HKTL_STEAL.GA
a variant of MSIL/Packed.NetSeal.A suspicious (ESET-NOD32), Trj/CI.A (Panda), Worm:Win32/Autorun.ZG (Microsoft)
Windows 2000, Windows Server 2003, Windows XP (32-bit, 64-bit), Windows Vista (32-bit, 64-bit), Windows 7 (32-bit, 64-bit)


Threat Type: Hacking Tool
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This hacking tool arrives as a component bundled with malware/grayware packages. It may be manually installed by a user.
TECHNICAL DETAILS
Arrival Details
This hacking tool arrives as a component bundled with malware/grayware packages.
It may be manually installed by a user.
Installation
This hacking tool drops the following files:
- %All Users Profile%\Application Data\Nimoru\GizmoSE
- %All Users Profile%\Application Data\Nimoru\GizmoDll
- %All Users Profile%\Application Data\Nimoru\6DE717A443510AB9BB378E6E051FEAB1
(Note: %All Users Profile% is the All Users folder, where it usually is C:\Documents and Settings\All Users on Windows 2000, Windows Server 2003, and Windows XP (32- and 64-bit); C:\ProgramData on Windows Vista (32- and 64-bit), Windows 7 (32- and 64-bit), Windows 8 (32- and 64-bit), Windows 8.1 (32- and 64-bit), Windows Server 2008, and Windows Server 2012.)
It creates the following folders:
- %All Users Profile%\Application Data\Nimoru
(Note: %All Users Profile% is the All Users folder, where it usually is C:\Documents and Settings\All Users on Windows 2000, Windows Server 2003, and Windows XP (32- and 64-bit); C:\ProgramData on Windows Vista (32- and 64-bit), Windows 7 (32- and 64-bit), Windows 8 (32- and 64-bit), Windows 8.1 (32- and 64-bit), Windows Server 2008, and Windows Server 2012.)
NOTES:
This hacking tool sends an email if the user registered an account:
To: {Email provided by user}
Subject: Please activate your account!
Body:
Please click on the following link to activate your account. If you did not register an account or believe this email has been sent to you by mistake please ignore it.
Username: {Username provided by user}
Activation: http://seal.{BLOCKED}u.com/User/activate.php?t=ae9973475a479b724e8f978a9f7fd5a
This hacking tool sends an email if the user request for a password reset:
To: {Email provided by user}
Subject: Password Reset
Body:
This email has been sent to you because you recently requested a password reset. If you did not make this request or believe this email has been sent to you by mistake please ignore it. Otherwise you may proceed by clicking the reset link below.
Username: {Username provided by user}
Activation: http://seal.{BLOCKED}u.com/User/reset.php?t=0978bf540d33fba1b0ca6f3a91f50fb1
This hacking tool connects to the following websites:
- http://seal.{BLOCKED}u.com
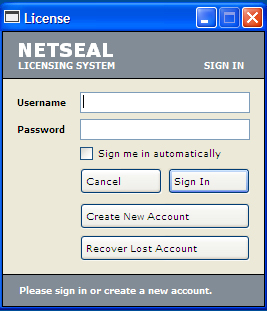
This hacktool displays the following image once executed:
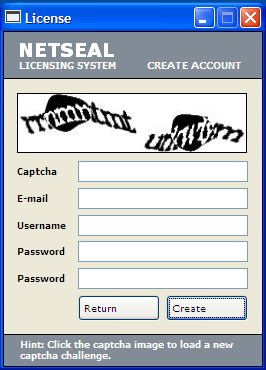
This hacktool displays the following image when the user wants to creates a new account:
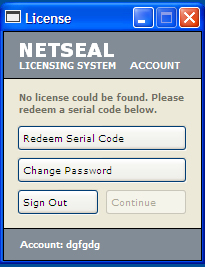
This hacktool displays the following image when the user signs in:
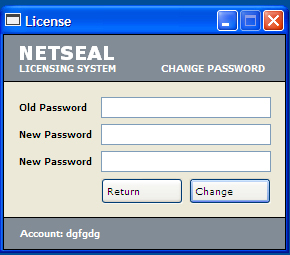
This hacktool displays the following image when the user wants to change the account password:
This hacktool displays the following image when the user wants to reset the account password:
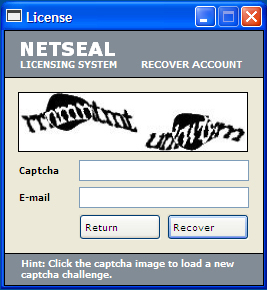
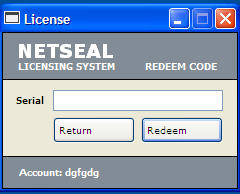
This hacktool displays the following images when the user wants to redeem the serial code:
SOLUTION
Step 1
Before doing any scans, Windows XP, Windows Vista, and Windows 7 users must disable System Restore to allow full scanning of their computers.
Step 2
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 3
Search and delete these folders
- %All Users Profile%\Application Data\Nimoru
Step 4
Search and delete this file
- %All Users Profile%\Application Data\Nimoru\GizmoSE
- %All Users Profile%\Application Data\Nimoru\GizmoDll
- %All Users Profile%\Application Data\Nimoru\6DE717A443510AB9BB378E6E051FEAB1
Step 5
Scan your computer with your Trend Micro product to delete files detected as HKTL_STEAL.GA. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


