Cybercriminal ‘Cloud of Logs’: The Emerging Underground Business of Selling Access to Stolen Data
By Vladimir Kropotov and Fyodor Yarochkin
There has been an unprecedented increase in the adoption of cloud-based services and technologies over the years. This increased adoption is prompted by companies that are adapting to evolving industry landscapes through digital transformation — a move that allows them to be more agile, scalable, and cost-efficient. However, the benefits of using cloud services and technologies are not just reaped by legitimate companies, but also by cybercriminals who keep up with the trend.
We have seen several underground business models offering cloud-based services and technologies, which we also previously touched upon in our research on the commodification of cybercrime infrastructures. In this latest research, we dive deep into a growing underground market that is driven by malicious actors who sell access to troves of stolen data, which are frequently advertised in the underground as “clouds of logs.” Some malicious actors host their clouds of logs in their private cloud-based platforms, which can be conveniently accessed by customers via tools for analyzing and extracting the data that they need to conduct malicious activities.
Organizations, whether or not they use cloud-based services and technologies, are at risk from criminals taking part in this relatively new market for selling and buying stolen data. Criminals who use the cloud to optimize their attacks expose more than the users whose credentials were stolen. Ultimately, the organizations that these users are part of are also placed at risk since criminals could reuse stolen credentials to subsequently enter organizations’ IT premises. In fact, a 2019 report reveals that 80% of hacking-related breaches were caused by compromised, weak, or reused credentials. With the emerging market for clouds of logs, criminals who are on the prowl for stolen credentials that they can use to victimize organizations could find more opportunities to launch attacks, thereby potentially exposing organizations to a higher number of intrusion or compromise attempts.
This article discusses these findings in detail, including the varying types of data sold in the market, their price ranges, and our insights into how such a market could evolve in the future.
The commodification of stolen information through clouds of logs
The business of selling access to a gargantuan amount of data (with cloud account credentials being one of the many popular fixtures) is another type of cybercriminal venture that branches out from identity theft and the trade of stolen information — both of which are major threats to organizations and ordinary individuals.
In recent years, the theft of user credentials has been on the rise, with attackers collecting massive amounts of credentials and associated email addresses or domain names. Stolen credentials and web browser sessions are also up for sale and can be effectively obtained and used by criminal groups. Attackers who prefer larger prey might see an opportunity in reusing the stolen credentials of employees, as these can be utilized to enter the IT premises of the organizations that the employees are part of.
With the introduction of cloud-based services and technologies, criminals are equipped to steal, purchase, and use data to conduct their attacks much faster when targeting organizations. As an analogy, we can compare the effectiveness of a criminal trying to obtain their tools at a garage sale versus trying to buy them from an online shopping site. The ease afforded to cybercriminals when they use cloud-based services and technologies, similar to the ease afforded to online shoppers, would in turn make it difficult for organizations to anticipate the arrival and execution of attacks. It is worth stressing here that these attacks are particularly dangerous not only because these are enabled by stolen data, but also because they are orchestrated by criminals over a very short period, leaving organizations with less time to detect these attacks and respond to them accordingly.
The capability to conduct such attacks with convenience and effectiveness naturally increases the demand for data available in the underground market. Such information often includes recorded keystrokes, authentication credentials to online portals, online banks, authenticated session attributes, personally identifiable information (PII), scans of documents, tax reports, invoices, bank account payment details (such as those that involve credit cards), and more.
With the exponential growth of cybercrime, some criminal gangs might be operating on massive amounts of valuable data. However, it is likely that they are unable to exploit the full potential of such a colossal amount of data. This has paved the way for a pay-for-access scheme that allows other cybercriminals to monetize the data that they extract from sellers’ clouds of logs.
Various services in the underground that rent access to clouds of logs
Cybercriminals exfiltrate massive amounts of data when they successfully launch cyberattacks that involve ransomware, botnets, keyloggers, exploit kits, and other malicious components. Additionally, information stolen by criminals might include browsing history, cookies, keystrokes, user credentials, authentication tokens, information about the victim environment that can be used to evade anti-fraud systems, and more.
In our analysis, the amount of data collected by these criminals from the aforementioned attacks exceeds terabytes. However, precisely because of the gargantuan amount of data, it is unlikely that a single threat actor or even a single group of cybercriminals would be able to make full use of it all. In order to milk their opportunities further, cybercriminals have found a way to monetize the excess by letting other cybercriminals rent access to their clouds of logs. Since a lot of the data from such platforms is exfiltrated from compromised end-user and corporate systems and various cloud platforms, such data could be used to conduct further criminal activities.
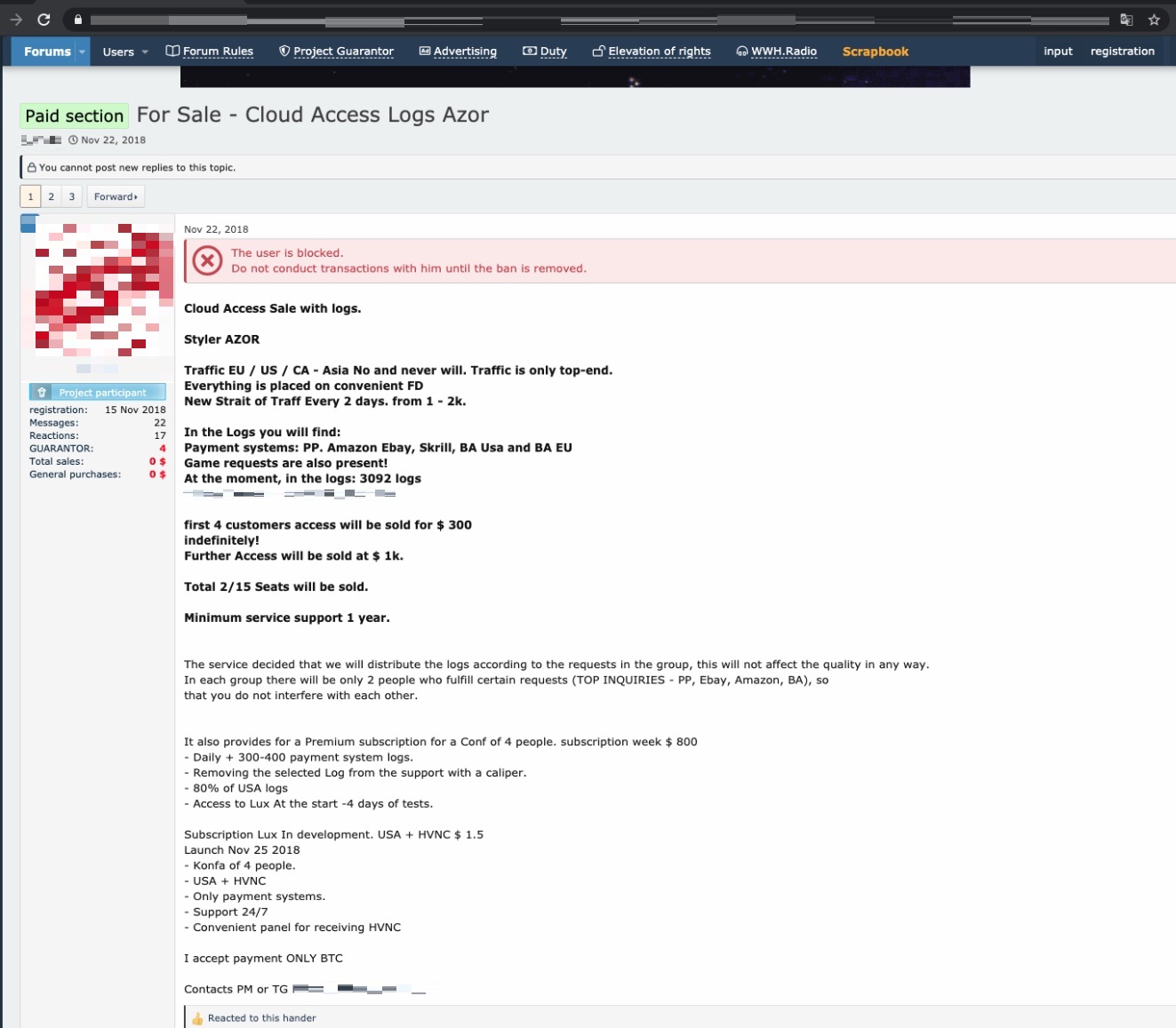
Customers pay to access these datasets at varying price ranges. Packages that only allow limited access and downloads are in the hundred-dollar ranges. Monthly subscription rates are also offered, with some cybercriminals pricing them within the US$300 to US$1,000 range. For example, Figure 1 shows a screenshot of an advertisement that offers a lifetime membership for US$900.
Meanwhile, another actor offers a similar service; however, they claim to update their dataset with new stolen accounts on a weekly basis. The service offers a premium subscription for US$300 for the first four customers, while further access is priced at US$1,000.
Figure 2. The seller offers data from companies like Amazon, eBay, and Skrill, among others.
The same seller in Figure 2 also advertises another dataset with about 100,000 logs. Additionally, they say that the distribution of the dataset is limited and that only five copies will be sold. In the underground market, it is common for service providers to limit the number of items that they will sell to customers. Indeed, data sold in a limited number of copies tends to merit a higher price since fewer people can monetize from it. This strategy is similar to that used by sellers in legitimate marketplaces, where premium goods are more expensive than the ones that are produced for mass consumption.
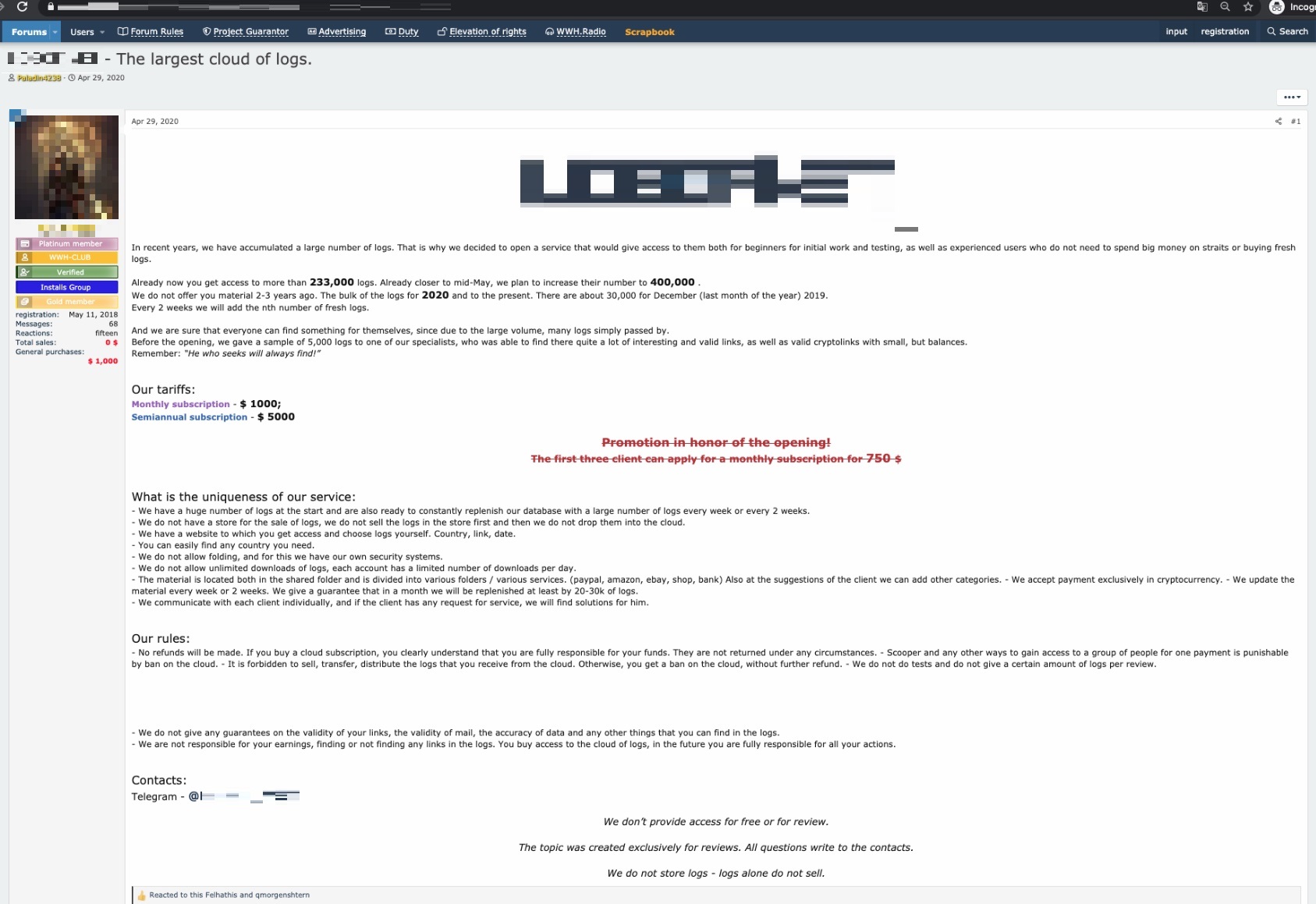
In another instance, we saw an advertisement of a service that guarantees updates of new batches of data ranging from 20,000 to 30,000 logs every one to two weeks. A monthly subscription costs US$1,000, while a semiannual subscription costs US$5,000.
Figure 3. This advertisement guarantees interested customers with new batches of 20,000 to 30,000 logs every one to two weeks.
Here is the breakdown of popular sellers of logs in the underground, including various details of the logs that they sell, and their price ranges.
| Seller | Package details such as volume of data, types of data, regularity of updates, and others | Price or subscription range/s |
| Seller 1 | 1.2 TB of logs | US$350/month, US$900/lifetime |
| Data belongs to entities based in various countries | ||
| Seller 2 | Focuses on corporate accounts | US$100/week, US$350/month |
| Active on Telegram | ||
| Seller 3 | 600 GB of logs for carding | US$600/month (EU-related info), US$800/month (US-related info), US$1,500/month (most recent; mix of EU- and US-related info) |
| With weekly updates | ||
| Seller 4 | About 400,000 logs | US$1,000/month, US$5,000/biannual |
| With quotes for downloads per day | ||
| Logs normalized and sorted by many categories including geolocation and categories of accounts like PayPal, Amazon, eBay, banks, and shops | ||
| Seller 5 | More than 50 GB US and EU logs | US$300/lifetime |
| Over 100,000 logs | ||
| With weekly updates of at least 5,000 new entries | ||
| Seller 6 | 300 GB | US$2000/lifetime |
| 500,000 logs | ||
| With two to three updates per month | ||
| A mix of US-, CA-, FR-, DE-, EU-, and Asia-related info | ||
| Seller 7 | 3 TB compressed logs previously used for the monetization of well-known services like crypto wallets and PayPal | US$100/lifetime |
| With monthly updates |
Table 1. A summary of popular log sellers and some details about the packages that they offer
Based on details that are highlighted by sellers and mentioned by customers, the sizes of logs are often measured in either gigabytes or number of log entries. Some actors advertise the size of collected data stored in plaintext, while others measure the accumulative size of the archived data. This means that the volume of data in 500 GB by one actor could be 50 GB for another actor, because the latter takes into account the size of the data when it is compressed.
Sellers also sometimes advertise data volume by indicating the number of log entries. It is important to note that one log entry is not normally limited to including just a combination of login and password credentials, or even just cookies stolen from the victim host. Rather alarmingly, one log entry can contain so much more, including dozens of credentials for corporate accounts, public email services, social networks, payment systems, banks, and government services. Such log entries also often contain detailed information about the software environment and sensitive data collected from browsers.
Some advertisements indicate the countries or the regions where the data is sourced. Details concerning data type are also often included. For example, data type could refer to whether the data was preprocessed and sorted according to possible monetization paths.
Notably, the price for accessing different datasets varies depending on whether or not the logs had already been used in previous monetization schemes. For instance, two sellers who offer datasets of the same size could price their datasets differently, as the data that had already been monetized in a previous scheme might sell at a lower price.
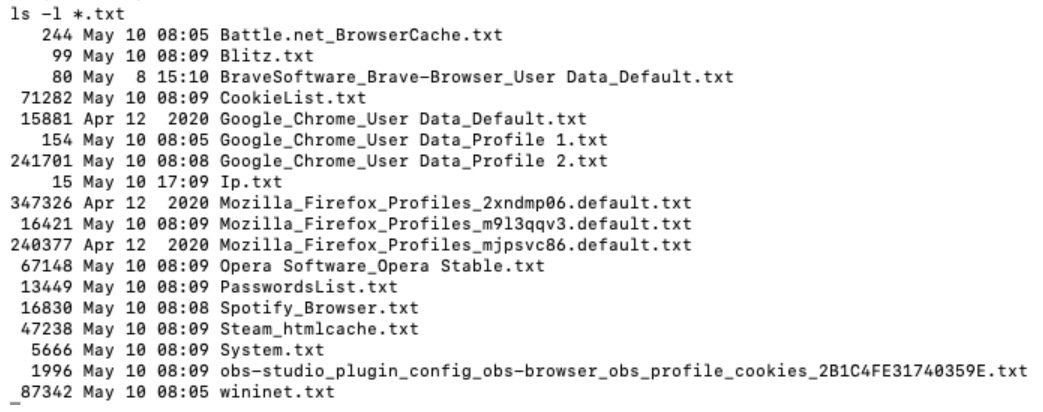
The content of the datasets, which we will expound on in the succeeding section, typically contains a wide variety of logs, including PII, credit card information, and account credentials that are used for access to cloud services such as those offered by PayPal, Amazon, Google, and more. Figure 4 shows a sample list of some information that can be found in a single log.
Figure 4. A screenshot of the list of information found within a single log
Criminals who buy access to these datasets also vary in their specializations. Some of these criminals primarily focus on carding activities, while others specialize in attacking financial institutions and seek banking credentials. Credentials for accessing cloud platform portals are also sold to those criminals who specialize in selling bulletproof-dedicated services. Such credentials could be used to spawn instances of virtual machines that are then sold in underground markets.
What is the advantage of buying such logs from uniform platforms like the ones that we previously mentioned, compared with the old practice of obtaining these logs individually? The capability to scale operations is one factor. With the use of cloud technologies, criminals are provided more computing power, storage, or bandwidth to optimize their operations.
In addition, with the availability and variance of stolen information in such platforms, criminals only need to search for the data that they need in order to find an opportunity to commit a crime faster; after all, they won’t have to bother with obtaining data themselves anymore. Such data (which includes sensitive account credentials) could potentially leave organizations with unsecure accounts that are vulnerable to attacks. If targeted organizations have weak security in place to begin with, then the chances are even higher that they would not have enough time to detect a breach and employ the appropriate response actions to contain and remediate it. Naturally, the availability and variance of information could also enable criminals to target a larger number of victims.
An inside look into the logs
We analyzed several data samples from forums and online platforms. We also reviewed the advertised features and feedback from buyers. This allowed us to build a more complete picture of what is actually inside the logs that criminals pay to access.
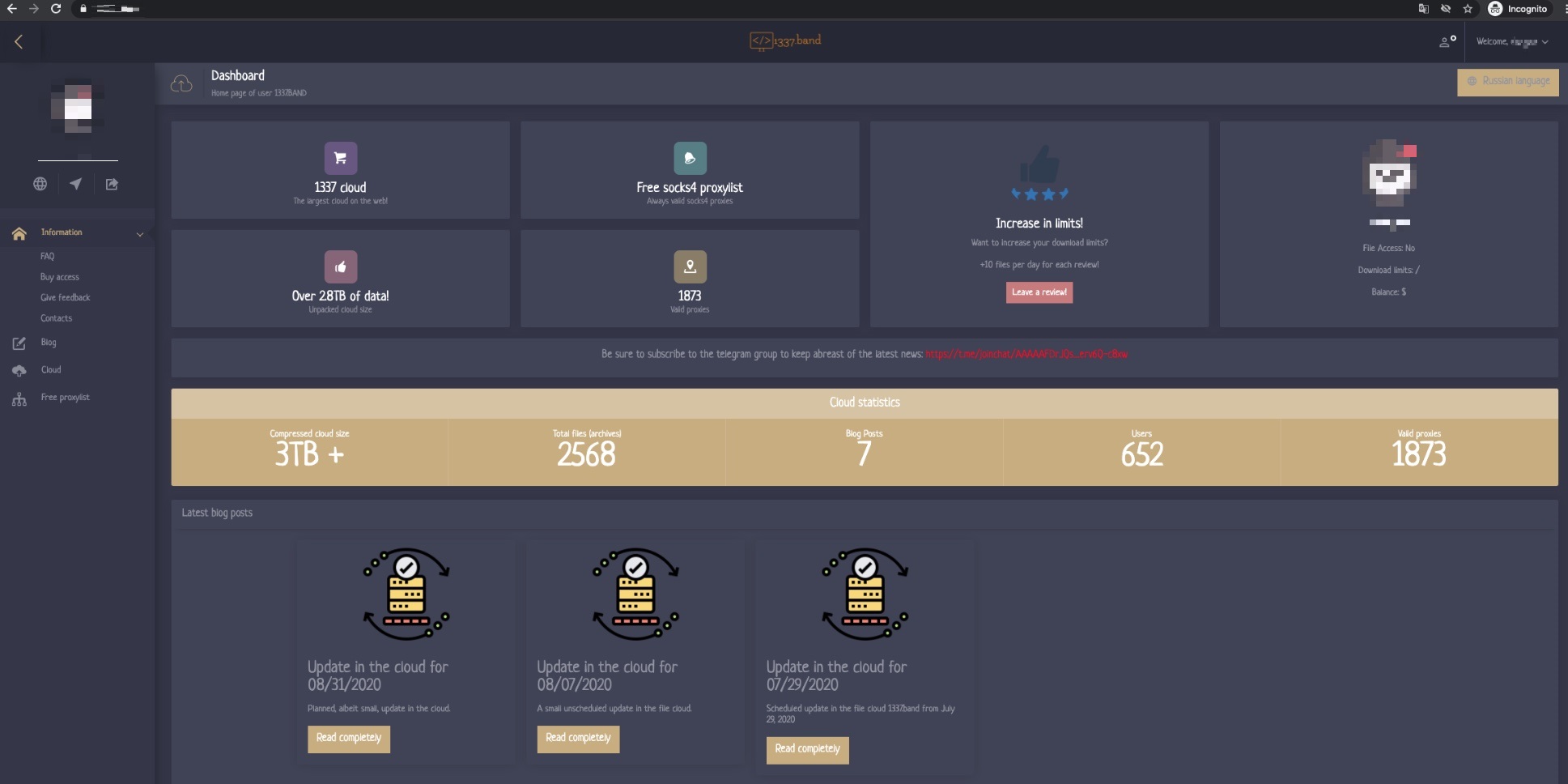
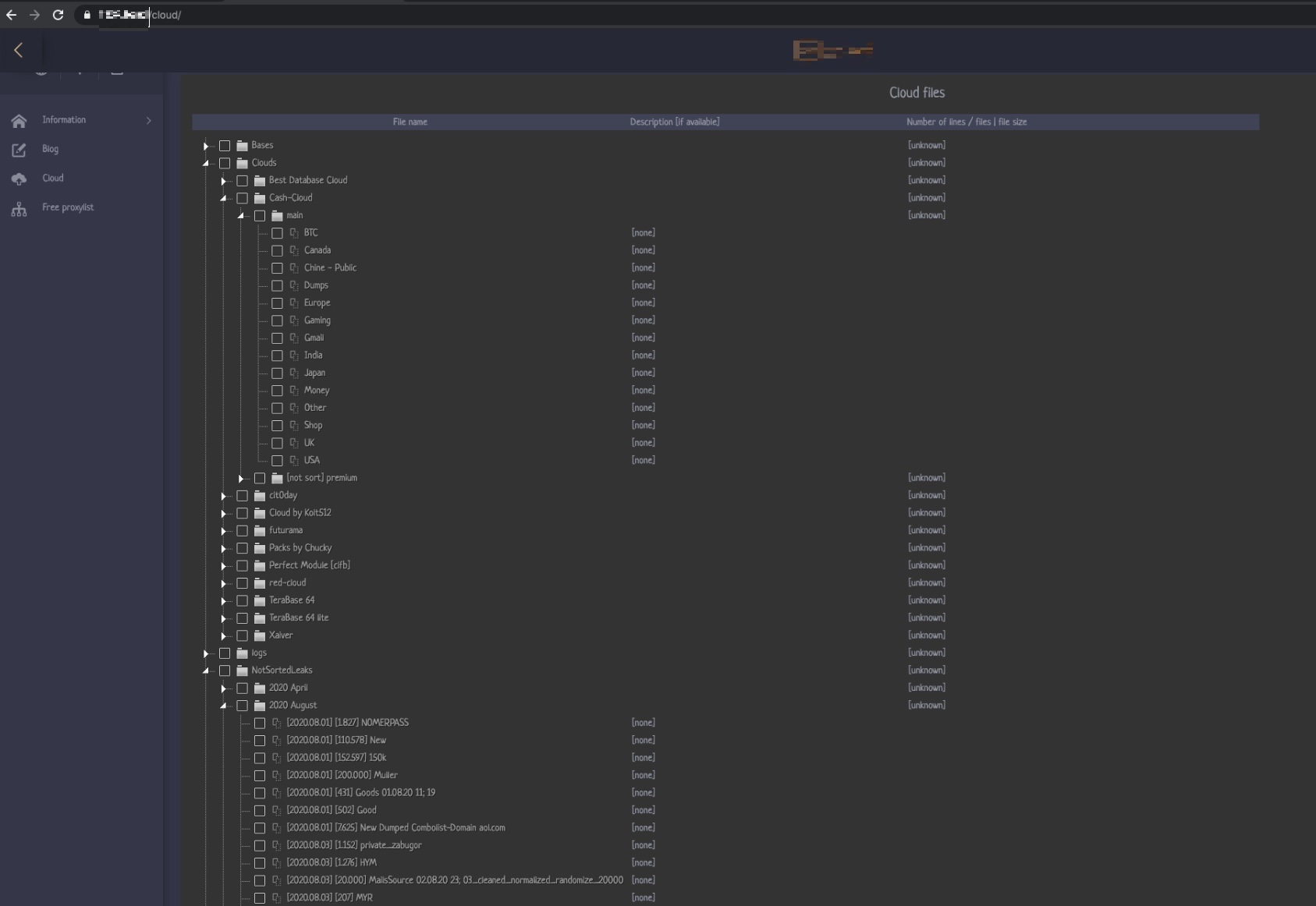
Figure 5. This service provides access to multiple cloud services. On this page, the seller claims to have accumulated more than 3 TB of compressed data.
Many cloud platforms that are used by sellers offer preprocessed and normalized data from a variety of keyloggers, information stealers, and other types of malware. The information is structured and stored inside files. Each file name and/or file path contains the category information of the data. Often, data that is stored in the platform is analyzed first by whoever provides that information. That actor could then extract and use bits of information that they find useful, while the rest of the data would be left in the platform. How the attacker exploits or monetizes the data depends on the attacker’s specialization and skill set. For example, it is very common for attackers to seek credentials to popular services such as eBay, PayPal, Amazon, Qiwi, or cryptocurrency wallets because stolen credentials from these sites allow them to steal money from the linked accounts or to immediately execute certain fraudulent schemes.
Figure 6. This page, which is owned by the same seller in Figure 5, shows the category details of the logs that they offer to potential customers.
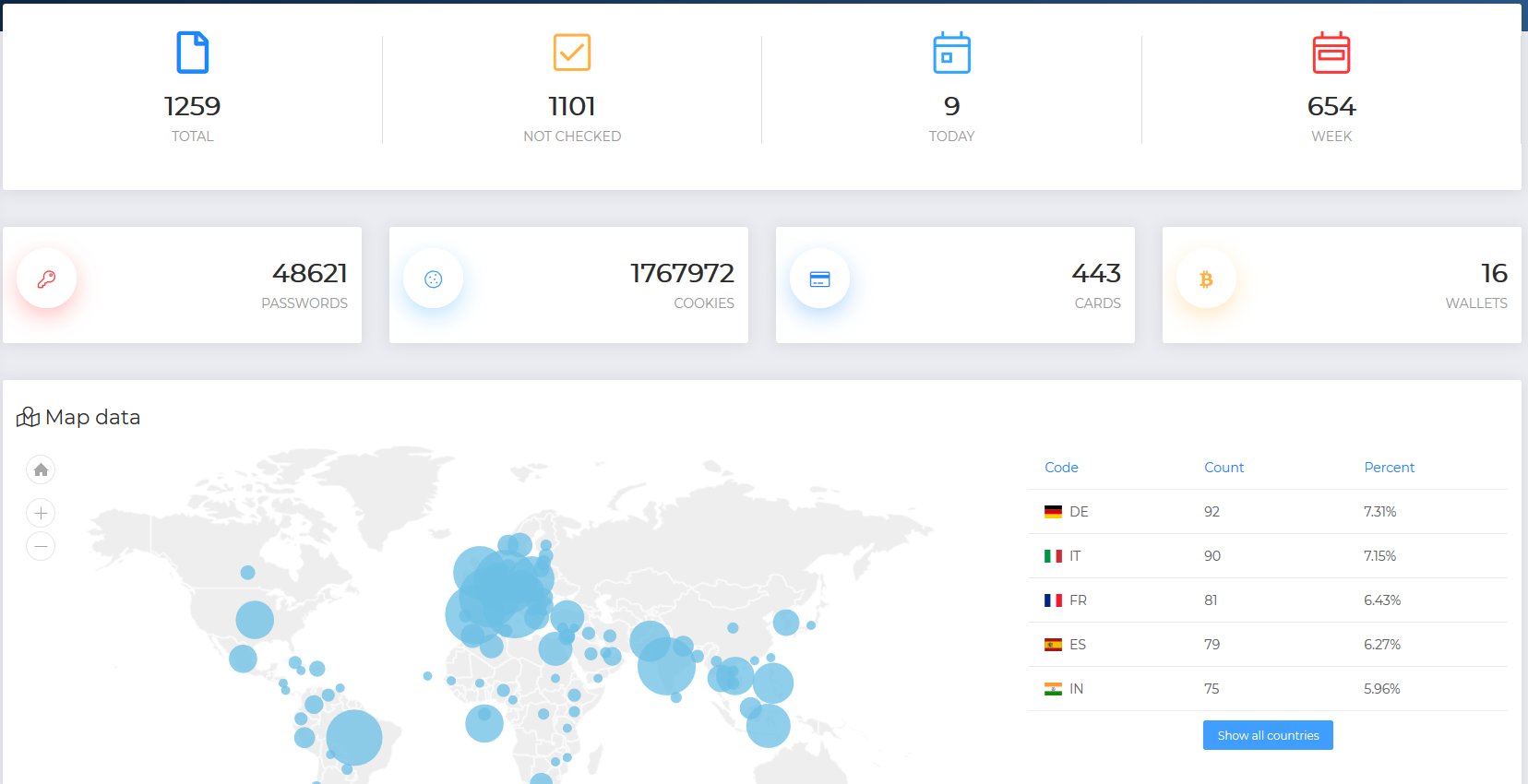
Figure 7. This screenshot shows another seller’s offerings, which include varying types of data like passwords, cookies, cards, and wallets. Their webpage also shows the location distribution of the data that they offer.
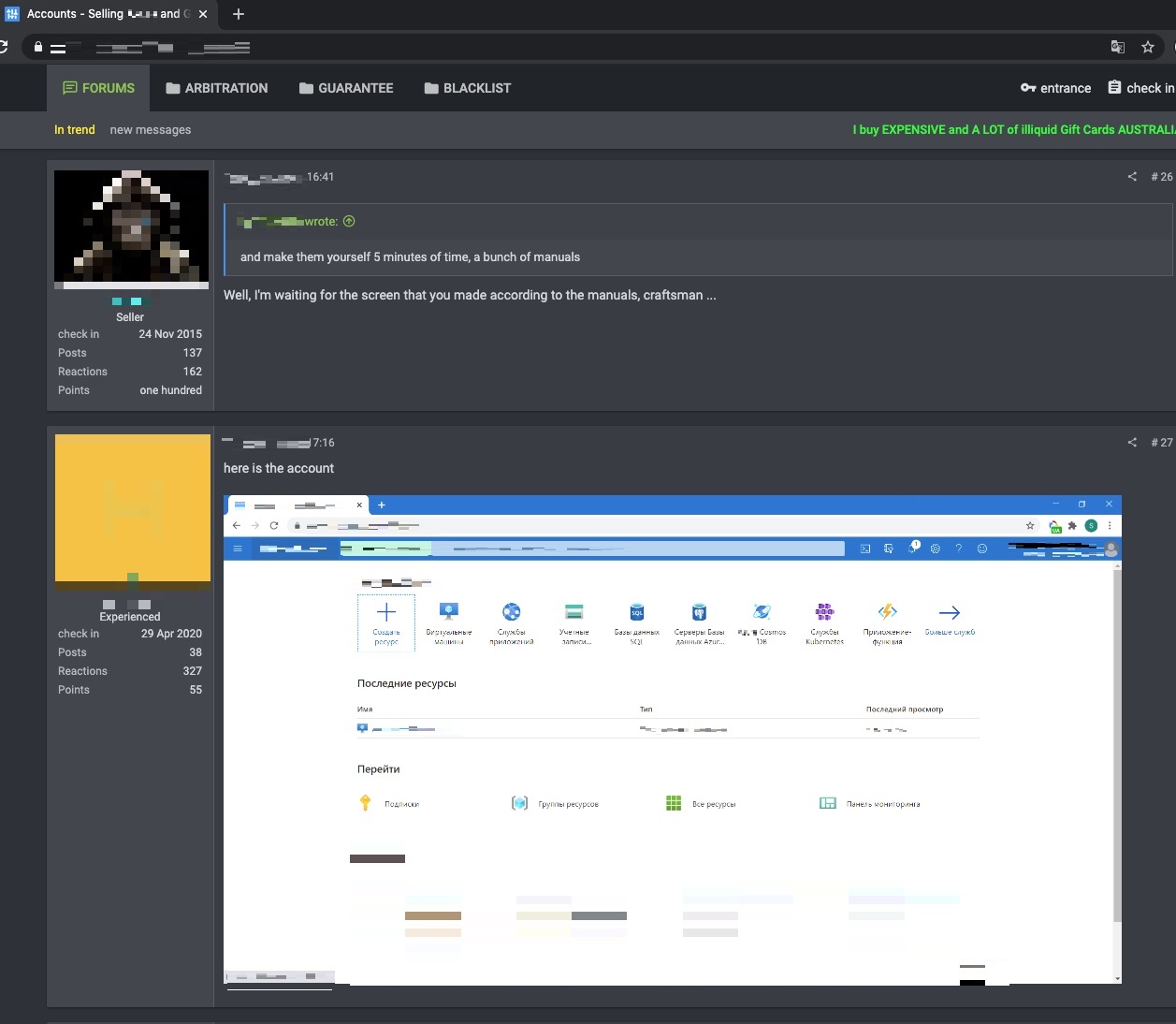
Other sellers also provide supposed proofs of existence for the accounts that can be accessed using the stolen credentials that they offer. In Figure 8, a seller posts a screenshot of one such account.
Figure 8. To add credence to their offering, a cybercriminal shows a screenshot of the compromised account that is accessible through stolen credentials.
Often, almost all sellers explain the kind of data that is available to potential customers: They clarify the size of the logs, how often the dataset is updated, and the type and quality of data that they have in their platforms. They also often introduce restrictions on how the data and the interface can be used. For example, they strictly prohibit bulk-dumping of a whole dataset and sharing data with a third party or other actors. Violating such restrictions are often punished with account suspension.
As discussed earlier, many sellers also limit the number of people who can access and buy logs. They also implement data watermarking and other tracking methods to enforce their service-level agreements (SLAs). Among these restrictions are fixed quotes on the total number of accessed objects per day, a restriction on the number of files permitted for download, or the implementation of traffic-shaping policies. Other platforms also restrict access to the cloud to one device per account. Some also require private VPN credentials to initiate access to the service.
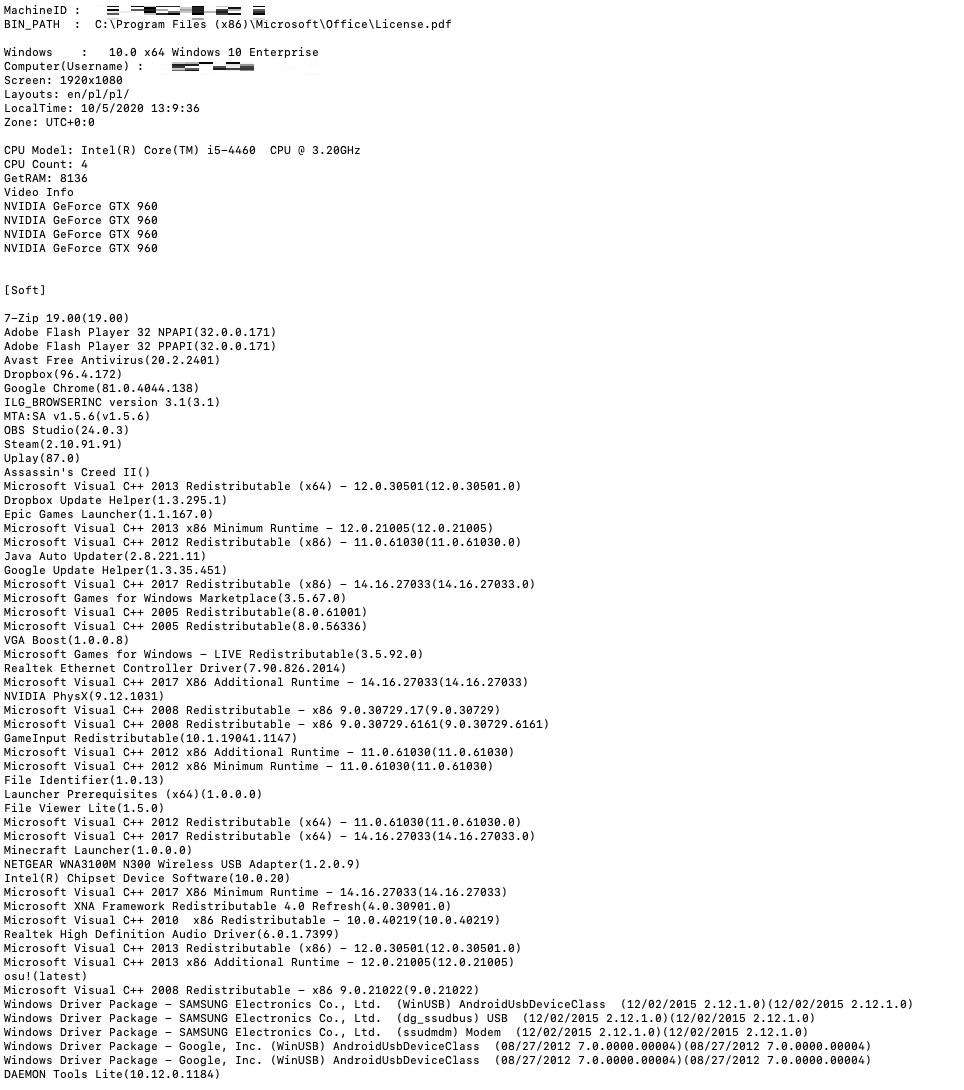
Among the available samples, we have seen many logs in the format of AZORult Stealer logs. AZORult Stealer logs normally contain victims’ IP addresses, logged credentials to a variety of websites in the form of SOFT (credentials sourced from software) to access the website, HOST, and USER and PASS credentials. In addition, these logs normally contain cookies from browsers and information stored in AutoComplete. Some attackers also know how to effectively use this information to bypass the fraud detections of some financial organizations by creating software environments that match the victim machine.
Figure 9. Example of a log with software and hardware environment information collected from a victim machine
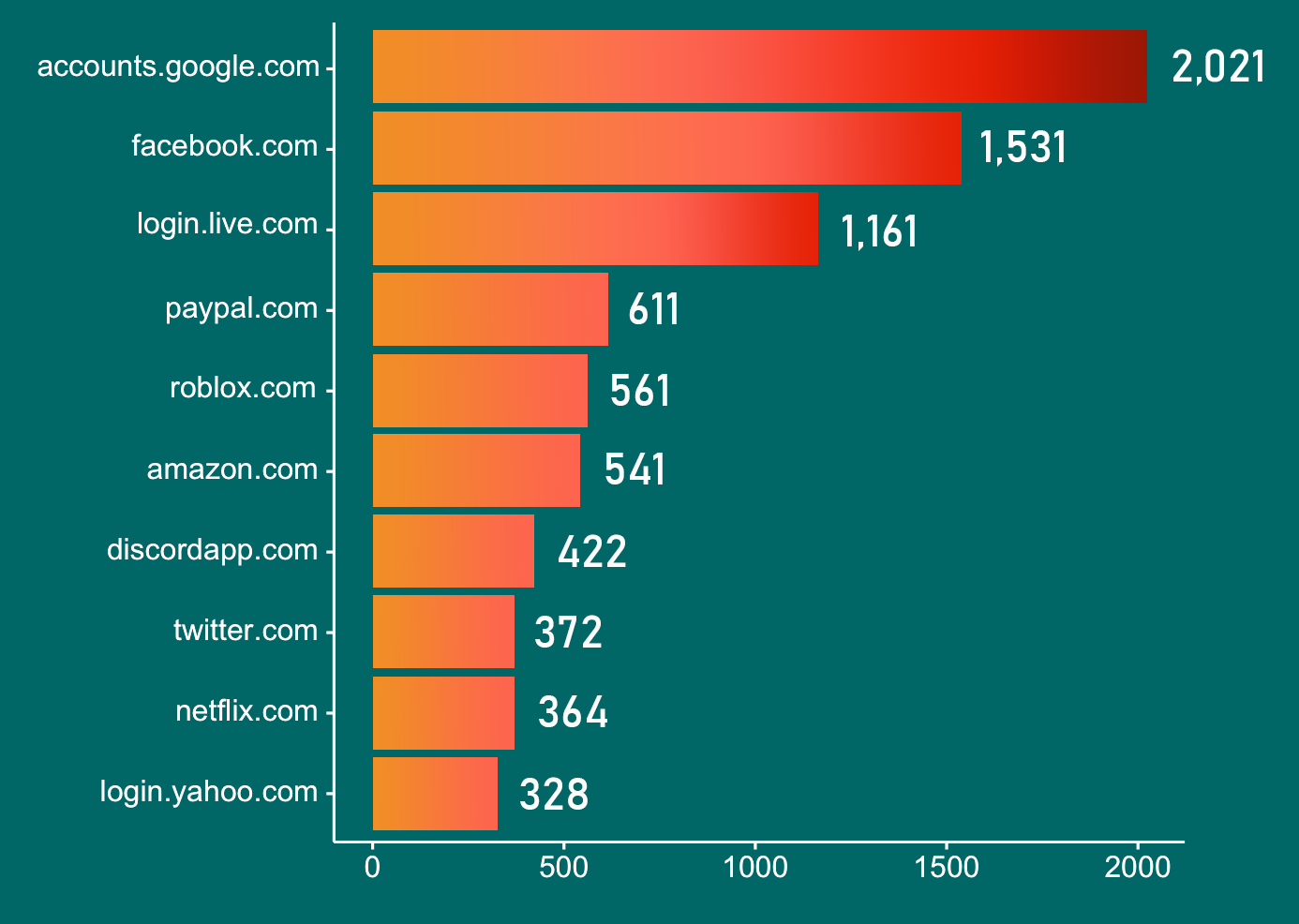
In a sample dataset of 1,000 logs, we identified a total of 67,712 URLs and conducted a short analysis. The chart in Figure 10 shows a breakdown of the top 10 sites with the most stolen credentials based on the log samples that we analyzed.
Figure 10. The distribution of the 10 sites from which most credentials were stolen based on our analysis of a sample dataset. Google tops the list, followed by Facebook, Microsoft, and PayPal respectively.
The use of tools for log analysis and exfiltration
While there are malicious actors who simply use tools like Total Commander or the search bar to look for logs, some automation tools are available for managing the massive amount of information that is stuffed into the sellers’ storage platforms. We have seen these data analysis and extraction tools (some of which are cloud-based) often discussed in underground platforms and sold in the underground market. These tools are deployed for bulk processing of stolen data.
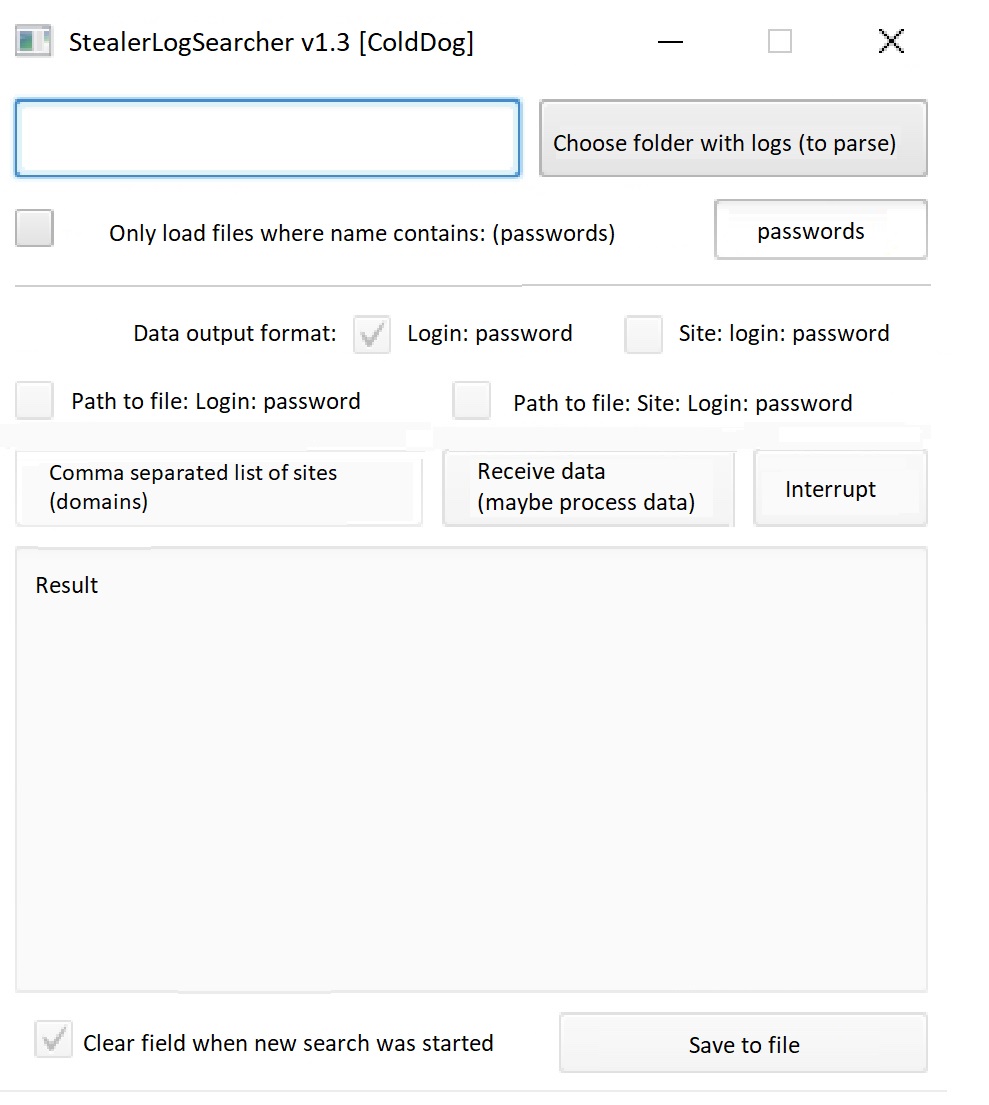
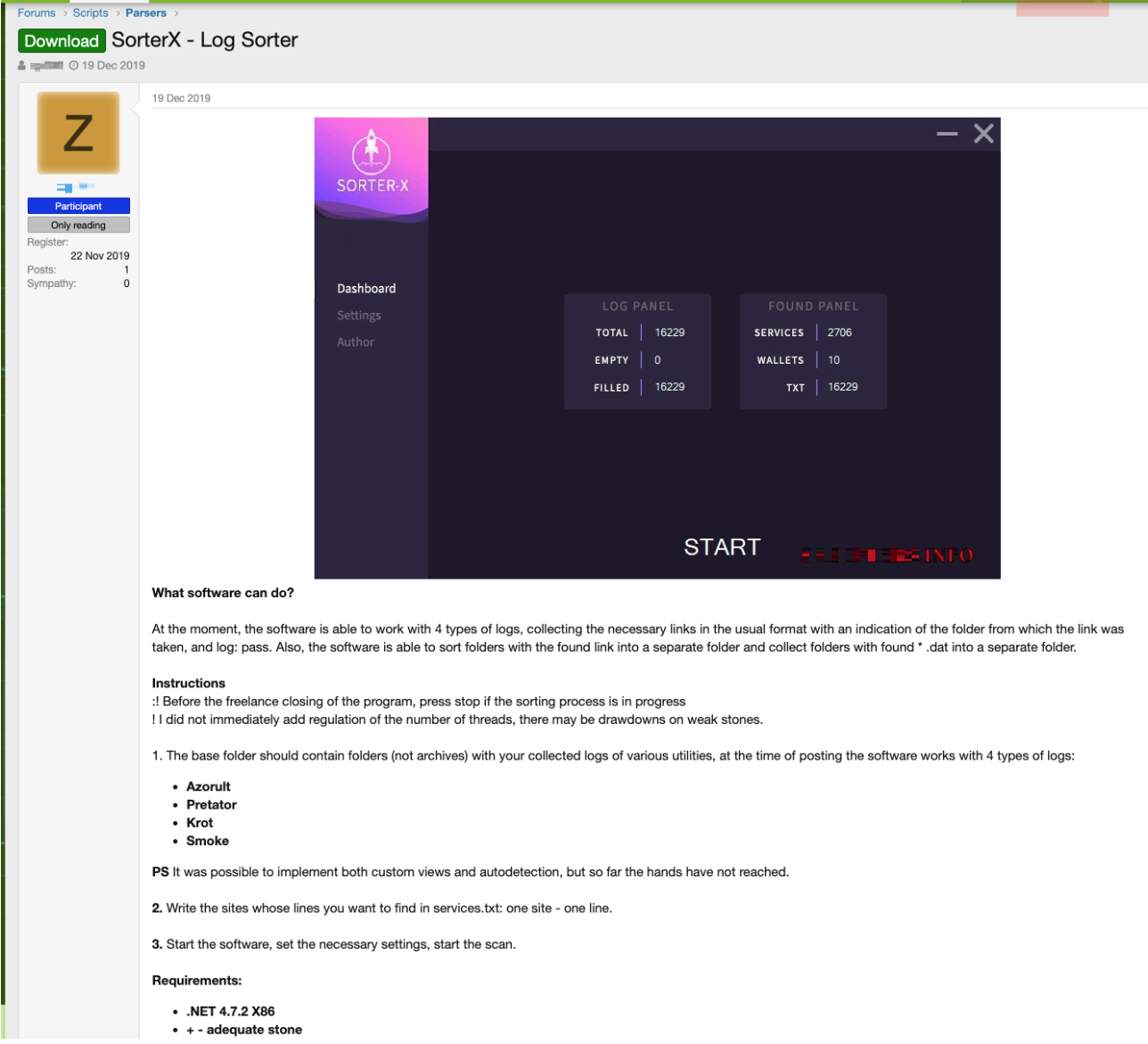
There are several automation tools used for processing credentials, sifting through large amounts of data, or performing manipulations on datasets obtained from the cloud of logs. Among the tools available in the underground, StealerLogSearcher v1.3 and SorterX are two software programs that are widely used for data analysis and exfiltration. Both tools save criminals from having to spend more time and effort in manually searching for and extracting data.
Figure 11. A screenshot of StealerLogSearcher v1.3 — a tool used to sift through massive amount of logs
StealerLogSearcher v1.3 is a tool that allows cybercriminals to quickly search through massive amounts of data by specifying “strings” of interest and log analysis. The tool allows users to search through the data — regardless of the source of logs — for occurrences of user credentials that match a particular site. It also allows users to provide output in the form of file name, user:password, or URL. Data analyzed by StealerLogSearcher has to be downloaded on the local disk before being analyzed. This tool is frequently used by criminals who are trying to find credentials for particular websites, such as Paypal.com or Qiwi.com.
SorterX, on the other hand, is advertised in the underground as a tool for faster credential-logs processing. However, the tool only supports a number of log formats, and its analyzed folder only contains uncompressed files in subfolders. The version that we reviewed supports log formats generated by AZORult, Predator, Krot, and Smoke malware families. It should be noted that other malware families might adapt some of the widely used formats (such as AZORult’s) and could be supported by this tool as well.
Figure 12. An underground forum member posts about SorterX, a tool that can be used for the faster processing of credential logs.
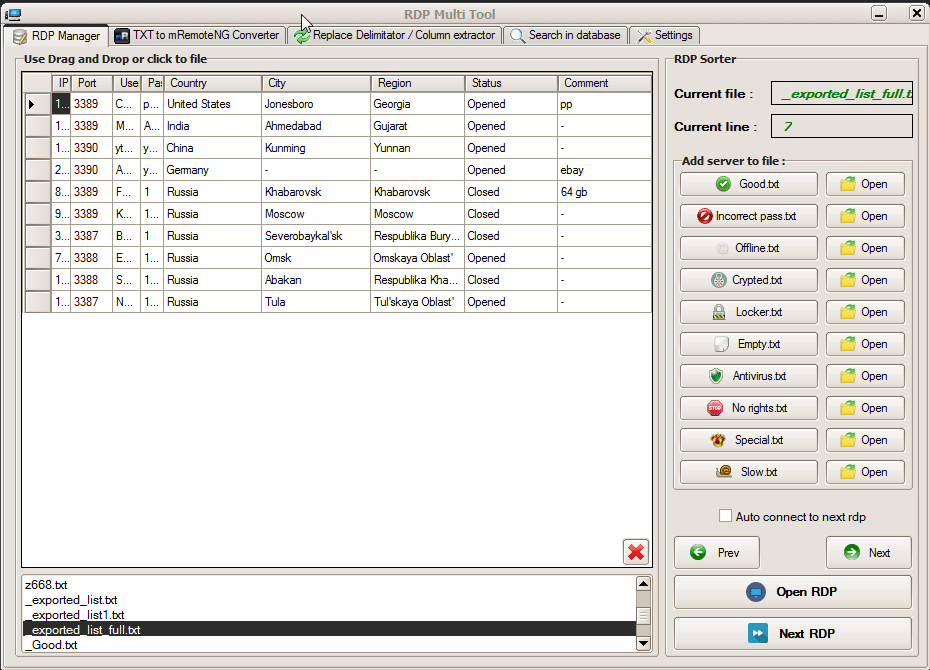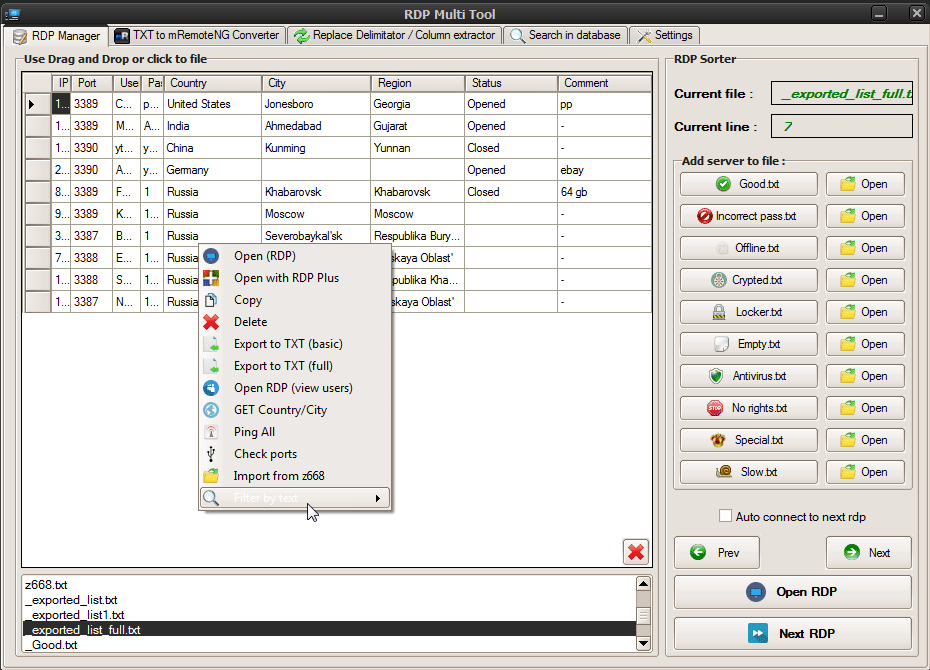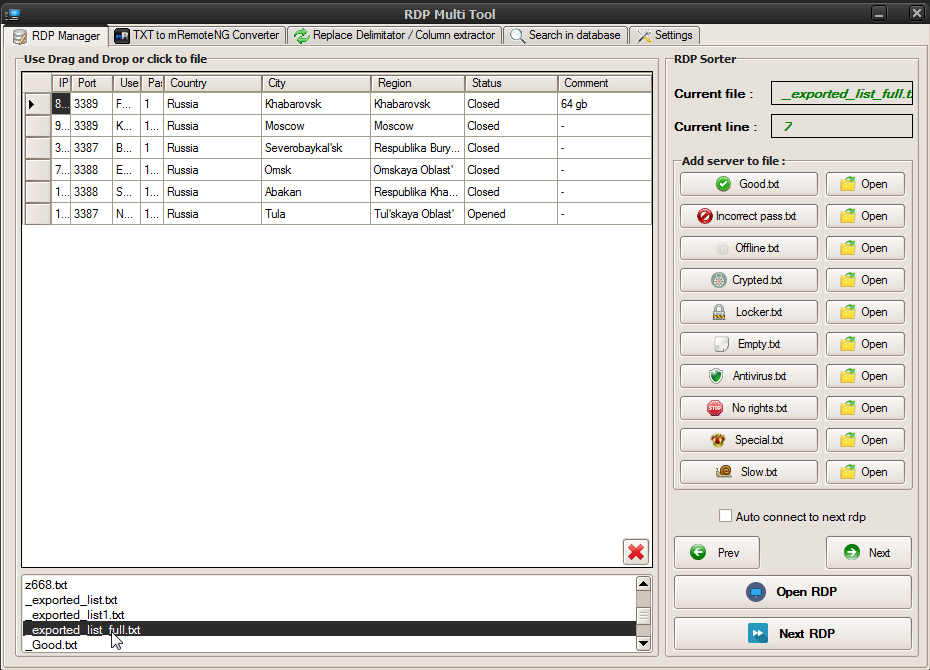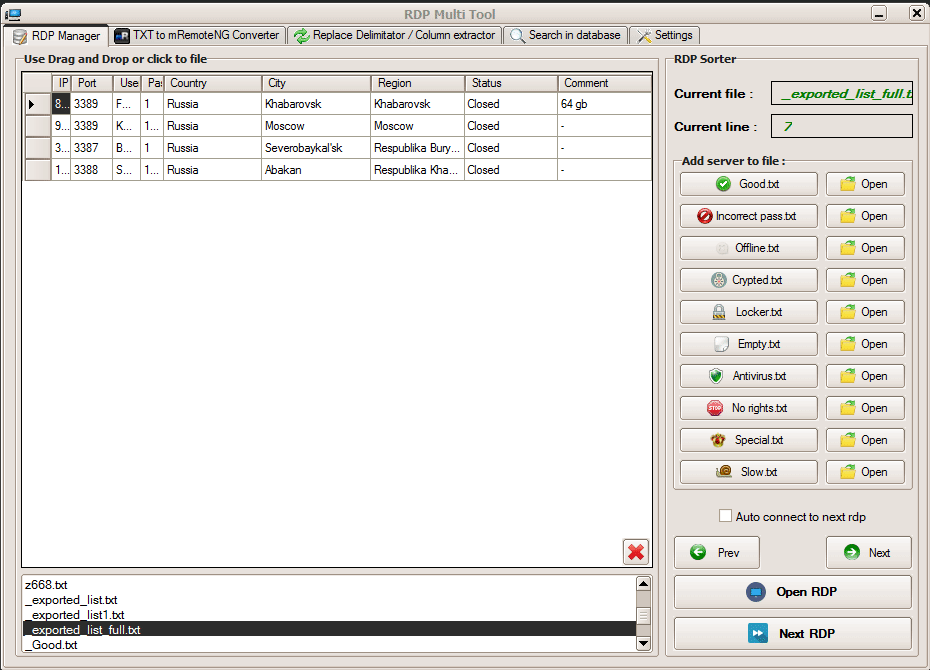
In underground forums, we also saw a tool that is advertised as capable of importing RDP credentials in .txt format and automating routine tasks for further monetization, including input data format normalization, testing for availability of hosts, collection of the precise geolocation of a victim, credential validation, collection of host fingerprints and software environment, and fingerprinting of network parameters and open ports. RDP credentials are an attractive target for criminals because they are among the major entry points that criminals use when attacking enterprises with ransomware or exfiltrating sensitive data.
Figure 13. The interface of a software advertised as a tool for monetization of RDP credentials
Criminals are also adopting open-source tools for data mining and bulk validation processing of stolen credentials. For example, the open-source tool OpenBullet can be used to verify the validity of stolen credentials. In one of the forum posts that we saw, a user shared that this tool with custom configuration runs checks of stolen credentials from the cloud-gaming platform, Vortex.GG.
Another popular tool is AZORult Analyzer. The name of the tool is revelatory of its purpose: the analysis of AZORult malware logs. The AZORult malware is capable of stealing cookies, browsing history, cookies, ID/passwords, cryptocurrency information, and more.
Indeed, the availability of the aforementioned tools could enable criminals to improve the scale of their operations. By being able to quickly find the data that they need, criminals can conveniently proceed to the subsequent attacks that they might deploy.
The abuse of cloud to scale criminal operations
Cloud services and technologies enable businesses to be more agile, scalable, and cost-effective. The business of selling access to a cloud of logs does the same, but for cybercrime.
The cloud has equipped illegal businesses operated by criminals with the capability to effectively manage massive datasets and deliver services. By using cloud platforms, criminals are provided with the technology to efficiently mine, process, and host massive amounts of stolen data. As a result of having such stolen, valuable data, they can then conduct their attacks with increased speed when targeting organizations. Furthermore, with the growing business of selling access to stolen, valuable information and the availability of cloud-based tools to help criminals easily find the logs that they need, they are spared both the effort and the time in acquiring the critical data that is necessary for them to proceed with their malicious activities.
As a result, the gap from the time when information is stolen to the time when it is used in an attack is shorter. This could create a blind spot for organizations in particular who have a weak security posture, as they would be left with less time to detect and respond to attacks. Even worse, organizations might not be able to detect an intrusion because the use of legitimate account credentials could help criminals easily evade security solutions.
With operators who have their logs rented out to a diverse customer base of cybercriminals that specialize in different crimes, the potential for using the multitude of stolen data is further maximized for nefarious purposes. For example, some of these cybercriminals could be looking to obtain account credentials for the purpose of stealing money, while others might use these credentials to defraud online shopping sites, just to name a few.
Predictions for the cloud of logs market
With the growing business of selling access to clouds of logs, organizations could be exposed to a higher number of intrusions or compromise attempts. This is a significant possibility to consider since threat actors now have the option of choosing from a multitude of stolen data that they could use to further facilitate attacks.
As the market continues to boom, cybercriminals could be persuaded into developing various monetization schemes from the different types of data that they can steal from victims. For instance, cybercriminals could look for records of authenticated user sessions to cloud portals. If a malicious actor hijacks an active console session from a cloud service provider, they could have full control of a victim’s cloud resources. This could mean gaining access to existing cloud systems and storage. The actors could then sniff valuable data from these resources, which they could in turn exfiltrate and sell in the underground. Notably, we have already seen multiple threat actors building their business operations around this model in our previous research.
We also expect sellers to ingest more preprocessed and cleansed data into their systems in the future. We also anticipate that criminals will process and search data using cloud-native tools, as opposed to offline ones. In line with this, we foresee malicious actors developing tools powered by machine learning (ML) to speed up data extraction and analysis processes. Although we have only seen tools with limited capacities as of writing, we believe that the development of ML-powered tools — ones that can scale much larger datasets at a faster rate — is the next logical step for criminals as the market matures.
To add, we expect criminals to improve their standards by stepping away from data with depreciated value: for example, data that had already been monetized in a previous scheme. With this kind of standard for data value in place, customers will then find it easier to compare services, and standardization of prices will then follow. We believe, moreover, that this new market will give rise to a novel type of cybercriminal. In the future, these new cybercriminals will not participate in the compromise of victims or their eventual monetization. Rather, they will act as significant middlemen who, with their expertise in data mining, will produce raw, uncut gems for other criminals to polish and profit from.
In our exploration of this new underground market, we learned about the risks that organizations are likely to face should any of their valuable information be included in criminals’ clouds of logs. With criminals able to launch attacks much faster through the use of stolen data, organizations have significantly much less time to respond to such incidents. Indeed, by the time that they do spot and identify a security breach, attackers might already be reusing stolen information to gain access to the other segments of their network.
More importantly, it is worth emphasizing that it is only a matter of time before we see this new market evolve into something that could expose organizations to greater risks. Such risks could lead to even bigger financial losses, incredible reputational damage, and unprecedented operational disruption. By sharing the information that we discovered in this article, we hope that organizations gain key and novel insights into how cybercriminals are expanding their businesses and maximizing every bit of data that they steal, including the direction that their attacks could take in the future. We will continue to monitor this underground market to gather threat intelligence and coordinate with law enforcement agencies to combat malicious entities who steal, monetize, and use critical data to target organizations.
Security strategies for preventing data and system compromise
Organizations should be able to design and implement countermeasures to avoid falling prey to criminal schemes that could compromise their data and systems. To protect these, we recommend that organizations implement data-breach prevention and mitigation strategies as an integral part of their daily operations, particularly ones that could preclude criminals from compromising system accounts, which in turn could provide attackers with remote access (for example, through VPN and RDP) to organizational IT premises. The successful implementation of prevention strategies can be accomplished by establishing and strengthening security controls in order to detect intrusions that might lead to the inclusion of critical data in cybercriminal’s clouds of logs. Meanwhile, mitigation strategies should be implemented with capabilities and procedures for effective incident detection, response, and investigation.
One approach that organizations could take is implementing the principle of least privilege to control the use, assignment, and configuration of user access on computers, networks, and applications. Taking this approach could reduce the risk of malicious actors gaining access to critical systems and sensitive data.
To prevent attackers from exploiting potentially vulnerable services and settings, organizations can also establish, implement, and actively manage the security configuration of network infrastructure devices using a thorough configuration management and change control process.
Holding training and awareness programs to develop a security-conscious workforce is another key practice that organizations can follow. Through these programs, organizations can raise the bar with regard to expecting their employees to practice the desired security precautions that would allow them to effectively manage potential security threats that could come from downloading malicious apps, sharing passwords, using unsecured networks, and clicking on suspicious links, among others.
Organizations can also rely on security solutions such as Trend MicroTM XDR to prevent attackers from breaching their IT premises and stealing valuable data. XDR allows organizations to gain visibility over the entire attack life cycle, including infiltration, lateral movement, and exfiltration. This security solution provides a single platform for incident detection, mitigation, and investigation, giving organizations an attack-centric view of an entire chain of events across mail, network, endpoint, and server layers. This capability could allow organizations to prevent critical data exfiltration or the compromise of critical systems within their network.
Lastly, organizations can look into Trend Micro’s Hybrid Cloud Security solution, which provides powerful, streamlined, and automated security> within organization’s DevOps pipeline and delivers multiple XGenTM threat defense techniques for protecting runtime physical, virtual, serverless, and cloud workloads.
Hybrid Cloud Security is powered by Trend Micro Cloud OneTM, a security services platform that goes beyond traditional intrusion prevention system capabilities by including virtual patching and post-compromise detection and disruption. Cloud One - Conformity, one of the services offered by Cloud One, provides organizations with auto-remediation capabilities to automatically address high-risk violations, such as open storage access. More importantly, these capabilities can prevent malicious actors from accessing sensitive data. Through vigilance in implementing the appropriate security strategies, solutions, and training programs for their workforce, organizations can be better prepared in the face of cybercrime’s continuously evolving nature.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One