Virus.MacOS.THIEFQUEST.A-O
Ransom:MacOS/Filecoder.YA!MTB (MICROSOFT); HEUR:Trojan-Ransom.OSX.FileCoder.gen (KASPERSKY)
MacOS


Threat Type: Virus
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This Virus prepends its codes to target files. It adds infection markers to files.
It executes commands from a remote malicious user, effectively compromising the affected system.
It encrypts files with specific file extensions. It encrypts files found in specific folders.
TECHNICAL DETAILS
Arrival Details
This malware arrives via the following means:
- It arrives on a system as part of an application bundle downloaded by users who look for pirated software installers.
Installation
This Virus drops the following files:
- /private/var/root/.ncspot – text files containing a 43-byte string to be used by the Virus
It drops the following copies of itself into the affected system:
- ~/Library/AppQuest/com.apple.questd
- /Library/AppQuest/com.apple.questd
- /private/var/root/Library/.{random generated string}
- (Note: The character <~>indicates the main directory accessible to the current logged in user only. If the file path does not contain the character <~> specified file is located in the local main directory accessible to all users.)
File Infection
This Virus infects the following file types:
- Mach-O Executable File
It prepends its codes to target files.
It searches for target files in the following folders:
- /Users
It adds infection markers to files.
Backdoor Routine
This Virus executes the following commands from a remote malicious user:
- Load and execute received data from memory
- Save received data as specified file
- Log keystrokes
It connects to the following URL(s) to send and receive commands from a remote malicious user:
- {BLOCKED}.{BLOCKED}.237.219
Download Routine
This Virus accesses the following websites to download files:
- http://andrewka6.{BLOCKED}anywhere.com/ret.txt → Contains specified C&C Server
Other Details
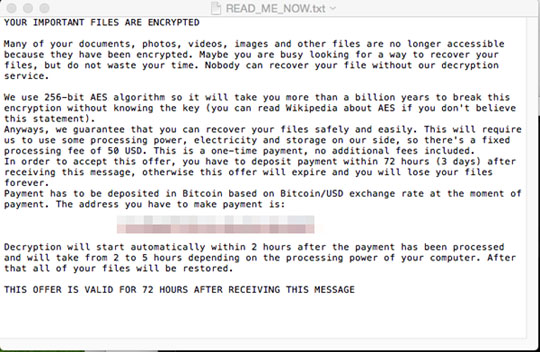
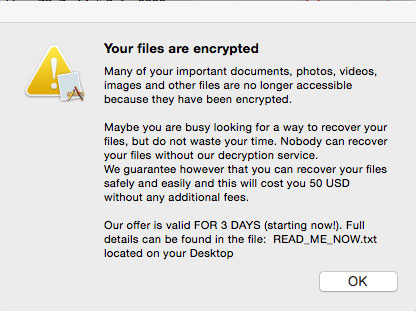
This Virus displays a pop-up window with the following message:
It does the following:
- Installs the following autorun items:
- ~/Library/LaunchAgents/com.apple.questd.plist
- /Library/LaunchDaemons/com.apple.questd.plist
- (Note: The character <~>indicates the main directory accessible to the current logged in user only. If the file path does not contain the character <~> specified file is located in the local directory accessible to all users.)
- It avoids the Mach-O Executable files that are included in application bundles(.app file extension)
- Infected files from this Virus will drop and execute its original code as a hidden file to deceive the user into thinking that the infected executed file was not affected while the malware performs its routines in the background.
- It will first attempt to download the file to get the specified C&C. If unsuccessful it will instead use the IP Address as C&C Server.
- It does not append a different file extension to the file name of the encrypted files. Instead, it leaves an encryption marker at the end each file.
- It is capable of file exfiltration. It searches the following folder for files of interest to encode and send to the server:
- /Users
- It searches for files that match the following regular string expressions to encrypt:
- *id_rsa*/i
- *.pem/i
- *.ppk/i
- known_hosts/i
- *.ca-bundle/i
- *.crt/i
- *.p7!/i
- *.!er/i
- *.pfx/i
- *.p12/i
- *key*.pdf/i
- *wallet*.pdf/i
- *key*.png/i
- *wallet*.png/i
- *key*.jpg/i
- *wallet*.jpg/i
- *key*.jpeg/i
- *wallet*.jpeg/i
Ransomware Routine
This Virus encrypts files with the following extensions:
- .tar
- .rar
- .tgz
- .zip
- .7z
- .dmg
- .gz
- .jpg
- .jpeg
- .png
- .gif
- .psd
- .eps
- .mp4
- .mp3
- .mov
- .avi
- .mkv
- .wav
- .aif
- .aiff
- .ogg
- .flac
- .doc
- .txt
- .docx
- .xls
- .xlsx
- .pages
- .rtf
- .m4a
- .csv
- .djvu
- .epub
- .pub
- .key
- .dwg
- .c
- .cpp
- .ovpn
- .download
- .pem
- .numbers
- .keynote
- .ppt
- .aspx
- .html
- .xml
- .json
- .js
- .sqlite
- .pptx
- .pkg
- .vb
- .asp
- .ppk
- .crt
- .p7
- .pfx
- .p12
- .dat
- .hpp
- .ovpn
- .download
- .pem
- .numbers
- .keynote
- .ppt
- .aspx
- .html
- .xml
- .json
- .js
- .pkg
- .webarchive
It encrypts files found in the following folders:
- /Users
It leaves text files that serve as ransom notes containing the following text:
SOLUTION
Scan your computer with your Trend Micro product to delete files detected as Virus.MacOS.THIEFQUEST.A-O. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check the following Trend Micro Support pages for more information:
Did this description help? Tell us how we did.