Australian Health Insurance-Themed Spam Spreads Ursnif
 Analysis and Insights by Monte De Jesus
Analysis and Insights by Monte De Jesus
Trend Micro researchers encountered a spam campaign referencing the Australian health insurance brand Medicare. The attachment, which Trend Micro detects as Trojan.X97M.URSNIF.THDAEBO, downloads the malicious file (detected as TrojanSpy.Win32.URSNIF.THDAEBO). The campaign aims to spread the spyware Ursnif, also known as Gozi.
The email headers pertain to payment transactions with the words “Statement,” “Invoice,” or “Transaction,” and include a supposed transaction number:
- RE: Statement 21833187
- RE: Invoice 187790985
- RE: Transaction 1214860391
The email contains an attached encrypted spreadsheet (.xls) file (detected by Trend Micro as Trojan.X97M.URSNIF.THDAEBO) that uses “Medicare” in its file names, as listed below:
- Medicare - 1214860391.xls
- Medicare - 187790985.xls
- Medicare - 21833187.xls
- Medicare - 577725932-577725932.xls
- Medicare - 656187332.xls
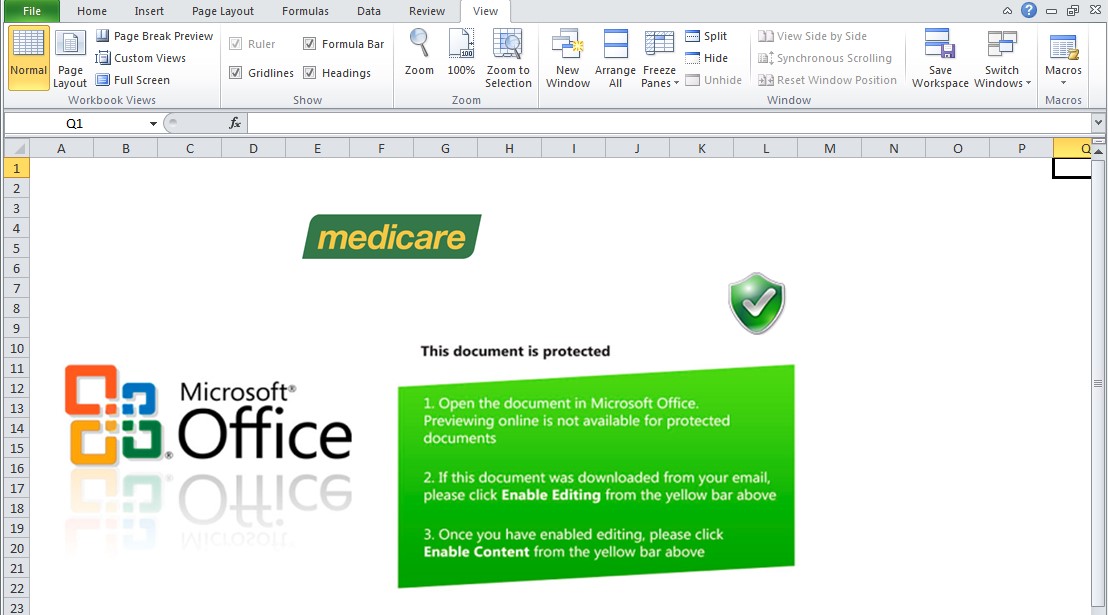
Figure 1. Healthcare-Themed Spam Attachment
This trojan accesses the website hxxps://www.{BLOCKED}contracting.com/ray/pom.php. It then downloads a malicious file (Ursnif) from the site and saves it using the name %All Users Profile%\qmbvlcq.exe (detected as TrojanSpy.Win32.URSNIF.THDAEBO).
This malicious file steals the following data, which can possibly be abused for further attacks:
- Computer Name
- Machine Globally Unique Identifier (GUID)
- Operating System Type
- Operating System Version
- System Uptime
- Username
The file then sends the information via HTTP POST to the following URL:
- hxxps://{BLOCKED}cos.xyz/index.htm
Earlier this year, Ursnif has been spotted being used in another campaign targeting users in Japan.
Defense Against Spam Campaigns
Threat actors use current affairs such as the Covid-19 outbreak in their social engineering strategies to bait even the most careful email users. Spam campaigns can propagate malicious files such as Ursnif and other types of malware and even ransomware. Users can defend against these threats by following these best practices:
- Do not download links and click attachments from emails sent by unfamiliar sources.
- Spot telltale signs of spam like bad grammar, misspellings, and spoofed email addresses.
- Verify the legitimacy of emails from official sources through other means of communication, such as phone calls.
The following Trend Micro solutions for email-based threats are recommended for a more proactive defense against spam:
- Trend Micro™ Email Security – Scrutinizes email headers and content to detect spam and other email-based threats.
- Trend Micro™ Deep Discovery™ Email Inspector – Analyzes patterns and reputation to detect malicious files that come with spam emails.
- Trend Micro™ Cloud App Security – Conducts sandbox malware analysis and detects impersonation of writing styles in emails.
Indicators of Compromise
URLs
- hxxps://www.{BLOCKED}contracting.com/ray/pom.php
- hxxps://{BLOCKED}cos.xyz/index.htm
| SHA-256 | Trend Micro Pattern Detection |
| 35a5cb85a5fbea3fdbd568aacedca42c4488877c1c2ee479fe21c1534e070866 | TrojanSpy.Win32.URSNIF.THDAEBO |
| 3f713f94f2c6c981a93cc9e01894da2da3a144829093619eb960f469e245fa17 | Trojan.X97M.URSNIF.THDAEBO |
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One