Social Engineering via Phishing Will Replace Exploit Kits as Attack Vector
Phishing attacks will markedly increase in 2019. The diversity in software and operating system (OS) market shares is wider than ever, with no single OS holding more than half of the market (compared to five years ago, for instance), so cybercriminals are adapting by going back to exploiting a more common “operating system”: human emotions. True enough, we have been seeing an increase in phishing attacks in recent years, which we can glean from the volume of phishing-related URLs blocked.
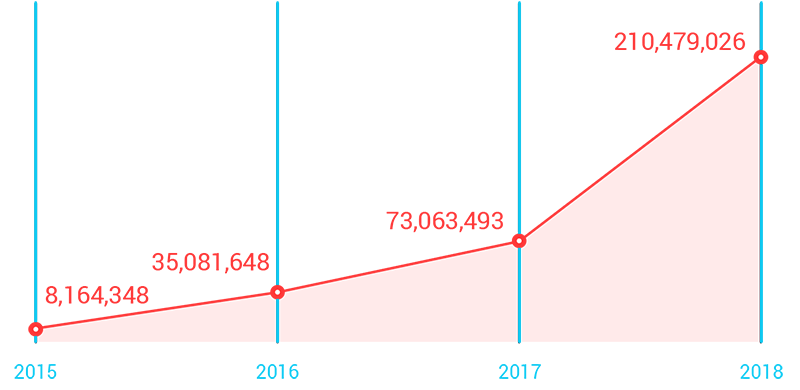 Phishing-related URLs blocked increased, based on data from the Trend MicroTM Smart Protection NetworkTM infrastructure as of Q3 2018.
Phishing-related URLs blocked increased, based on data from the Trend MicroTM Smart Protection NetworkTM infrastructure as of Q3 2018.
We will continue to see a decrease in exploit kit activity, something we have noted in our exploit kit activity data as well.
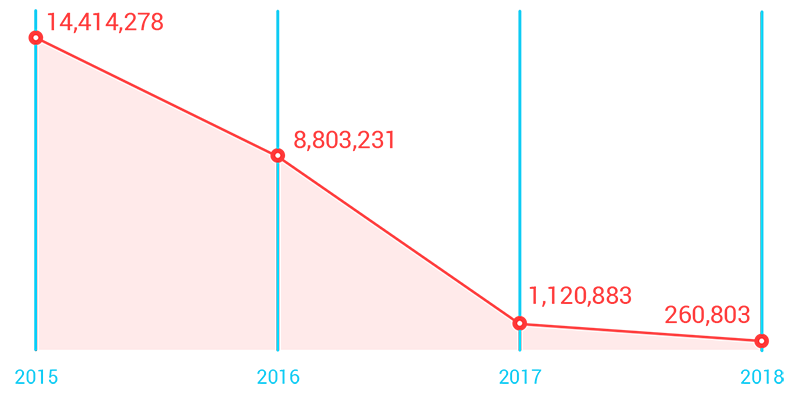 Exploit kit activity blocked decreased over the years, based on data from the Trend Micro Smart Protection Network infrastructure as of Q3 2018.
Exploit kit activity blocked decreased over the years, based on data from the Trend Micro Smart Protection Network infrastructure as of Q3 2018.
Actual Mass Real-World Use of Breached Credentials Will Be Seen
Breached credentials will be actively and heavily used in fraudulent transactions as cybercriminals take the next logical step after amassing data breach info dumps in past years: using these stolen credentials. A recent report by Ponemon Institute and Akamai highlighted that credential stuffing — the automated injection of stolen username and password combinations from a single breach into several other popular websites — is becoming more severe.
We will see cybercriminals signing up with stolen account credentials for mileage and rewards programs, and using them to register trolls for cyberpropaganda, manipulate consumer portals by posting fake reviews, or add fake votes to community-based polls — the applications are endless.
Sextortion Cases Will Rise
We will see more polished executions or iterations of digital extortion. For instance, we will see an increase in reports of teenagers and young adults being extorted for non-monetary reasons. Even if there is no guarantee that a blackmailer will come through, the highly personal nature of this kind of attacks will make the victim seriously consider fulfilling the attacker’s demands, whether that means money or sexual favors. In some cases, this situation will lead to dire outcomes such as suicide — this kind of attacks will claim more lives in 2019.
Home Networks in Work-From-Home Scenarios Will Open Enterprises to BYOD-like Security Risks
Employees’ internet-connected home devices will be the new and unlikely entry point into enterprise networks. This is the unexpected but inevitable intersection of two trends:
- The rise of remote-working arrangements, which challenges the visibility of enterprise data movements whenever employees access cloud-based apps and collaboration software for chat, videoconferencing, and file sharing from home.
- The increasing adoption of smart devices in the home, which employees will find incredibly convenient to use for work as well, resulting in a mixed-use scenario.
Our researchers have already proved how smart speakers can leak personal data. A few targeted attack scenarios in 2019 will make use of smart speaker weaknesses to access enterprise networks through employees’ home networks.
Automation Will Be a New Wrinkle in Business Process Compromise
Business process compromise (BPC) — in which specific business processes are silently altered to generate profit for attackers — will be an ongoing risk for enterprises. Automation will add a new layer of challenge in securing business processes against BPC. Forrester predicts that automation will result in the loss of 10 percent of jobs in 2019.
As more aspects of monitoring and function are conducted through software or online applications, threat actors will have more opportunity to infiltrate these processes if they are not secured from the outset. Automation software will have vulnerabilities and integration with existing systems will introduce loopholes.
Furthermore, since threat actors will try to find weaknesses in a target company’s suppliers, partners, or vendors to accomplish their goals, automation will introduce risks to the supply chain as well.
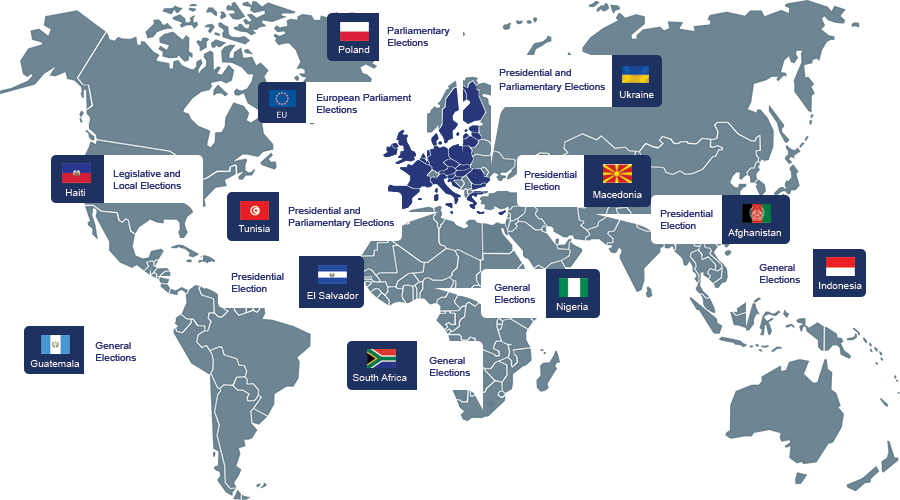
The Fight Against Fake News Will Buckle Under the Pressure of Various Elections
The giant role of social media in past elections, particularly its use in spreading fake news, painted a picture of the kind of challenges that other countries would face. Several factors contribute to the persistence of fake news: motivation, availability of tools, and accessibility of platforms. Governments have expressed interest in regulating social media platforms, but there will not be enough time to clear the internet “airwaves” of fake news.
The improvements social media has made to fight fake news post-2016 will not be enough to keep up with the deluge of cyberpropaganda surrounding voting exercises in 2019. Adding to the technical difficulty of tamping down fake news is the existence of different languages in large geographic areas like the EU.
Innocent Victims Will Get Caught in the Crossfire As Countries Grow Their Cyber Presence
Targeted attacks will continue among traditional players, but in 2019, even countries not usually called out will be involved as well. Nations that are firming up their cyber capabilities will seek to support and empower domestic hackers, either in preparation for or in response to perceived or prior attacks.
Unfortunately, these developments will have spillover effects on innocent victims completely unrelated to these cyber responses. We already saw this happen with WannaCry and NotPetya — the collateral damage will only increase.
Cybercriminals Will Use More Techniques to Blend In
In response to security vendor technologies, specifically the renewed interest in machine learning for cybersecurity, cybercriminals will use more malicious tactics to “blend in.” New ways of using normal computing objects for purposes other than their intended use or design — a practice known as “living off the land” — will continue to be discovered, documented, and shared.We have been observing a few of these.
Enterprises relying on machine learning technology as their sole security solution will be up for a challenge as more cybercriminals use these techniques, among others, to infect systems. We expect such cybercriminal tactics to become much more pronounced in 2019.
99.99% of Exploit-Based Attacks Will Still Not Be Based on 0-Day Vulnerabilities
Zero-day exploits have been a point of focus in IT security because of:
- The existing infrastructure of responsible disclosure that rewards vulnerability researchers for their findings, including Trend Micro’s Zero Day Initiative (ZDI).
- The fact that all it takes is the discovery of an attack for vendors to be prompted to take proper action.
The most accessible opportunity for cybercriminals is the window of exposure that opens up between the release of a new patch and when it is implemented on enterprise systems.
In 2019, successful exploit-based attacks will involve vulnerabilities for which patches have been available for weeks or even months but have not been applied yet. We will continue to see cases of n-day exploits being a bane in network security.
Real-World Attacks Targeting ICSs Will Become a Rising Concern
Countries expanding their cyber capabilities will conduct attacks against smaller players’ critical infrastructure. They will do so to gain political or military advantage, or to test out capabilities against countries that do not yet have the capacity to retaliate, among other possible motivations.
Whether the attacks will hit water, electricity, or manufacturing industrial control systems (ICSs) will depend on the threat actor’s intent or opportunity. But they will highlight weaknesses such as those meant to be curbed by the EU NIS Directive with its regulations for operators of essential services.
A successful ICS attack will affect the target facility with operational shutdowns, damaged equipment, indirect financial losses, and at worst, health and safety risks
More Cloud-Related Software Vulnerabilities Will Be Discovered
Both Docker, a containerization program, and Kubernetes, a container orchestration system, are widely adopted for use in cloud-based deployments. There have already been a few Kubernetes vulnerabilities disclosed in recent years and a “critical” security issue was discovered just before the close of the year. Meanwhile, more than a dozen malicious Docker images were found by Kromtech to have been downloaded at least five million times over a span of a year before they were pulled out.
As more enterprises migrate to the cloud, we will see cloud infrastructure vulnerability research gain ground, especially as the open-source community finds more uses for and digs deeper into cloud-related software.
Cybercriminals Will Compete for Dominance in an Emerging IoT ‘Worm War’
Routers will continue to be an attractive attack vector for cybercriminals wanting to take control of any number of connected devices. We will see a repeat of the so-called “worm wars“ in the outbreak era of the early 2000s in smart homes.
Recent router-based attacks that affect smart devices, or IoT attacks, are mostly based either on the same leaked source code from the Mirai malware or from other similarly behaving malware. They are all auto-scanning the internet and discovering the exact same devices.
Since there are a finite number of devices and only one piece of malware needs to be in control of a single device to perform distributed denial of service (DDoS) and other attacks, cybercriminals will begin adding code to lock out any other hacker from using the device or kick out an existing malware infection to become its exclusive controller.
The First Case of Senior Citizens Falling Easy Victims to Smart Health Device Attacks Will Emerge
The first few real-world victims of a smart health device attack will be seniors. Companies are exploring the senior citizen customer base as potential users of smart trackers or other internet-connected health devices, such as those that monitor heart rates or send alerts to connected accounts when the elderly user slips or falls. In the past, senior citizens have been targets of phone scams because of their relative wealth, given their retirement savings.
We believe that we will see seniors becoming easy victims of attacks that abuse these devices as early as 2019. Elderly users of health trackers will not be computer-savvy enough to check the privacy settings of these devices (resulting in data leakage) or to keep their accounts secure (allowing cybercriminals to access health-related and other personal data).
More Unknowns Require Intelligent Multilayered Security for Enterprises
The realities of modern hybrid data center architectures and evolving endpoint/end-user access and mobility — including partners and other third parties that connect to the network — will demand a lot more from IT security teams in 2019.
The IT security skill set shortage will thus become more pronounced, and augmenting existing expertise with intelligent, efficient, and multilayered security technologies will become more critical.
Developers Must Embrace DevOps Culture With Security as a Focus
DevSecOps — DevOps with a focus on security — leads to strong security practices and baked-in security every step of the way. Software developers should adopt this mindset, along with its practical range of tools, in order to reap not only security benefits but also cost reductions.
Users Must Take up Responsible Digital Citizenship and Security Best Practices
Users must apply the same level of critical thinking to their social media sharing behavior as to their diligence in checking whether an email or a phone call is indeed coming from a trusted source.
The ability of internet users to distinguish truth from untruth in 2019 will become more important. Spreading awareness of the mechanics behind fake news will hopefully make the public more resistant to opinion manipulation.
For account protection and data privacy, users should change their passwords regularly, have unique passwords for different accounts, take advantage of multifactor authentication features whenever possible, or use a password manager tool to help store credentials securely.
Smart home users must secure their routers and devices.
The threat landscape promises a lot of challenges for almost all sectors of the internet-using public in 2019. A deep understanding of these issues is a step in the right direction.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- The Industrialization of Botnets: Automation and Scale as a New Threat Infrastructure
- From Holiday Snap to Custom Scam in 30 Minutes: How AI Turns Public Photos Into Targeted Attacks
- From LinkedIn to Tailored Attack in 30 Minutes: How AI Accelerates Target Profiling for Cybercrime
- Threat Attribution Framework: How TrendAI™ Applies Structure Over Speculation
- AI Skills as an Emerging Attack Surface in Critical Sectors: Enhanced Capabilities, New Risks


 The Industrialization of Botnets: Automation and Scale as a New Threat Infrastructure
The Industrialization of Botnets: Automation and Scale as a New Threat Infrastructure AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One