PE_BISTRO.Ax
Windows 2000, Windows XP, Windows Server 2003


Threat Type: File infector
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
This destructive memory resident, polymorphic virus infects Win 32 (PE) executables in the Windows directory and its subdirectories.
It infects these files upon boot-up, after the virus has been executed. In some instances, the virus corrupts the files it infects.
TECHNICAL DETAILS
NOTES:
This virus is executed when its dropper program is run. The following text appear in the decompressed versions of the dropper programs:
- Caf Troc Virus, if you like you can create self an example of this nice program we hope that you have fun :( before you begin to work with this nice programm, we would like to introduce our self GhostDog, leader and Coder lives in England -- United Kingdom --, 30 Years old student of informatic and hate all Lamerz and Rippers Mesut, Polymorphic Coder lives in Tuerkey -- Izmir --, 28 Years old student of Nuclear Medicine and i am love all people who like kebap more interesting informations, you can get next two month...!
The first time that the dropper program is run, it creates a copy of itself in the Windows directory. The filename of this dropped file is chosen at random.
The virus then adds the following registry entry:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run {malware file name} = %Windows%\{malware file name}.exe
At every boot-up, the virus infects a few EXE files in the Windows and its subdirectories. The virus also infects other files by appending itself to the end of the file and changing some header values so that entry point now points to the virus code.
The virus adds about 70 Kilobytes to the target file. This virus is not encrypted but employs a polymorphic technique by scrambling the codes and linking jumps to the next block of code. The virus also modifies the instructions in such a way that the functionality remains the same but the code is changed.
Since EXPLORER.EXE is loaded upon boot-up, it cannot be infected by the virus so the virus does the following to infect it:
1. Upon the first-reboot after running the dropper file, the virus creates an infected copy of EXPLORER.EXE as the file EXPLORER.AB in the Windows directory.
2. Then it creates WININIT.INI with the following value:
- c:\WINDOWS\EXPLORER.EXE = c:\WINDOWS\EXPLORER.AB
3. On the next reboot, the virus infects EXPLORER.EXE since EXPLORER.AB is the one loaded upon boot-up as specified in the WININIT.INI. After infecting EXPLORER.EXE, the virus deletes WININIT.INI and EXPLORER.AB.
4. On the third reboot, the infected EXPLORER.EXE is loaded upon boot-up so it cannot be cleaned or deleted.
The virus uses call gate techniques to gain ring zero privilege, and utilizes the ETG (Executable Trash Generator) engine to modify its own code and to hide from heuristic scanners.
It uses Structures Exception Handler (SEH) to catch errors while modifying its own code to prevent detection.
SOLUTION
Step 1
For Windows XP and Windows Server 2003 users, before doing any scans, please make sure you disable System Restore to allow full scanning of your computer.
Step 2
Identify and delete files detected as PE_BISTRO.Ax using either the Startup Disk or Recovery Console
Step 3
Restore a file/s that has/have been corrupted/modified by this malware/grayware
To restore system files:
• For Windows 2000:
- Insert your Windows 2000 Installation CD in your CD-ROM drive.
- Click Start>Run.
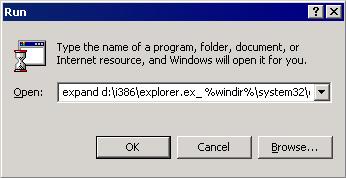
- In the Open text box, type the following then click OK:
expand D:\i386\{file to restore}.ex_ %windir%\system32\{file to restore}.exe
• For Windows XP and Windows Server 2003:
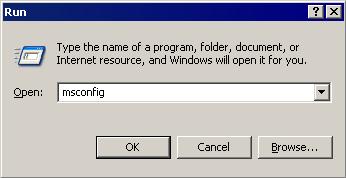
- Click Start>Run.
- In the Open text box, type the following then click OK:
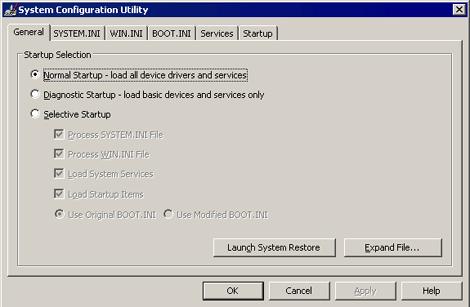
MSCONFIG - Make sure that the option Normal startup - load all device drivers and services option is selected.
- Click the Expand button.
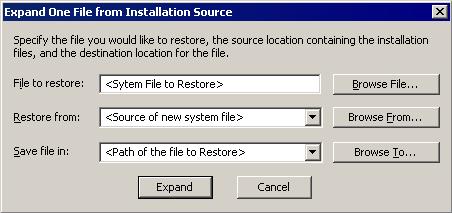
- In the dialog box that appears, type the following:
- File to restore contains the path and file name of the file you wish to restore.
- Restore from contains the path to the Windows CAB files. This path may vary from machine to machine. It may be in a local drive, in a network drive, or in a CD-ROM. In the local drive, it is usually in C:\WINDOWS\OPTIONS\INSTALL.
- Save file in contains the path of the file you wish to restore (Do not include the file name).
- Click the Expand button.
Did this description help? Tell us how we did.

