ANDROIDOS_FONCYSMS.A
Premium Service Abuser, Rooting Tool
Android OS


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
This is an AndroidOS malware with backdoor capabilities. It drops a file that creates an IRC connection where it receives commands, thus compromising the affected system's security for the user. It is also a premium service abuser, which can result in unauthorized billing charges for the user.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
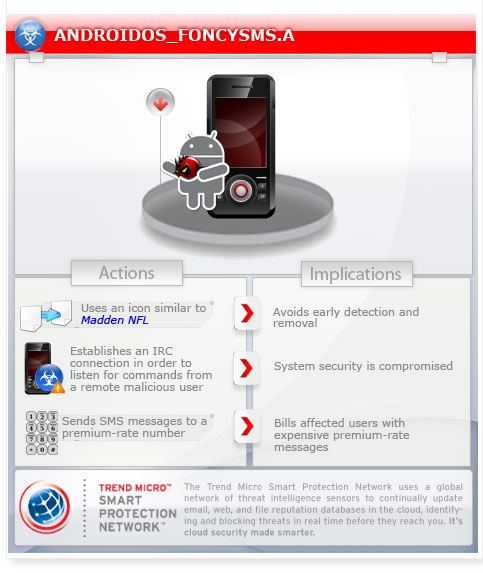
This Android application displays an icon similar to that of "Madden NFL" game. However, upon execution, it drops and installs other malicious components then displays an error.
This Trojan may be manually installed by a user.
TECHNICAL DETAILS
Arrival Details
This Trojan may be manually installed by a user.
NOTES:
When installed, this Android application displays an icon similar to that of "Madden NFL" game.
![]()
However, upon execution, it drops and installs other malicious components then displays an error with the message:
"(0x14) Error - Not registred application."
It creates the following folder and sets its permissions to read, write and execute for all:
- /data/data/com.android.bot/files
It then extracts its component files into the created folder:
- header01.png - root application
- footer01.png - IRC bot
- border01.png - premium service abuser
To begin, it executes header01.png. If rooting is successful, it will run footer01.png which is an IRC bot. It attempts to establish an IRC connection to the following server:
- {BLOCKED}.{BLOCKED}.196.198
Once connected, it joins the channel #andros where it waits for commands coming from a remote user.
The IRC bot executes border01.png.
border01.png is a premium service abuser that runs on Android OS. It obtains the location of the user by using getSimCountryISO API. The premium number and message it uses vary depending on the location.
fr (France)
number: 81083
message: ALL
be (Belgium)
number: 3075
message: CODE
ch (Switzerland)
number: 543
message: GEHEN SP 300
lu (Luxembourg)
number: 64747
message: ACCESS SP
ca (Canada)
number: 60999
message: SP
de (Germany)
number: 63000
message: SP 462
es (Spain)
number: 35024
message: GOLD
gb (Great Britain)
number: 60999
message: SP2
ma (Morocco)
number: 2052
message: CODE
sl (Sierra Leone)
number: 7604
message: PASS
ro (Romania)
number: 1339
message: PASS
no (Norway)
number: 2227
message: PASS
se (Sweden)
number: 72225
message: PASS
us (United States)
number: 23333
message: PASS
If the returned value is not one of the above-mentioned countries, it sends "WUUT" to 00000.
It also blocks incoming messages coming from the numbers above then connects to the URL below with parameters:
- http://{BLOCKED}.{BLOCKED}.146.102/?={premium rate number}///{message body}
SOLUTION
Step 1
Trend Micro Mobile Security Solution
Trend Micro Mobile Security Personal Edition protects Android smartphones and tablets from malicious and Trojanized applications. The App Scanner is free and detects malicious and Trojanized apps as they are downloaded, while SmartSurfing blocks malicious websites using your device's Android browser.
Download and install the Trend Micro Mobile Security App via Google Play.
Step 2
Remove unwanted apps on your Android mobile device
Did this description help? Tell us how we did.



