file is present on the system:
- /Library/Little Snitch/lsd
Little Snitch is a firewall software for outgoing internet connections for Mac OS X.
If the said file is present, the malware stops the installation and deletes itself. If not, it proceeds with its installation.
It connects to the following links to download additional installation and configuration files:
- http://{BLOCKED}.43.31//counter/{hex}
- http://{BLOCKED}.com/counter/{hex}
However, as of this writing, the said sites are inaccessible.
It restarts any instances of Safari.
This malware disables the Xprotect, an anti-malware system built in to recent releases of Mac OS X. It unloads the XProtectUpdater daemon then modifies the following files by deleting their contents:
- /System/Library/LaunchDaemons/com.apple.xprotectupdater.plist
- /usr/libexec/XProtectUpdater
SOLUTION
NOTES:
- To restore the modified XProtectUpdater files, please re-install the XProtectUpdater.
- Restart your machine
- Scan your computer with your Trend Micro product to delete files detected as OSX_FLASHBCK.A. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.

