Your Bonus This Christmas is Delivered with EMOTET
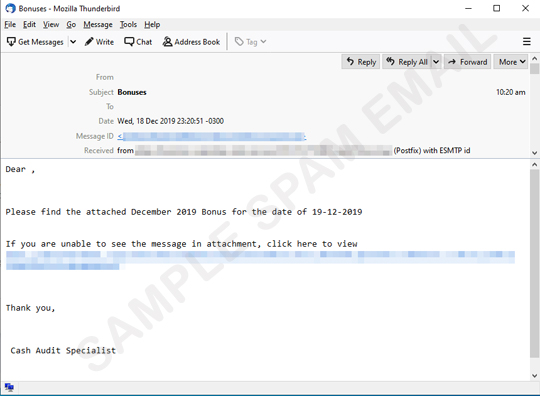
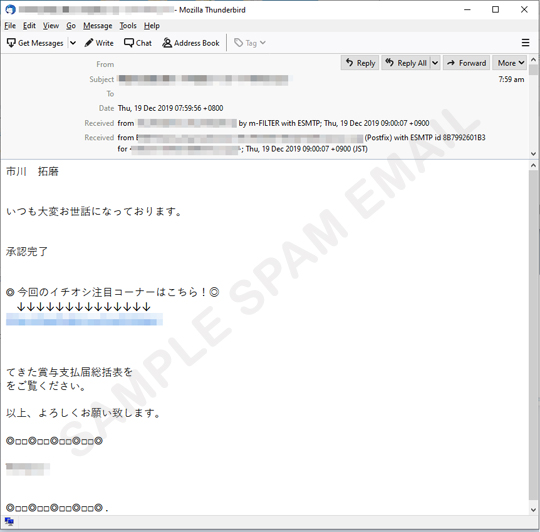
EMOTET continues to spread, using different techniques and relevant events. This December 2019, we observed the rise of malicious spam containing links or password-protected attachments bringing EMOTET. These messages tell its recipients that their Christmas bonuses are ready to be claimed. It sends an attachment or a link that tells the user to view the payout summary. It then lures the recipients into clicking the malicous links or opening the attached file. The messages are written in English or Japanese, depending on the country of the victims being spammed.
The URLs used in the spam varies widely, with some using a cloud service or a compromised website. While the links may differ, all of it downloads a malicious document file with macro.
A notable technique used by spammers is sending the malicious attachment with no mention of its password, and later on, sending the password in another email. This is done to evade detection. Inside the attachment is an encrypted archive is a document that is responsible for downloading and running EMOTET.
These malicious documents contain macros that when executed, downloads a copy of EMOTET and installs it in the victim's system. These documents are now detected by Trend Micro as Trojan.W97M.EMOTET.JKDE. To prevent system infection, we recommend users to refrain from opening unsolicited email, especially those with attachments.
- ENGINE:8.1
- PATTERN:25114