ANDROIDOS_SMSSPY.DT
Information Stealer, Spying Tool
Android OS


Threat Type: Spyware
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This spyware may be downloaded from app stores/third party app stores.
TECHNICAL DETAILS
Arrival Details
This spyware may be downloaded from app stores/third party app stores.
NOTES:
It declares to use the following permissions:
| android.permission.READ_SMS | read SMS or MMS |
| android.permission.WRITE_EXTERNAL_STORAGE | modify/delete SD card contnts |
| android.permission.ACCESS_NETWORK_STATE | view network state |
| android.permission.INTERNET | full Internet access |
| android.permission.RECEIVE_BOOT_COMPLETED | automatically start at boot |
| android.permission.CHANGE_COMPONENT_ENABLED_STATE | enabled or disable an app component |
| android.permission.PROCESS_OUTGOING_CALLS | intercept outgoing calls |
When the malware is executed, it configures the FTP server and the phone number. The phone number is a key in reopening the setting panel. By setting the phone number, the cybercriminals can dial the phone number on the device and show the panel.
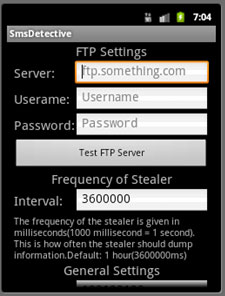
After clicking the “Start Logging” button, it hides its icon and asks the users to reboot.
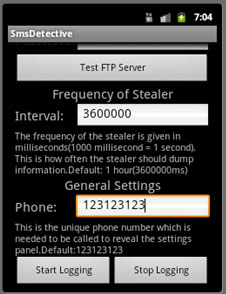
It logs SMS to /sdcard/.androidsecuritytest/Log.sda, and sends the file to a specific FTP server.
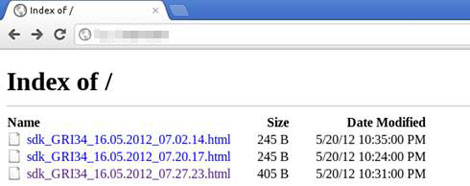
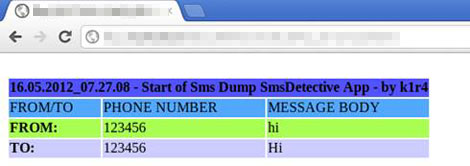
Once the cybercriminals access the setting panel, they can perform the following capabilities:
- Install spyware on the device
- Click the app icon to execute the app
- Set the FTP server and phone number
- Sends SMS (inbox and outbox) to the FTP server
SOLUTION
Step 1
Remove unwanted apps on your Android mobile device
Step 2
Scan your computer with your Trend Micro product to delete files detected as ANDROIDOS_SMSSPY.DT. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


