URSNIF
November 04, 2020
PLATFORM:
Windows
OVERALL RISK RATING:
REPORTED INFECTION:


Threat Type: Trojan Spy
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
The Ursnif malware is one of the most prolific information stealing Trojans in the cybercrime landscape since 2007. This malware is one of the most effective malware families that are being delivered through malicious spam campaigns. The malware's source code was leaked in 2015 and made publicly available in Github, enabling other cybercriminals to add new features and make further development of the code.
Newer variants of URSNIF have enhanced modules to:
- evade security protection and steal financial information, email user accounts, content of inboxes and digital wallets
- provide a new persistence mechanism, new stealing modules, and new cryptocurrency stealing modules
- provide language checks works as a way of localization and a method of avoiding sandboxes and virtual machines
- look for disk encryption software and attempt to extract keys in order to unencrypt files that the user may have tried to hide
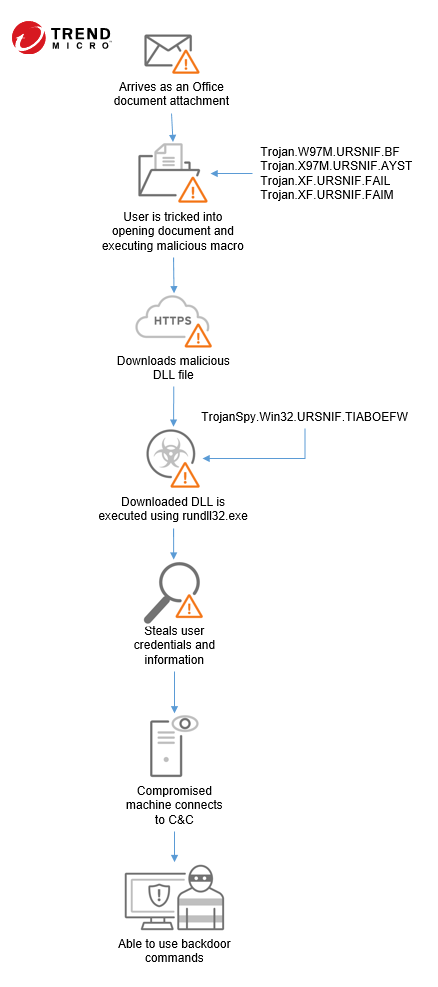
- target Microsoft Office users by starting with a weaponized Office document attached to a phishing email. In one example, a malicious document asks the user to enable macros to check if the target machine has Japanese country settings
- take advantage of an Italy-based retirement system entity by circulating a spam with the manager's signature and encouraging the recipient to open the attached Excel file. Once opened, it requests password indicated in the email content and contacts the URL contained within. From that URL, a DLL is downloaded to the victim's machine, which at that point the malware spreads to infect the system.
It is capable of the following:
- Information Theft
Its impact consists of:
- Financial Loss - steals banking, digital wallets and cryptocurrency information
- Violation of user privacy - gathers user credentials on various applications, logs keystroke and steals user information
URSNIF typically follows the infection chain below: