ANDROIDOS_FAKEINST.A
Information Stealer, Premium Service Abuser
Windows 2000, Windows XP, Windows Server 2003


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
This Trojan may be manually installed by a user.
TECHNICAL DETAILS
Arrival Details
This Trojan may be downloaded from the following remote sites:
- {BLOCKED}giesthegame.ru
- {BLOCKED}giessymbian.ru
- {BLOCKED}giessamsung.ru
- {BLOCKED}giesru-hd.ru
- {BLOCKED}giesnokia.ru
- {BLOCKED}giesjava.ru
- {BLOCKED}giesapk.ru
- {BLOCKED}gies-symbian.ru
- {BLOCKED}gies-samsung.ru
- {BLOCKED}gies-nokia.ru
- {BLOCKED}gies-java.ru
- {BLOCKED}gies-apk.ru
- {BLOCKED}giessymbian.ru
- {BLOCKED}giessamsung.ru
- {BLOCKED}giesnokia.ru
- {BLOCKED}giesjava.ru
- {BLOCKED}giesapk.ru
- {BLOCKED}gies-symbian.ru
- {BLOCKED}gies-samsung.ru
- {BLOCKED}gies-nokia.ru
- {BLOCKED}gies-java.ru
- {BLOCKED}gies-apk.ru
- {BLOCKED}giesmac.ru
- {BLOCKED}giesgame.ru
- {BLOCKED}giesandroid.ru
- {BLOCKED}gies2.ru
- {BLOCKED}gies-pc.ru
- {BLOCKED}gies-mac.ru
- {BLOCKED}gies-hd.ru
- {BLOCKED}giespc.ru
- {BLOCKED}giesmac.ru
- {BLOCKED}gieshd.ru
- {BLOCKED}giesandroid.ru
- {BLOCKED}gies-pc.ru
- {BLOCKED}gies-mac.ru
- {BLOCKED}gies-hd.ru
- {BLOCKED}gies-android.ru
- {BLOCKED}gies.ru
- {BLOCKED}gies-ru.ru
- {BLOCKED}gieshd.ru
- {BLOCKED}gies-android.ru
- {BLOCKED}gies-game.ru
- {BLOCKED}gies-rovio.ru
- {BLOCKED}s-bad.ru
- {BLOCKED}gies.ru
- {BLOCKED}gies.ru
- {BLOCKED}giessymbian.ru
It may be manually installed by a user.
NOTES:
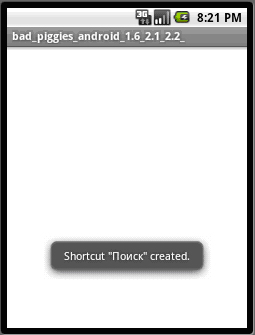
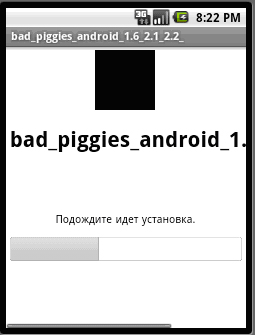
After installation, it shows a black icon named bad_pigges, which has the same name as popular application, Bad Piggies from Rovio Mobile Ltd..


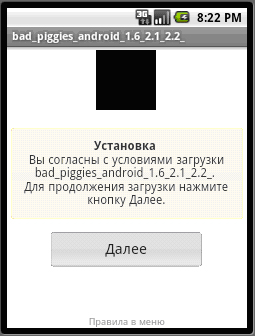
After users click the following button, it sends SMS:
The following are the SMS it sends:
| Number | Content |
|---|---|
| 2858 | 70123700212510818672 |
| 9151 | 78341700242510871602 |
| 7151 | 70136700202510891822 |
It leads users to the following screen:
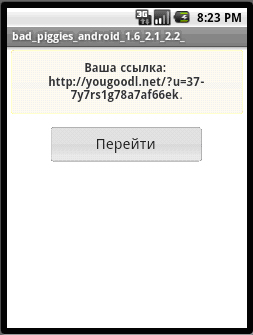
Once users clicked on the button, it leads them to the following URL:
- http://{BLOCKED}dl.net/?u=37-7y7rs1g78a7af66ek
The malware has the ability to drop incoming SMS and send out contacts to the following URL:
- http://{BLOCKED}1.net/index.php
SOLUTION
Step 1
Remove unwanted apps on your Android mobile device
Step 2
Scan your computer with your Trend Micro product to delete files detected as ANDROIDOS_FAKEINST.A. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


